TCP Idle Scan (-sI) Nmap Network Scanning
Por um escritor misterioso
Last updated 22 dezembro 2024
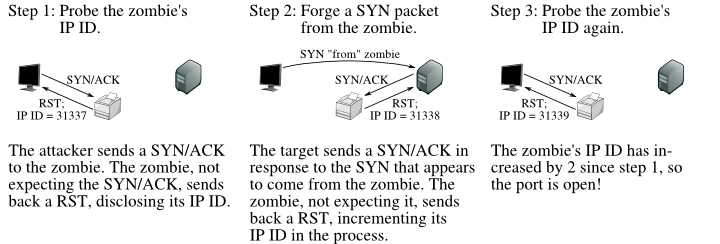

How to use NMAP command to test Server/Network Security
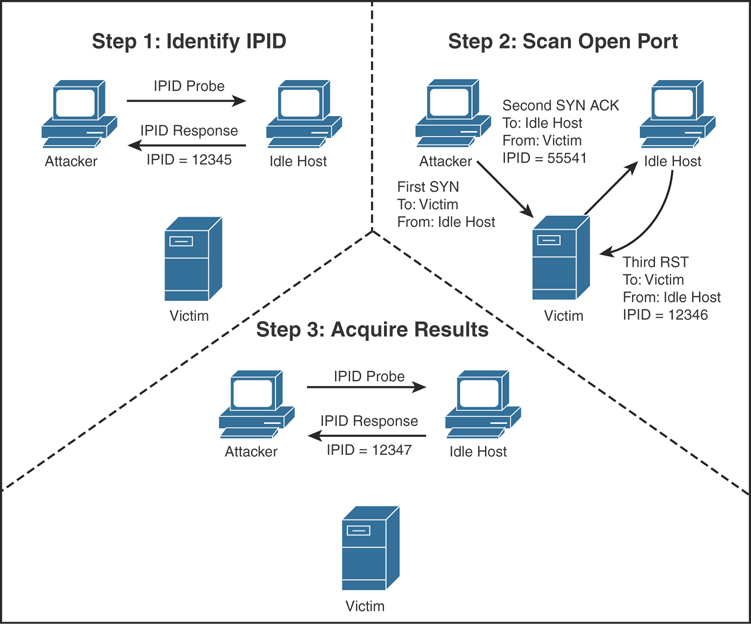
Scanning, Footprinting, Reconnaissance, and Scanning
NMAP Idle Scan

End]Network Vulnerability and Scanning: Other NMAP Scans (NULL,FIN,XMAS,ACK, IDLE), by Koay Yong Cett
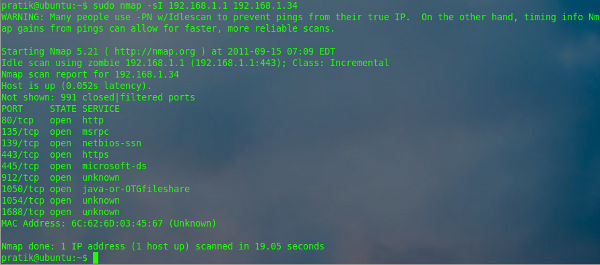
Understanding Nmap Commands: In depth Tutorial Part II

End]Network Vulnerability and Scanning: Other NMAP Scans (NULL,FIN,XMAS,ACK, IDLE), by Koay Yong Cett

Nmap Advanced Port Scans, TryHackMe (THM), by Aircon
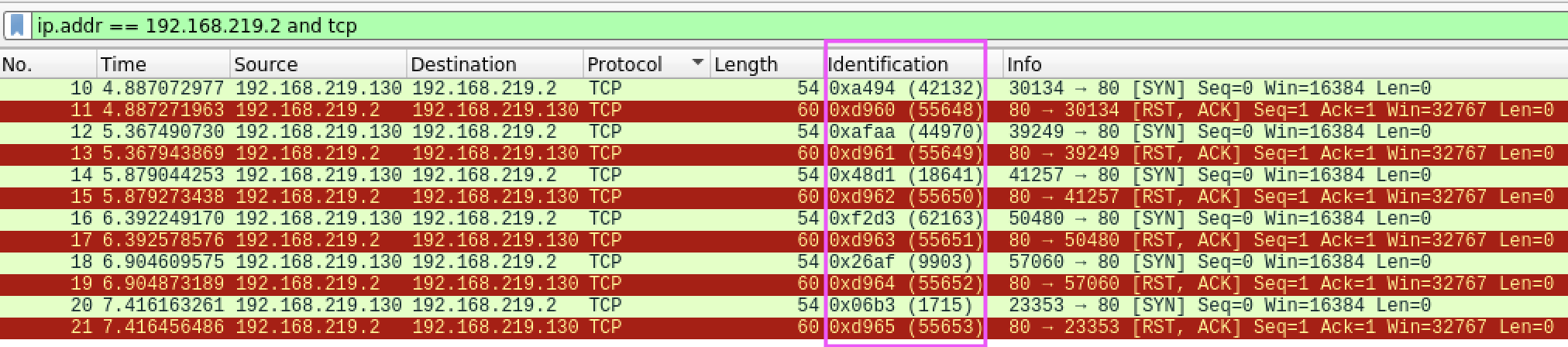
Pentesting - Nmap Stealth Scan
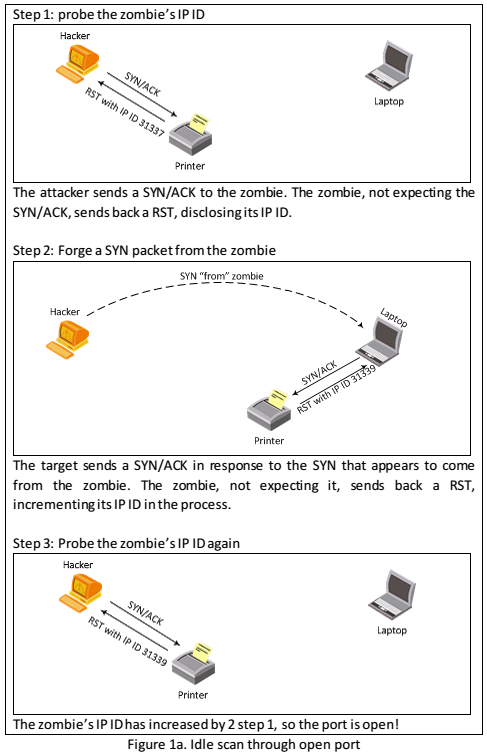
Performing Nmap Idle scan

How to Use nmap to Find Devices on Your Network - Securing Ninja

Let's find zombies with Nmap !. Note: This is for educational purposes…, by Tan
Recomendado para você
-
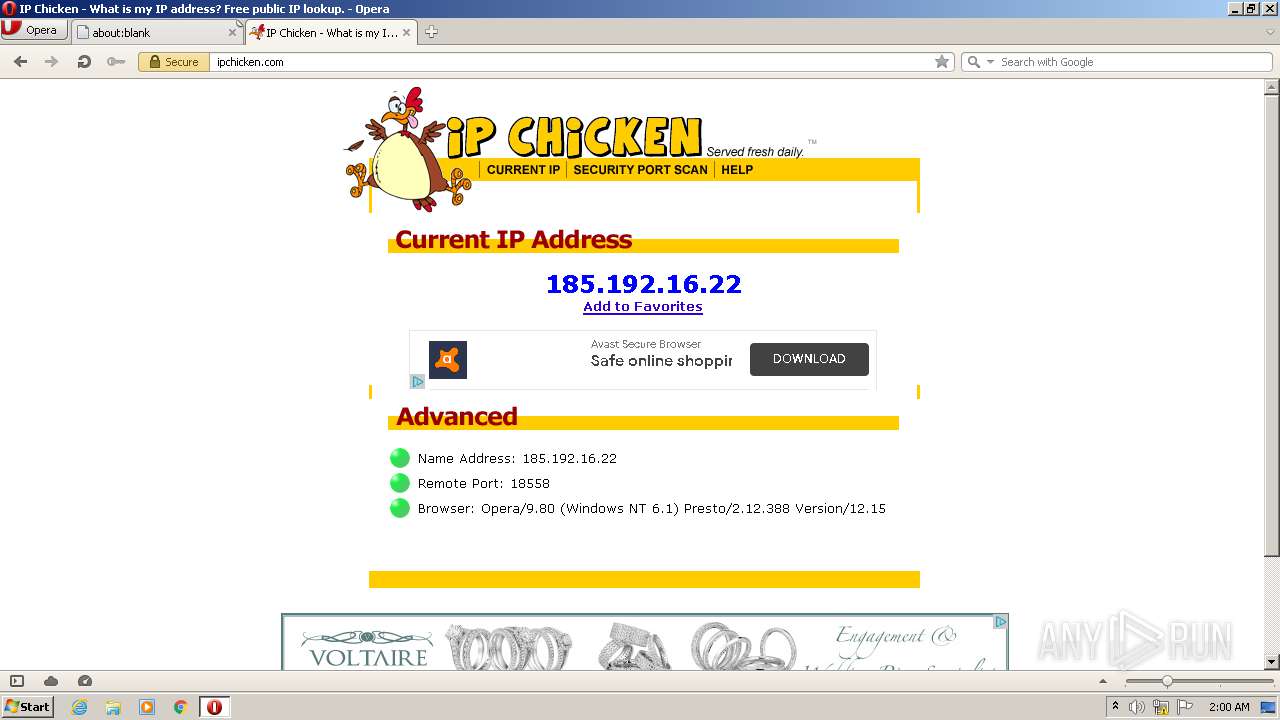
 IPChicken, Woo hoo! Lightspeed!, Richard De Guzman22 dezembro 2024
IPChicken, Woo hoo! Lightspeed!, Richard De Guzman22 dezembro 2024 -
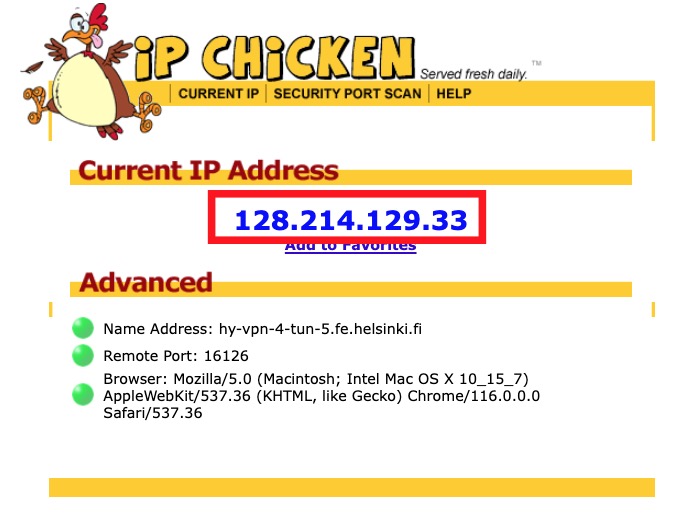 HY-VPN – Checking functionality and errors (Linux)22 dezembro 2024
HY-VPN – Checking functionality and errors (Linux)22 dezembro 2024 -
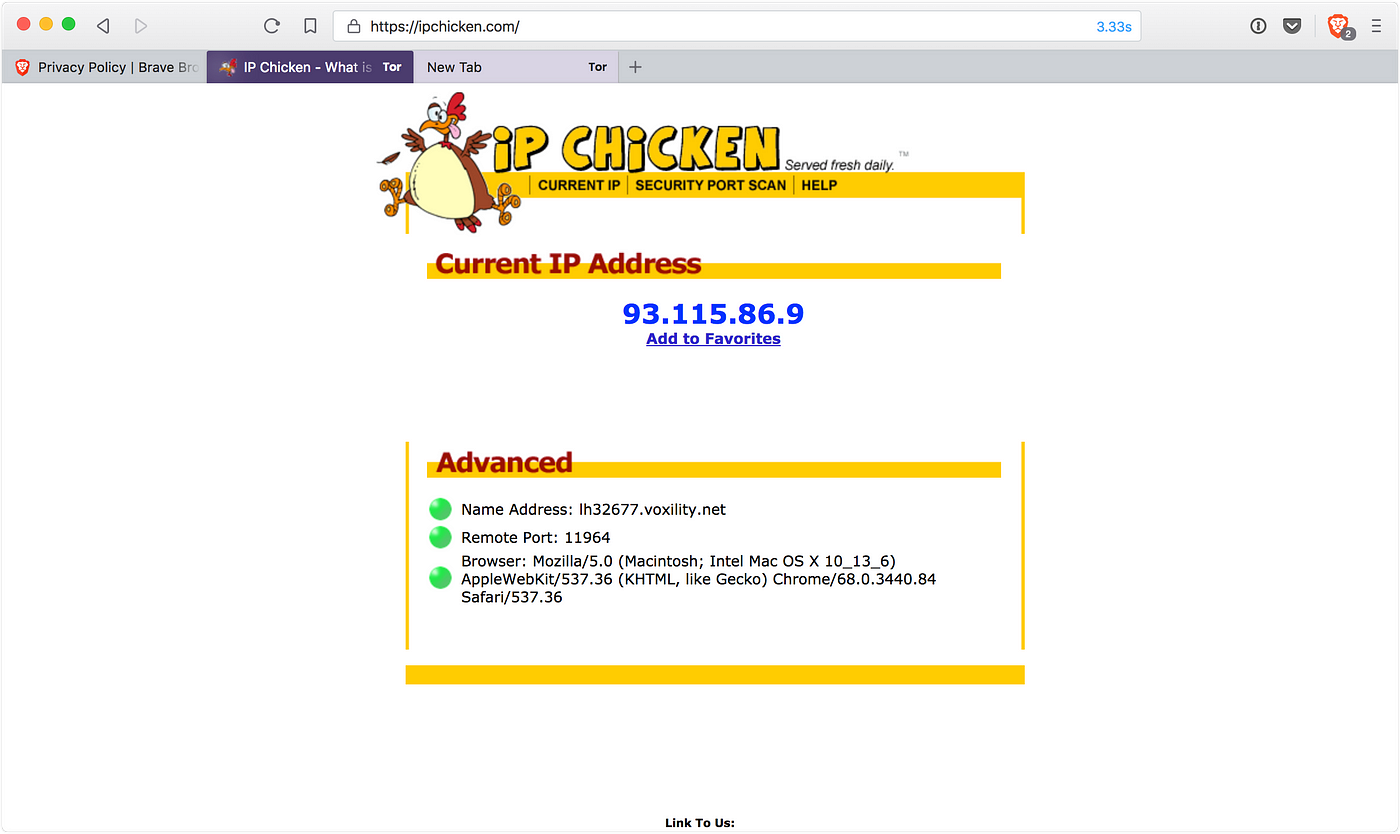 Using a truly private browser — Brave, by Dave Smith22 dezembro 2024
Using a truly private browser — Brave, by Dave Smith22 dezembro 2024 -
 Xfinity won't add as sourceNot In Subscription - TV Everywhere - Channels Community22 dezembro 2024
Xfinity won't add as sourceNot In Subscription - TV Everywhere - Channels Community22 dezembro 2024 -
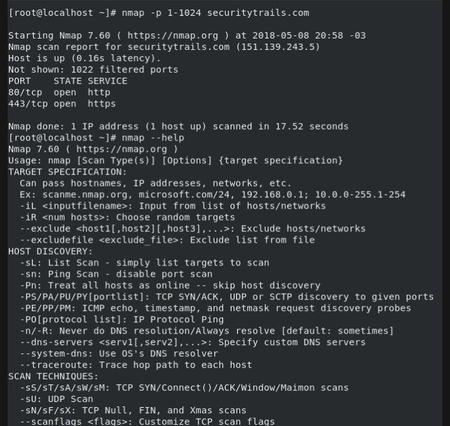 Top 5 Most Popular Port Scanners in CyberSecurity22 dezembro 2024
Top 5 Most Popular Port Scanners in CyberSecurity22 dezembro 2024 -
 Malware analysis Malicious activity22 dezembro 2024
Malware analysis Malicious activity22 dezembro 2024 -
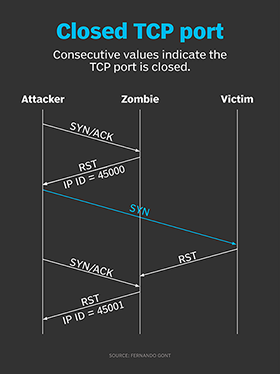 How hackers use idle scans in port scan attacks22 dezembro 2024
How hackers use idle scans in port scan attacks22 dezembro 2024 -
 Alt using troll awareness meme - Imgflip22 dezembro 2024
Alt using troll awareness meme - Imgflip22 dezembro 2024 -
 Hacking Package Pickup22 dezembro 2024
Hacking Package Pickup22 dezembro 2024 -
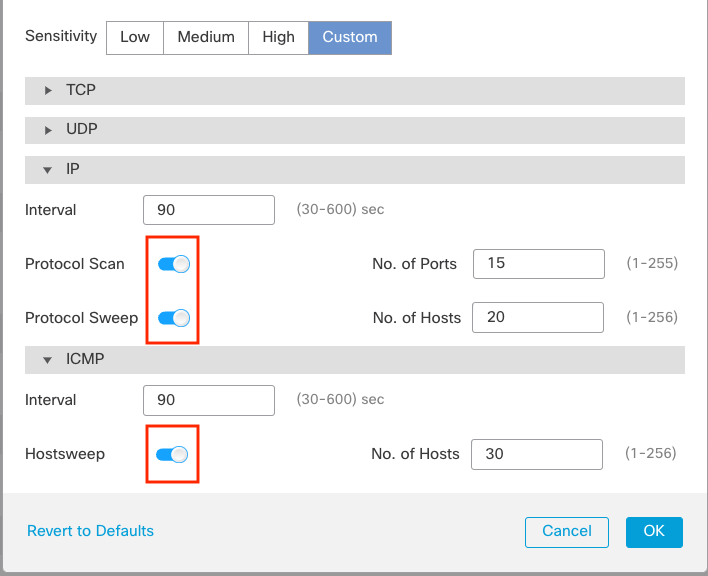 Port Scan Detection22 dezembro 2024
Port Scan Detection22 dezembro 2024
você pode gostar
-
 Create meme hair , hair roblox, roblox hair for girls - Pictures22 dezembro 2024
Create meme hair , hair roblox, roblox hair for girls - Pictures22 dezembro 2024 -
 The Mona Lisa in virtual reality in your own home22 dezembro 2024
The Mona Lisa in virtual reality in your own home22 dezembro 2024 -
Sudoku Solver - A Visualizer made using Backtracking Algorithm - CodeNewbie Community 🌱22 dezembro 2024
-
 Kit Para Agachamento Sumô Com Barra Reta Fixa 50cm22 dezembro 2024
Kit Para Agachamento Sumô Com Barra Reta Fixa 50cm22 dezembro 2024 -
Em John Wick, tudo começa e termina com os cães. Conheça as estrelas da saga – PiT22 dezembro 2024
-
 JoJo's Bizarre Adventure: Part 1--Phantom Blood, Vol. 1 (1)22 dezembro 2024
JoJo's Bizarre Adventure: Part 1--Phantom Blood, Vol. 1 (1)22 dezembro 2024 -
 Sirloin & Sherry Shallot Sauce Recipe22 dezembro 2024
Sirloin & Sherry Shallot Sauce Recipe22 dezembro 2024 -
 Bari Bari GIF - Bari Bari - Discover & Share GIFs22 dezembro 2024
Bari Bari GIF - Bari Bari - Discover & Share GIFs22 dezembro 2024 -
 Mickey Mouse - Incredible Characters Wiki22 dezembro 2024
Mickey Mouse - Incredible Characters Wiki22 dezembro 2024 -
 Pou Gameplay jogar POU na terça-feira #2922 dezembro 2024
Pou Gameplay jogar POU na terça-feira #2922 dezembro 2024
