Initial access broker repurposing techniques in targeted attacks
Por um escritor misterioso
Last updated 22 dezembro 2024

Describing activities of a crime group attacking Ukraine.

Transfer Learning: Repurposing ML Algorithms from Different Domains to Cloud Defense

A WINDOW INTO RUSSIAN SPEAKING CYBERCRIME by Tim Bobak

Scraping-as-a-Service: How a Harmless Tool Became a Cyber Threat

Initial access broker repurposing techniques in targeted attacks against Ukraine

Google Says Former Conti Ransomware Members Now Attack Ukraine - Privacy Ninja

Exposing initial access broker with ties to Conti

Disk-Locking HDDCryptor/Mamba Ransomware Makes a Comeback - Security News - Trend Micro IN

Security in product lifecycle of IoT devices: A survey - ScienceDirect
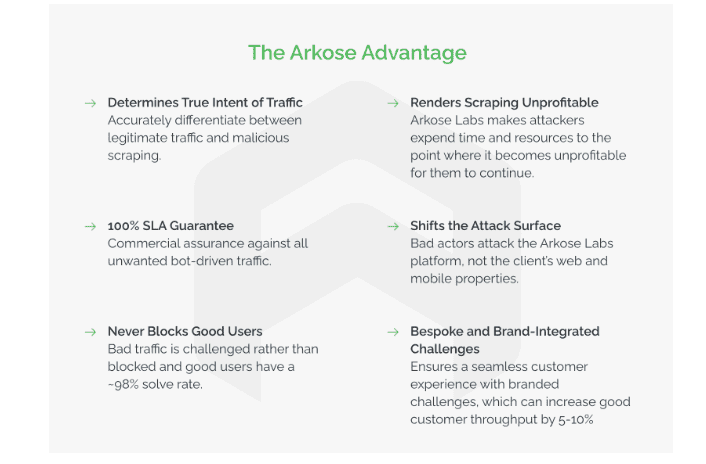
Scraping-as-a-Service: How a Harmless Tool Became a Cyber Threat

Initial Access Brokers - who are they, what do they do, and how can you protect yourself?
Recomendado para você
-
 Analysis Group Boston22 dezembro 2024
Analysis Group Boston22 dezembro 2024 -
 Analysis Group Careers and Employment22 dezembro 2024
Analysis Group Careers and Employment22 dezembro 2024 -
 Analysis Group - Crunchbase Company Profile & Funding22 dezembro 2024
Analysis Group - Crunchbase Company Profile & Funding22 dezembro 2024 -
 Analysis Group New York22 dezembro 2024
Analysis Group New York22 dezembro 2024 -
 Analysis Group Office Photos22 dezembro 2024
Analysis Group Office Photos22 dezembro 2024 -
 Careers - Analysis Group22 dezembro 2024
Careers - Analysis Group22 dezembro 2024 -
 Analysis Group - P&R Desjardins22 dezembro 2024
Analysis Group - P&R Desjardins22 dezembro 2024 -
 Home, Atmospheric Composition Analysis Group22 dezembro 2024
Home, Atmospheric Composition Analysis Group22 dezembro 2024 -
 Analysis Group's CEO on Managing with Soft Metrics22 dezembro 2024
Analysis Group's CEO on Managing with Soft Metrics22 dezembro 2024 -
 Prigozhin interests and Russian information operations22 dezembro 2024
Prigozhin interests and Russian information operations22 dezembro 2024
você pode gostar
-
high bun hair (blonde) Roblox Item - Rolimon's22 dezembro 2024
-
 Kidscreen » Archive » Scholastic and Gaumont team up for Rocket Park22 dezembro 2024
Kidscreen » Archive » Scholastic and Gaumont team up for Rocket Park22 dezembro 2024 -
 Play Chess Online for Free with Friends & Family22 dezembro 2024
Play Chess Online for Free with Friends & Family22 dezembro 2024 -
 Stream Stumble Guys Versi 0.37: The Ultimate Knockout Game to Download Now from Quihernistwa22 dezembro 2024
Stream Stumble Guys Versi 0.37: The Ultimate Knockout Game to Download Now from Quihernistwa22 dezembro 2024 -
 Kubo no me dejará ser invisible Temporada 2: ¿Qué fecha de lanzamiento?22 dezembro 2024
Kubo no me dejará ser invisible Temporada 2: ¿Qué fecha de lanzamiento?22 dezembro 2024 -
Berserk Volumes : Free Download, Borrow, and Streaming : Internet Archive22 dezembro 2024
-
 Magical Girl Magical Destroyers ep1 - BiliBili22 dezembro 2024
Magical Girl Magical Destroyers ep1 - BiliBili22 dezembro 2024 -
 img./cdn-cgi/image/quality=78,width=600,he22 dezembro 2024
img./cdn-cgi/image/quality=78,width=600,he22 dezembro 2024 -
 Blue Lock Season 2: Everything we know so far - Hindustan Times22 dezembro 2024
Blue Lock Season 2: Everything we know so far - Hindustan Times22 dezembro 2024 -
 Bayonetta 3 Developer Discusses Possibility of PlayStation and Xbox Ports22 dezembro 2024
Bayonetta 3 Developer Discusses Possibility of PlayStation and Xbox Ports22 dezembro 2024