How hackers use idle scans in port scan attacks
Por um escritor misterioso
Last updated 22 dezembro 2024
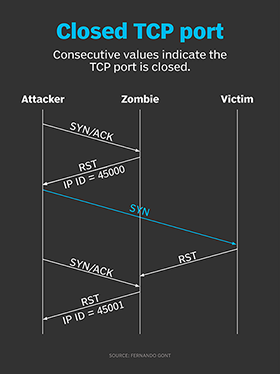
Hackers employ a variety of port scan attacks to gain entry into an enterprise network. Idle scans are a popular method to mask the hacker
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.

Nmap cheat sheet: From discovery to exploits, part 2: Advance port scanning with Nmap and custom idle scan

Hacking techniques

How to hide yourself using Idle scan (-sl) - Port scanning tutorial
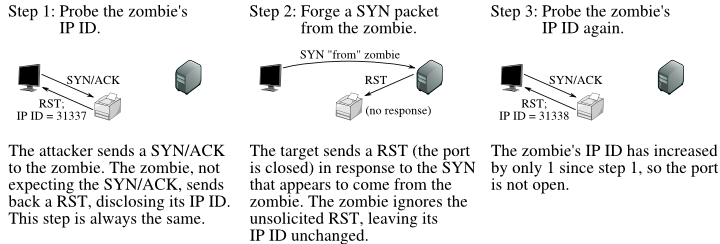
TCP Idle Scan (-sI) Nmap Network Scanning
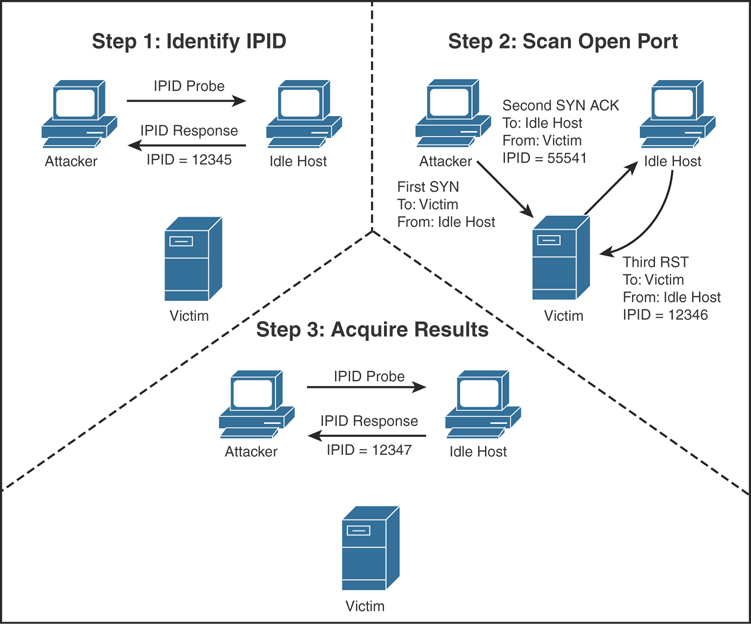
Scanning, Footprinting, Reconnaissance, and Scanning
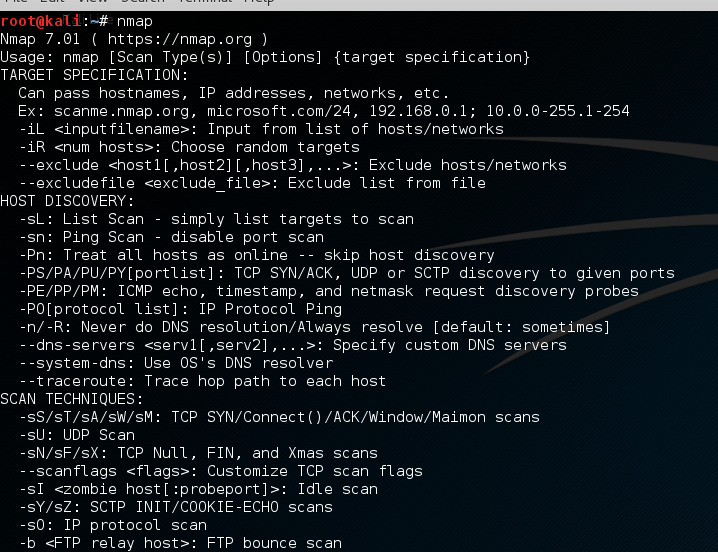
Applied Network Security

Port Scanning Tutorial for Hackers - Basics

PPT - Port Scanning PowerPoint Presentation, free download - ID:1577632
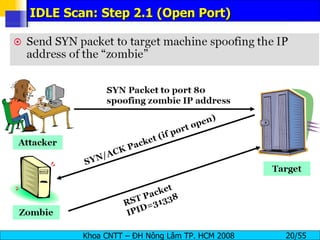
Module 3 Scanning
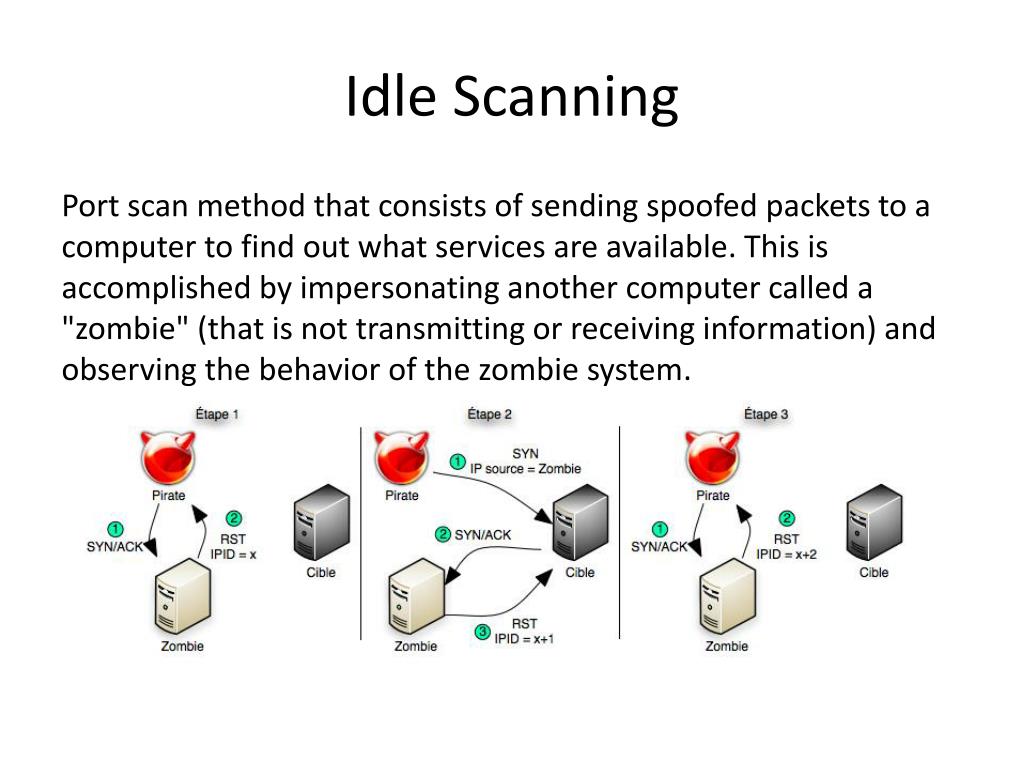
PPT - Port Scanning PowerPoint Presentation, free download - ID:1577632

NMAP by Shrikant Antre & Shobhit Gautam
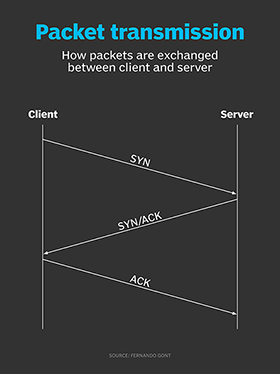
How hackers use idle scans in port scan attacks
Recomendado para você
-
 Setup OrthoInTouch with topsOrtho - OrthoInTouch - Appointment Reminders22 dezembro 2024
Setup OrthoInTouch with topsOrtho - OrthoInTouch - Appointment Reminders22 dezembro 2024 -
 The Fuck you Tony P Guide to getting around an IP ban!22 dezembro 2024
The Fuck you Tony P Guide to getting around an IP ban!22 dezembro 2024 -
![Question] How to get around VPN blockers?](https://i.gyazo.com/f0c5d0d5b114f0d49954a16dd5112ac7.png) Question] How to get around VPN blockers?22 dezembro 2024
Question] How to get around VPN blockers?22 dezembro 2024 -
 Xfinity won't add as sourceNot In Subscription - TV Everywhere - Channels Community22 dezembro 2024
Xfinity won't add as sourceNot In Subscription - TV Everywhere - Channels Community22 dezembro 2024 -
 Port Scan in Ethical Hacking - GeeksforGeeks22 dezembro 2024
Port Scan in Ethical Hacking - GeeksforGeeks22 dezembro 2024 -
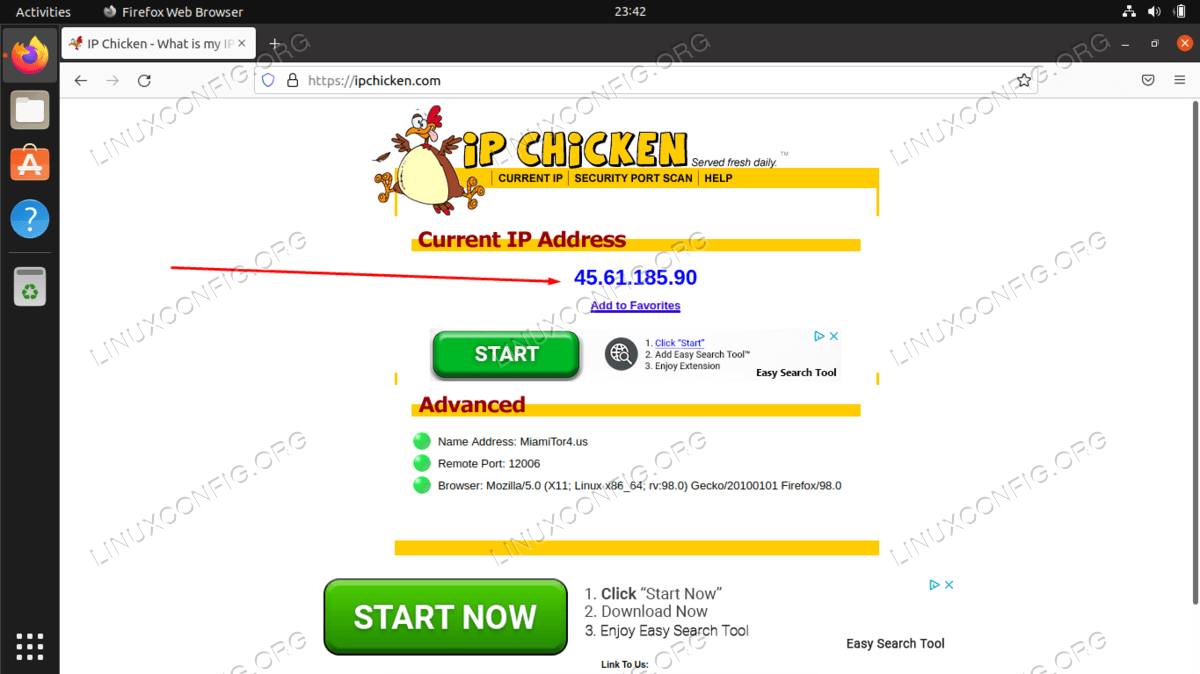 Install Tor proxy on Ubuntu 22.04 Linux - Linux Tutorials - Learn Linux Configuration22 dezembro 2024
Install Tor proxy on Ubuntu 22.04 Linux - Linux Tutorials - Learn Linux Configuration22 dezembro 2024 -
Ethical Hacking With Net22 dezembro 2024
-
Gogo's T-Mobile sponsored in-flight wifi? Free? On a PC?!22 dezembro 2024
-
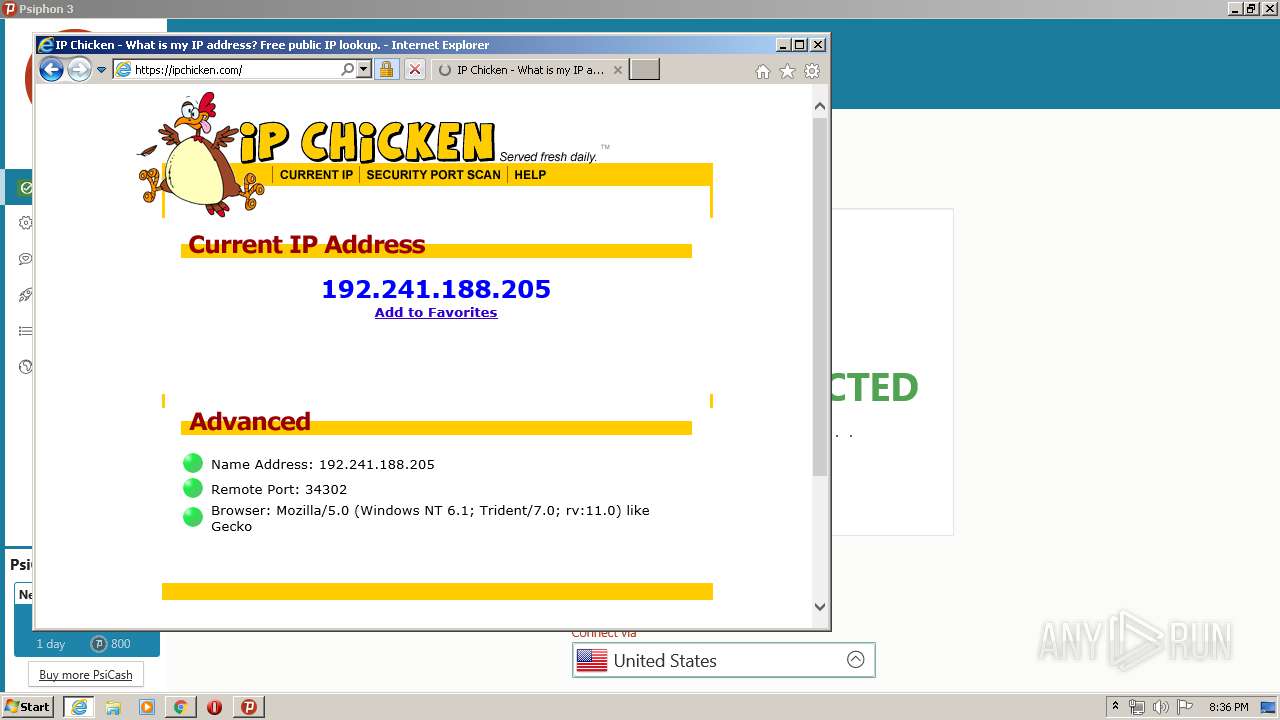 Malware analysis Malicious activity22 dezembro 2024
Malware analysis Malicious activity22 dezembro 2024 -
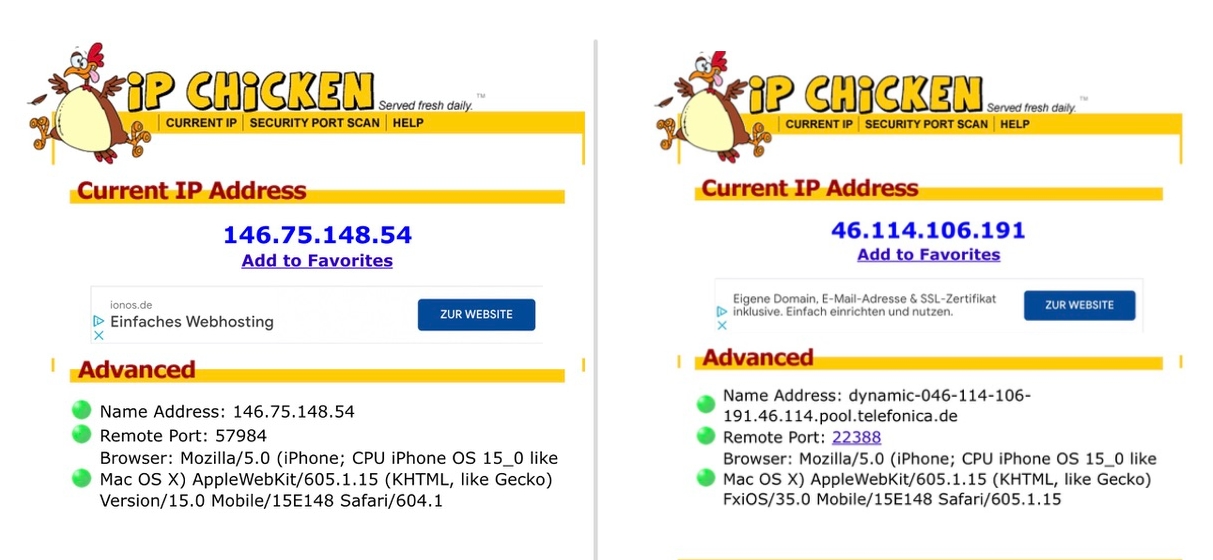 iOS 15: Hide IP address in Safari22 dezembro 2024
iOS 15: Hide IP address in Safari22 dezembro 2024
você pode gostar
-
 Pin de 𝕮𝖗𝖎𝖒𝖘𝖔𝖓 𝕻𝖆𝖎𝖒𝖔𝖓 em C S M em 202322 dezembro 2024
Pin de 𝕮𝖗𝖎𝖒𝖘𝖔𝖓 𝕻𝖆𝖎𝖒𝖔𝖓 em C S M em 202322 dezembro 2024 -
guerra de 1000 anos bleach|Pesquisa do TikTok22 dezembro 2024
-
 Anime Stand Isekai wa Smartphone to Tomo ni Linze Silhoueska Acrylic Figure Display Desktop Decoration 15cm22 dezembro 2024
Anime Stand Isekai wa Smartphone to Tomo ni Linze Silhoueska Acrylic Figure Display Desktop Decoration 15cm22 dezembro 2024 -
 Capa para Celular - GTA V, Modelo 422 dezembro 2024
Capa para Celular - GTA V, Modelo 422 dezembro 2024 -
 Wildberries снова изменил правила возврата товаров — теперь в пользу покупателей 26.06.202322 dezembro 2024
Wildberries снова изменил правила возврата товаров — теперь в пользу покупателей 26.06.202322 dezembro 2024 -
 Boneco Do Goku Ssj 422 dezembro 2024
Boneco Do Goku Ssj 422 dezembro 2024 -
 Mangá Hataraku Saibou, que retrata o que acontece dentro do corpo humano, ganha vídeo comercial - Crunchyroll Notícias22 dezembro 2024
Mangá Hataraku Saibou, que retrata o que acontece dentro do corpo humano, ganha vídeo comercial - Crunchyroll Notícias22 dezembro 2024 -
 Club Space Miami - Clubbing TV22 dezembro 2024
Club Space Miami - Clubbing TV22 dezembro 2024 -
 Olivo Jogo Tabuleiro de Xadrez - OLV00522 dezembro 2024
Olivo Jogo Tabuleiro de Xadrez - OLV00522 dezembro 2024 -
 Manga Like Tale of Fairy Tail: Ice Trail22 dezembro 2024
Manga Like Tale of Fairy Tail: Ice Trail22 dezembro 2024


