Major surge in memory-based attacks as hackers evade traditional
Por um escritor misterioso
Last updated 22 dezembro 2024

Protecting workloads with tools that understand how to interpret attacks on cloud runtime environments is crucial.

How can an attacker execute malware through a script? 2022
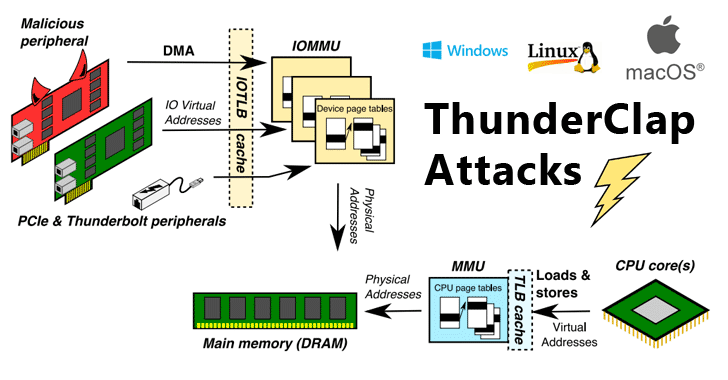
New Flaws Re-Enable DMA Attacks On Wide Range of Modern Computers

Why API attacks are increasing and how to avoid them

115 cybersecurity statistics + trends to know in 2024

Security 101: The Rise of Fileless Threats that Abuse PowerShell
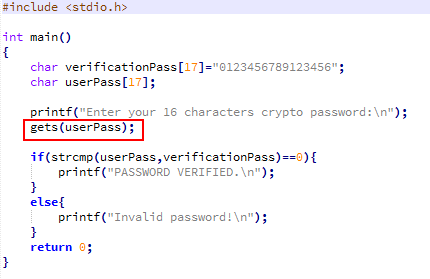
Inside the Mind of a Hacker: Attacking the Memory

100+ essential penetration testing statistics [2023 edition
“PACMAN” Hack Breaks Apple M1's Last Line of Defense - IEEE
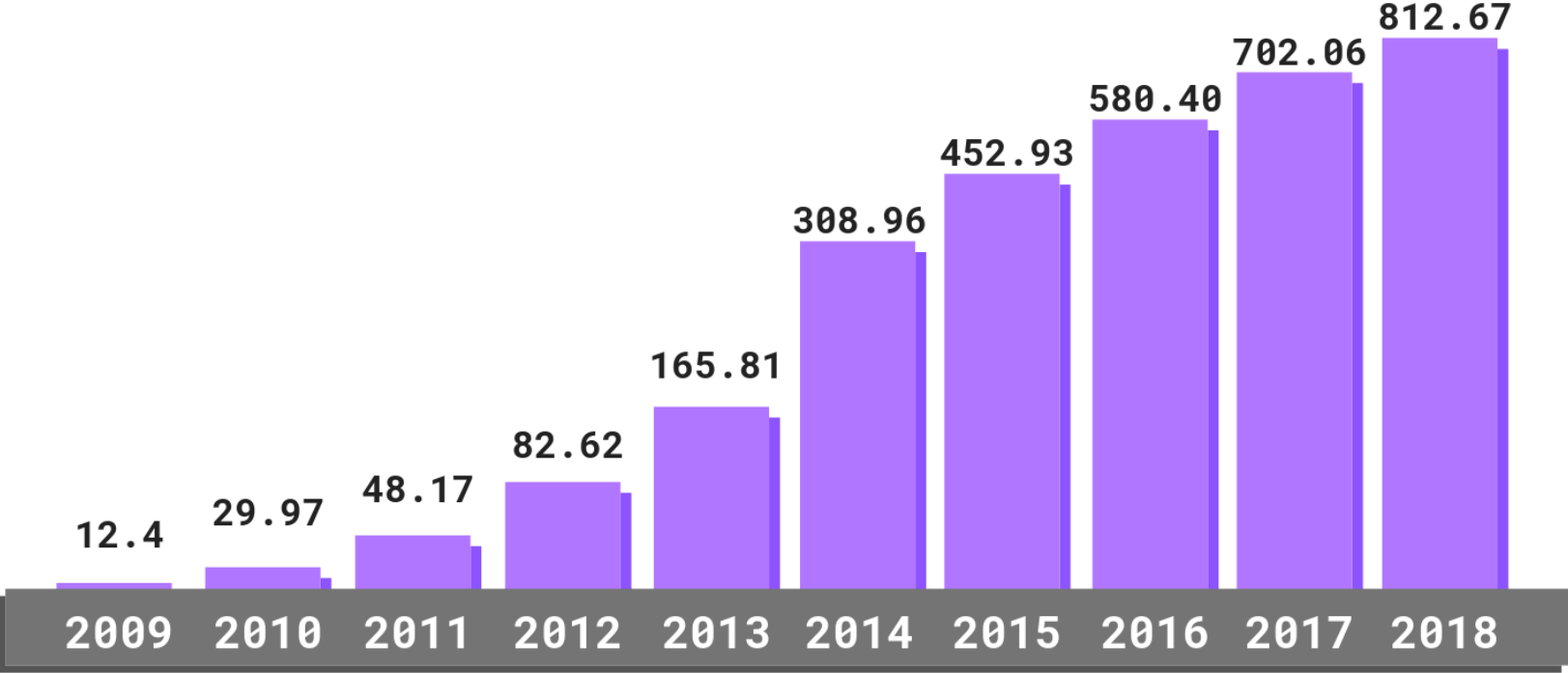
2023 Cyber Security Statistics: The Ultimate List Of Stats, Data

Exploring Prompt Injection Attacks
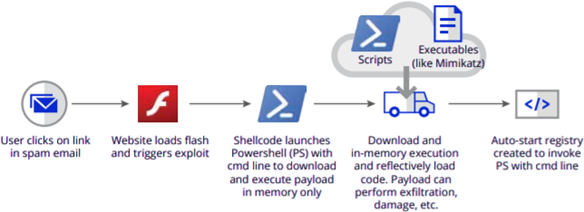
Fileless Malware Evades Detection-Based Security

Code Obfuscation: A Comprehensive Guide Against Reverse

6 Strategies That Help When Traditional Cloud Security Fails

Malware: Types, Examples, and How Modern Anti-Malware Works

Outsmarting Generative-AI Attacks: The Power of Automated Moving
Recomendado para você
-
![Evade [AutoRespawn, Esp] Scripts](https://rbxscript.com/images/-KAgv5dirUs-image.jpg) Evade [AutoRespawn, Esp] Scripts22 dezembro 2024
Evade [AutoRespawn, Esp] Scripts22 dezembro 2024 -
![Lol Hack] Script De Graça - Evade/Skillshot/Autofarm + - League Of](https://cdn.dfg.com.br/itemimages/935620138-lol-hack-script-de-graca-evade-skillshot-autofarm-TRH2.webp) Lol Hack] Script De Graça - Evade/Skillshot/Autofarm + - League Of22 dezembro 2024
Lol Hack] Script De Graça - Evade/Skillshot/Autofarm + - League Of22 dezembro 2024 -
 Evade Script Pastebin Hacks: Auto Farm, Attack, ESP & More!22 dezembro 2024
Evade Script Pastebin Hacks: Auto Farm, Attack, ESP & More!22 dezembro 2024 -
 OP) ROBLOX Evade Script - 2022, Auto Jump / ESP22 dezembro 2024
OP) ROBLOX Evade Script - 2022, Auto Jump / ESP22 dezembro 2024 -
 Python info-stealing malware uses Unicode to evade detection22 dezembro 2024
Python info-stealing malware uses Unicode to evade detection22 dezembro 2024 -
 EVADE (AUTO REVIVE) – DailyPastebin22 dezembro 2024
EVADE (AUTO REVIVE) – DailyPastebin22 dezembro 2024 -
 NEW* EVADE 🍀 HACK GUI 🔥 BEST MONEY FARM, GODMODE, FAST REVIVE22 dezembro 2024
NEW* EVADE 🍀 HACK GUI 🔥 BEST MONEY FARM, GODMODE, FAST REVIVE22 dezembro 2024 -
 Evade Halloween Ticket Autofarm22 dezembro 2024
Evade Halloween Ticket Autofarm22 dezembro 2024 -
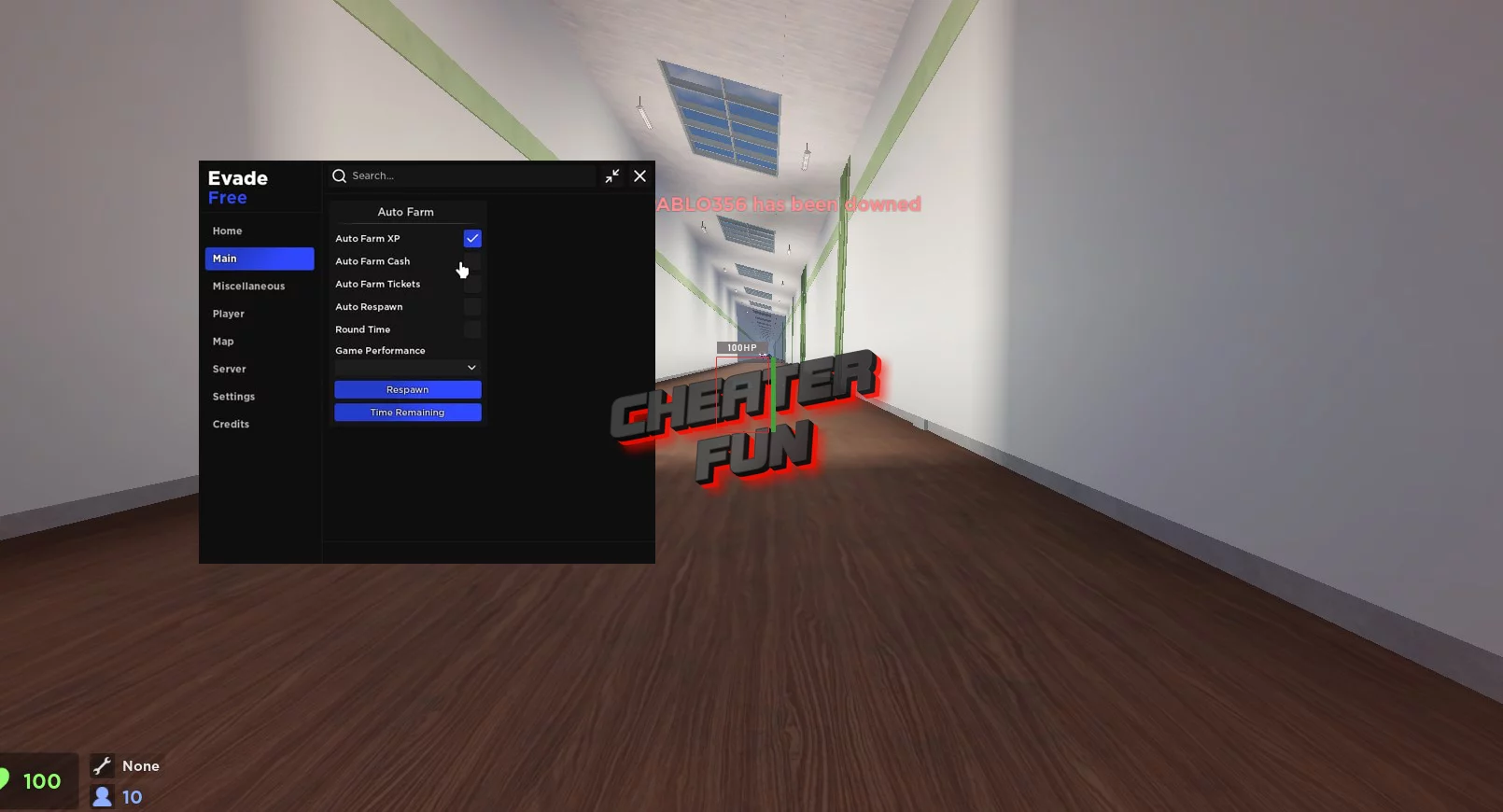 Evade Script Roblox: Auto Farm, Auto Respawn & More22 dezembro 2024
Evade Script Roblox: Auto Farm, Auto Respawn & More22 dezembro 2024 -
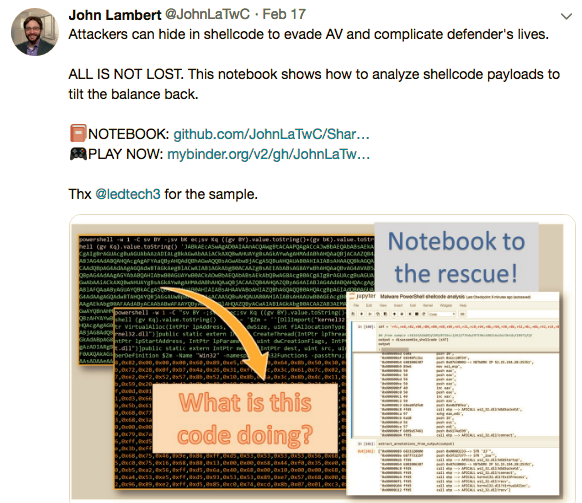 Disassemble Script22 dezembro 2024
Disassemble Script22 dezembro 2024
você pode gostar
-
 Goku base saga androides 🔯Dragon Ball Amino🔯 Amino22 dezembro 2024
Goku base saga androides 🔯Dragon Ball Amino🔯 Amino22 dezembro 2024 -
Conheça Bob e Lary de Os Vegetais. #desenho #cristao #osvegetais #desenhocristao #criancas #criancada, By Univer Vídeo22 dezembro 2024
-
 If Minecraft was released physically on PC in 2013 (Custom Box-Art by me!) : r/Minecraft22 dezembro 2024
If Minecraft was released physically on PC in 2013 (Custom Box-Art by me!) : r/Minecraft22 dezembro 2024 -
 1001 Ultimate Mahjong22 dezembro 2024
1001 Ultimate Mahjong22 dezembro 2024 -
 Meet UNCW's 2020 Homecoming King and Queen – The Seahawk22 dezembro 2024
Meet UNCW's 2020 Homecoming King and Queen – The Seahawk22 dezembro 2024 -
Shan Records - TRAITOR - OLIVIA RODRIGO [EASY KALIMBA22 dezembro 2024
-
 37 Best Dwayne Johnson Movies - The Rock's Complete Film List22 dezembro 2024
37 Best Dwayne Johnson Movies - The Rock's Complete Film List22 dezembro 2024 -
![25 Dark Roblox Outfits!! 2022 [Ep.-2]](https://i.ytimg.com/vi/uW0Fl-jAN48/sddefault.jpg?v=62cf721e) 25 Dark Roblox Outfits!! 2022 [Ep.-2]22 dezembro 2024
25 Dark Roblox Outfits!! 2022 [Ep.-2]22 dezembro 2024 -
 Shopping Mall Parking Driving Simulator - Real Car Racing Test Sim Run Race Games - MFi Games22 dezembro 2024
Shopping Mall Parking Driving Simulator - Real Car Racing Test Sim Run Race Games - MFi Games22 dezembro 2024 -
 Super Mario Bros 1.2.5- Download for Android22 dezembro 2024
Super Mario Bros 1.2.5- Download for Android22 dezembro 2024

