Kung fu enumeration. Data collection in attacked systems – HackMag
Por um escritor misterioso
Last updated 22 dezembro 2024
Find out if you have what it takes to keep the bad guys out of your network. This real-world resource contains 20+ hacking challenges for you to

Hacker's Challenge : Test Your Incident Response Skills Using 20 Scenarios
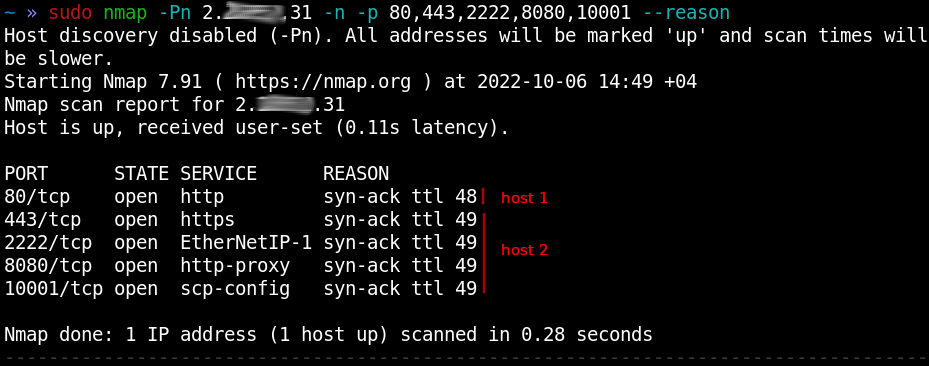
Kung fu enumeration. Data collection in attacked systems – HackMag
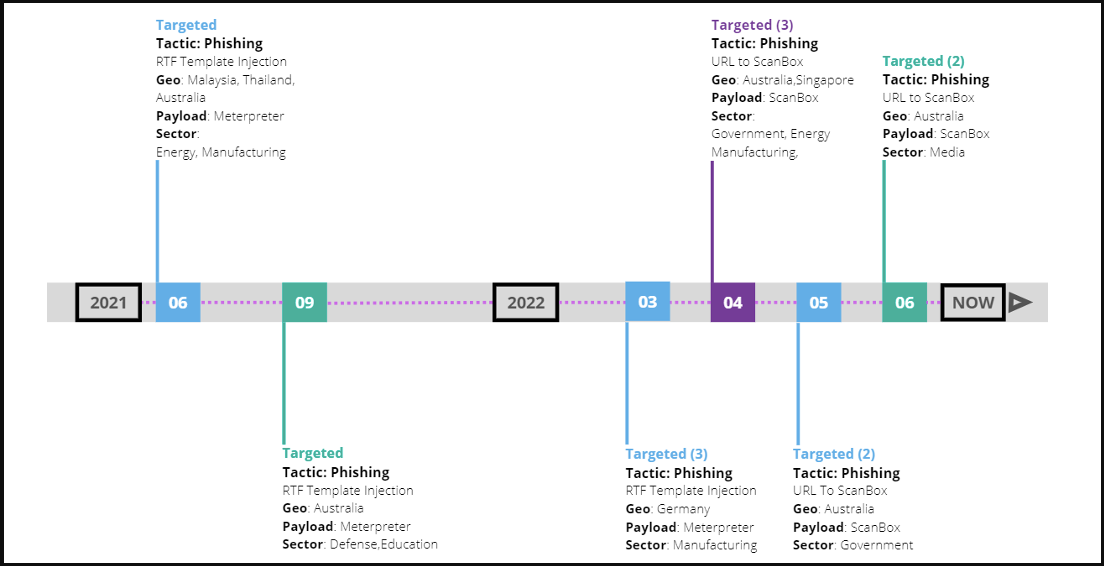
Chinese hackers target Australian govt with ScanBox malware

Subterfuge (Man-in-the-Middle Attack Framework) - Hacking Articles

08 - Attacker's Methodology

Counter Hack Reloaded: A Step-by-Step Guide to Computer Attacks

Interview with one of the world's best competitive bug hunters
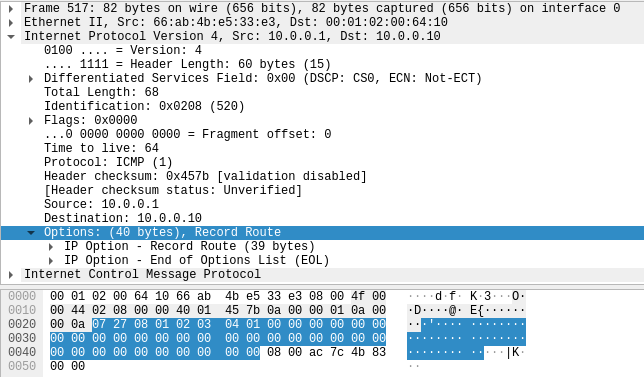
Kung fu enumeration. Data collection in attacked systems – HackMag
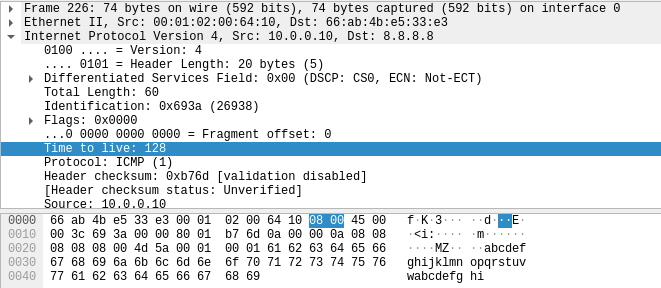
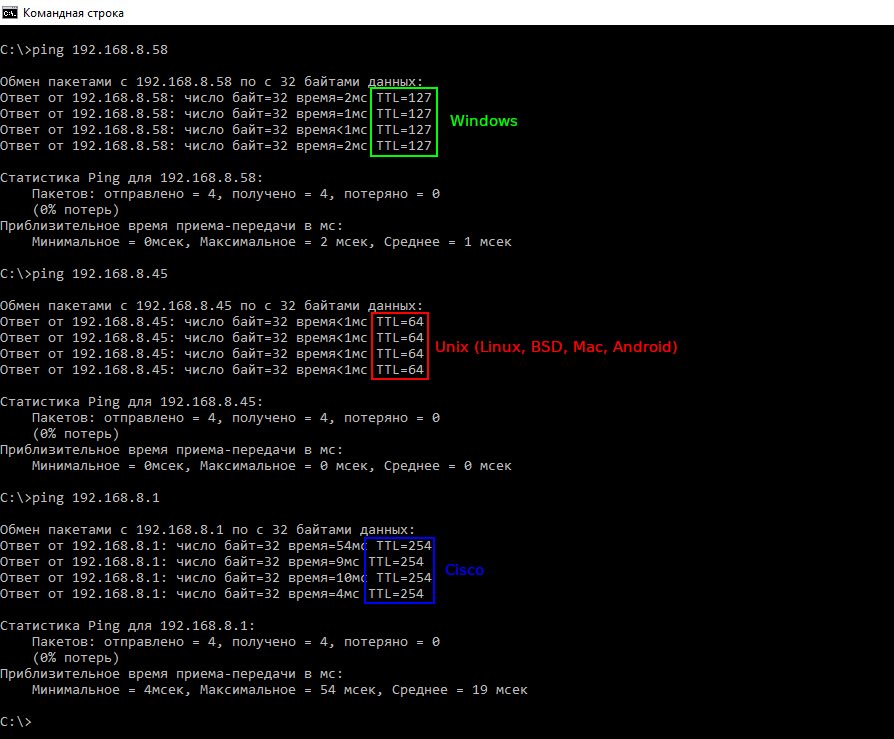
Kung fu enumeration. Data collection in attacked systems – HackMag
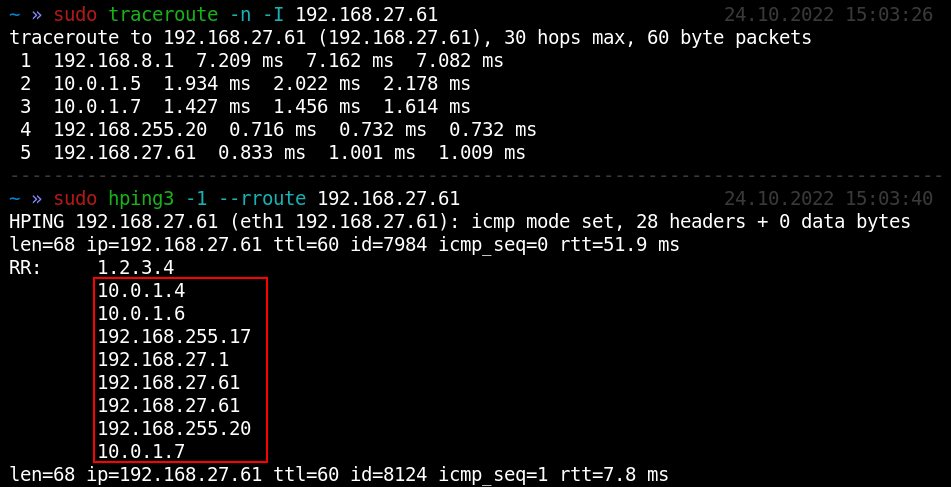
Kung fu enumeration. Data collection in attacked systems – HackMag

Hammond - Unit 17 Homework - GoodSecurity Penetration Test
Recomendado para você
-
 SCP 10001: The Ancient Behemoth, SCP Fanon Wiki22 dezembro 2024
SCP 10001: The Ancient Behemoth, SCP Fanon Wiki22 dezembro 2024 -
 SCP-10001-EX Niko, Wiki22 dezembro 2024
SCP-10001-EX Niko, Wiki22 dezembro 2024 -
 Monster22 dezembro 2024
Monster22 dezembro 2024 -
Mummy Ana!! Yay for spooky season 😭🍂! #overwatchfanart22 dezembro 2024
-
 Elastos Info - Manifesto22 dezembro 2024
Elastos Info - Manifesto22 dezembro 2024 -
 Hacker breaches security firm in act of revenge22 dezembro 2024
Hacker breaches security firm in act of revenge22 dezembro 2024 -
 Marliese Scheller - Summer Solstice: Luminescence Jun 3 - Jun 24, 2022 - Agora Gallery22 dezembro 2024
Marliese Scheller - Summer Solstice: Luminescence Jun 3 - Jun 24, 2022 - Agora Gallery22 dezembro 2024 -
 Game Jolt - Share your creations22 dezembro 2024
Game Jolt - Share your creations22 dezembro 2024 -
SCP-10001 : 3/8 Economy Printing LanyardsSilk Screen Prinitng-Bu Shang Enterprise Co., Ltd.22 dezembro 2024
-
 UGM1-SCP Complete 6 sets SUPER DRAGON BALL HEROES Card Japanese22 dezembro 2024
UGM1-SCP Complete 6 sets SUPER DRAGON BALL HEROES Card Japanese22 dezembro 2024
você pode gostar
-
 Recado : Jorge Di Sáh: Música Digital22 dezembro 2024
Recado : Jorge Di Sáh: Música Digital22 dezembro 2024 -
 PSA 10 Gem Mint Deoxys VSTAR 223/172 Vstar Universe Alt Art 202222 dezembro 2024
PSA 10 Gem Mint Deoxys VSTAR 223/172 Vstar Universe Alt Art 202222 dezembro 2024 -
 Por que GM caiu e viu Fiat assumir liderança do mercado de carros no Brasil22 dezembro 2024
Por que GM caiu e viu Fiat assumir liderança do mercado de carros no Brasil22 dezembro 2024 -
 Shaymin, Non-alien Creatures Wiki22 dezembro 2024
Shaymin, Non-alien Creatures Wiki22 dezembro 2024 -
 Play Stumble Guys Online for Free on PC & Mobile22 dezembro 2024
Play Stumble Guys Online for Free on PC & Mobile22 dezembro 2024 -
Release] Pokémon SuMoCheatMenu [supports o3DS]22 dezembro 2024
-
 Godzilla VS Wither Storm - Part 4?22 dezembro 2024
Godzilla VS Wither Storm - Part 4?22 dezembro 2024 -
 Quadro Decorativo Contra Konami Nintendo Nes 30x42cm A322 dezembro 2024
Quadro Decorativo Contra Konami Nintendo Nes 30x42cm A322 dezembro 2024 -
 Roma CF - Fiorentina (U19) 0-3 - SportReporter22 dezembro 2024
Roma CF - Fiorentina (U19) 0-3 - SportReporter22 dezembro 2024 -
 Basquetebol Fanático - Download do APK para Android22 dezembro 2024
Basquetebol Fanático - Download do APK para Android22 dezembro 2024
