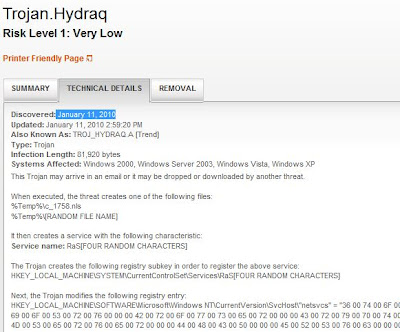
contagio: Trojan.Hydraq detection and naming
Por um escritor misterioso
Last updated 23 outubro 2024

Surveillance Capitalism or Democracy? The Death Match of Institutional Orders and the Politics of Knowledge in Our Information Civilization - Shoshana Zuboff, 2022
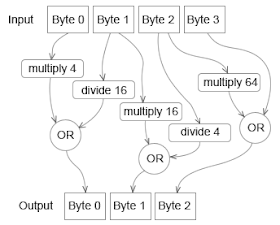
ThreatExpert Blog: Trojan.Hydraq - Part II
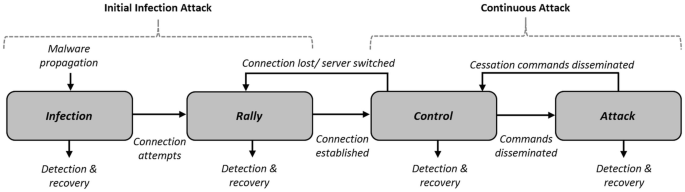
Botnet-Based Attacks and Defence Mechanisms

Cuidado: Uma mensagem de caractere único pode bloquear qualquer Apple iPhone, iPad ou Mac
PDF) A Review of State-of-the-Art Malware Attack Trends and Defense Mechanisms

Malware Dr. Tyler Bletsch - ppt download

Malware Dr. Tyler Bletsch - ppt download
Cyble — A New variant of Hydra Banking Trojan Targeting European Banking Users

Mal-Detect: An intelligent visualization approach for malware detection - ScienceDirect
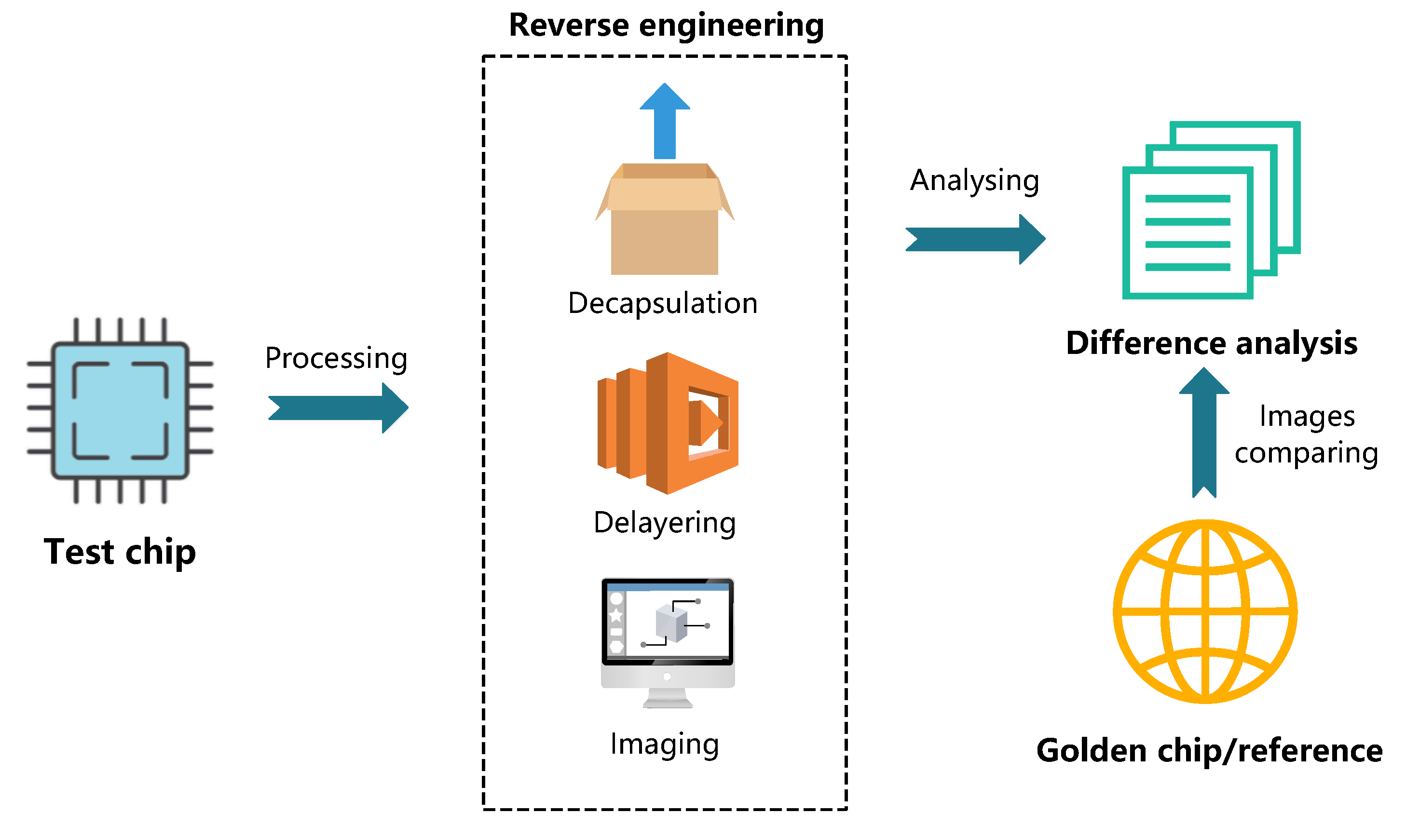
Sensors, Free Full-Text

Fiction, 9/11, and the Sleeper Agent

Trojan:Win32/Wacatac.B!ml & Trojan:Script/Wacatac.B!ml detected by Windows Security : r/computerviruses

Botnet-Based Attacks and Defence Mechanisms
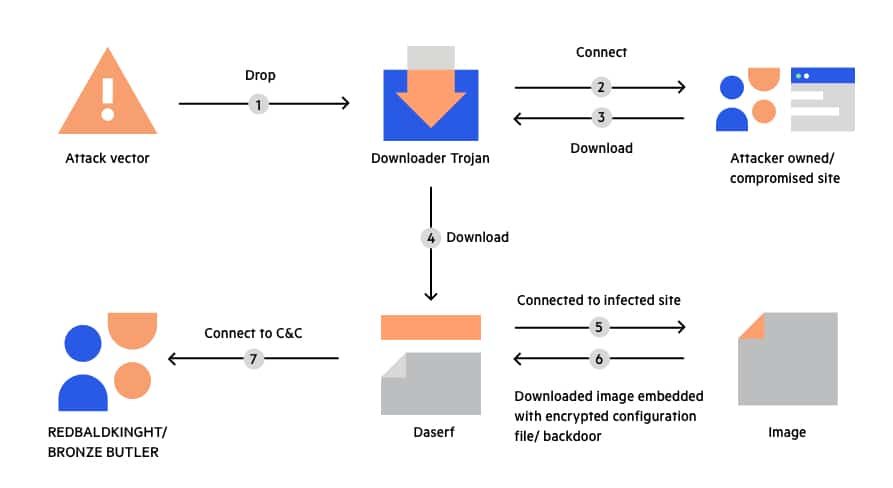
What is a Trojan Virus, Trojan Horse Malware
Recomendado para você
-
Ikarus antivirus detects this as a Trojan.Win64.CoinMiner · Issue #1620 · baldurk/renderdoc · GitHub23 outubro 2024
-
 Virus signature of specimens assigned by Ikarus23 outubro 2024
Virus signature of specimens assigned by Ikarus23 outubro 2024 -
 Ikarus Mobile Antivirus - Android Malware,Trojan,Virus Detection Test , Video23 outubro 2024
Ikarus Mobile Antivirus - Android Malware,Trojan,Virus Detection Test , Video23 outubro 2024 -
 Has Anyone Seen a Missing Scroll Bar? Phony Flash Update Redirects to Malware23 outubro 2024
Has Anyone Seen a Missing Scroll Bar? Phony Flash Update Redirects to Malware23 outubro 2024 -
 Analysis results for wget.exe on two different dates.23 outubro 2024
Analysis results for wget.exe on two different dates.23 outubro 2024 -
 Trojan.PDF.PHISH.TIAOOHQI - Threat Encyclopedia23 outubro 2024
Trojan.PDF.PHISH.TIAOOHQI - Threat Encyclopedia23 outubro 2024 -
![Remove Trojan:MSIL/Icarus.AI!MTB Trojan [Virus Removal]](https://malwaretips.com/blogs/wp-content/uploads/2023/02/Trojan-Virus-4.jpg) Remove Trojan:MSIL/Icarus.AI!MTB Trojan [Virus Removal]23 outubro 2024
Remove Trojan:MSIL/Icarus.AI!MTB Trojan [Virus Removal]23 outubro 2024 -
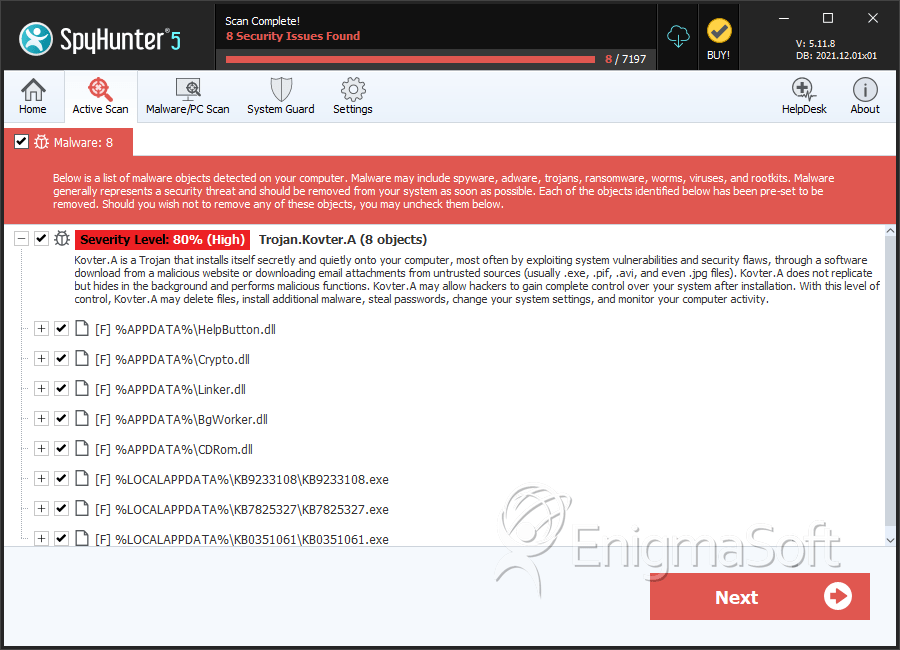 Trojan.Kovter.A Removal Report23 outubro 2024
Trojan.Kovter.A Removal Report23 outubro 2024 -
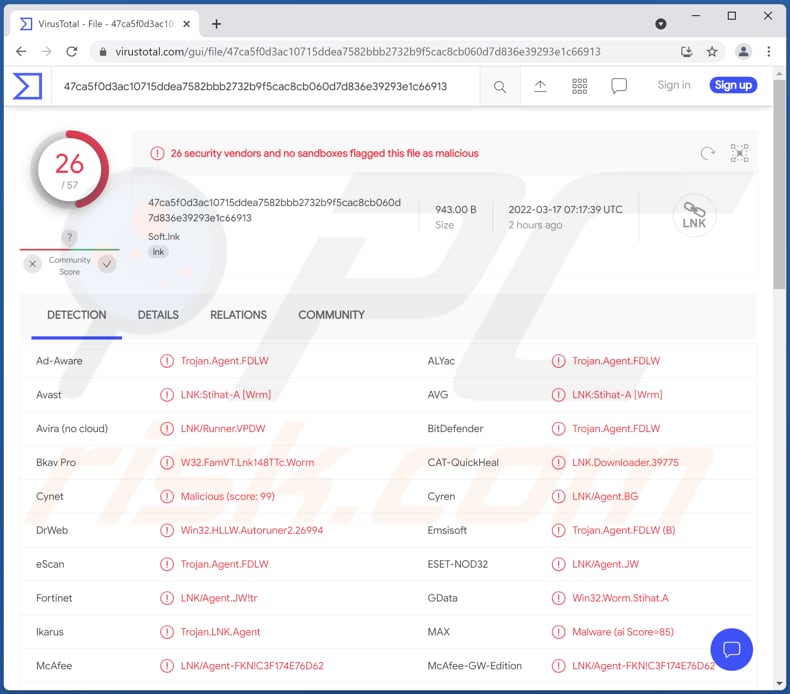 LNK/Agent Trojan - Malware removal instructions (updated)23 outubro 2024
LNK/Agent Trojan - Malware removal instructions (updated)23 outubro 2024 -
 Trojan.XF.HIDDBOOK.H - Threat Encyclopedia23 outubro 2024
Trojan.XF.HIDDBOOK.H - Threat Encyclopedia23 outubro 2024
você pode gostar
-
 Free-To-Play Battle Royale, My Hero Academia: Ultra Rumble, Announced - Game Informer23 outubro 2024
Free-To-Play Battle Royale, My Hero Academia: Ultra Rumble, Announced - Game Informer23 outubro 2024 -
 34 filmes e séries coreanas que chegam à Netflix em 2023 - Canaltech23 outubro 2024
34 filmes e séries coreanas que chegam à Netflix em 2023 - Canaltech23 outubro 2024 -
 Calaméo - jornal de Santarém, 20 a 26 de julho de 201223 outubro 2024
Calaméo - jornal de Santarém, 20 a 26 de julho de 201223 outubro 2024 -
 Genio Quiz Playstation23 outubro 2024
Genio Quiz Playstation23 outubro 2024 -
 2700lagostas23 outubro 2024
2700lagostas23 outubro 2024 -
 Summertime Rendering Volume 523 outubro 2024
Summertime Rendering Volume 523 outubro 2024 -
 Assistir Koi to Yobu ni wa Kimochi Warui Episodio 1 Online23 outubro 2024
Assistir Koi to Yobu ni wa Kimochi Warui Episodio 1 Online23 outubro 2024 -
 Dr Nowzaradan Ugly Christmas Sweater - Banantees23 outubro 2024
Dr Nowzaradan Ugly Christmas Sweater - Banantees23 outubro 2024 -
 How to Verify your Account on iPhone/iPad - Updated23 outubro 2024
How to Verify your Account on iPhone/iPad - Updated23 outubro 2024 -
 Yes Precure 5 Gogo Movie - Colaboratory23 outubro 2024
Yes Precure 5 Gogo Movie - Colaboratory23 outubro 2024