Validating User Flows to Protect Software Defined Network Environments
Por um escritor misterioso
Last updated 22 dezembro 2024

Software Defined Network is a promising network paradigm which has led to several security threats in SDN applications that involve user flows, switches, and controllers in the network. Threats as spoofing, tampering, information disclosure, Denial of Service, flow table overloading, and so on have been addressed by many researchers. In this paper, we present novel SDN design to solve three security threats: flow table overloading is solved by constructing a star topology-based architecture, unsupervised hashing method mitigates link spoofing attack, and fuzzy classifier combined with L1-ELM running on a neural network for isolating anomaly packets from normal packets. For effective flow migration Discrete-Time Finite-State Markov Chain model is applied. Extensive simulations using OMNeT++ demonstrate the performance of our proposed approach, which is better at preserving holding time than are other state-of-the-art works from the literature.

PERM-GUARD: Authenticating the Validity of Flow Rules in Software

What is Network Security?
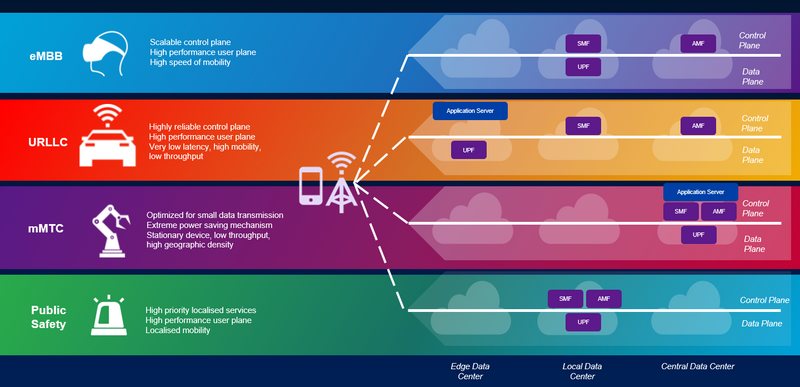
5G Network Slicing, What is it? 5G Slicing Architecture and
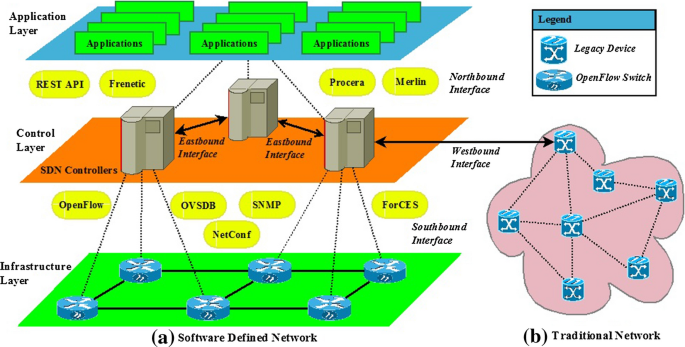
Scalability, Consistency, Reliability and Security in SDN

Validating User Flows to Protect Software Defined Network Environments

PERM-GUARD: Authenticating the Validity of Flow Rules in Software
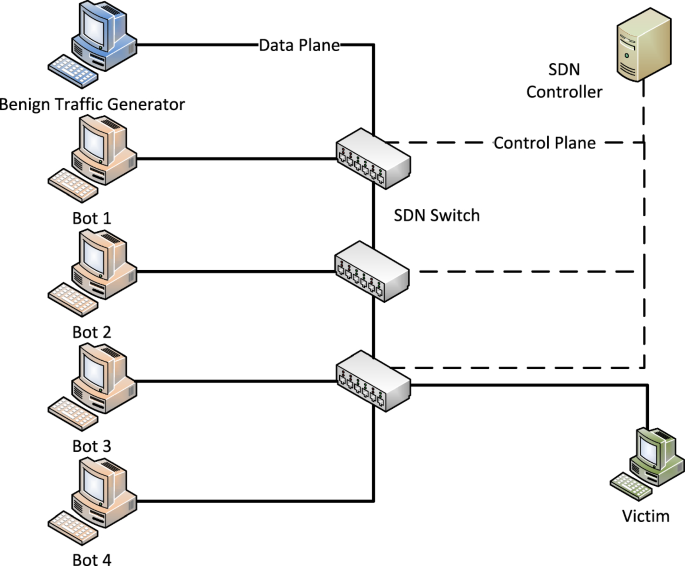
SDNTruth: Innovative DDoS Detection Scheme for Software-Defined
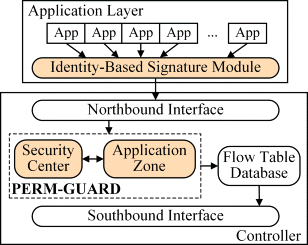
PERM-GUARD: Authenticating the Validity of Flow Rules in Software
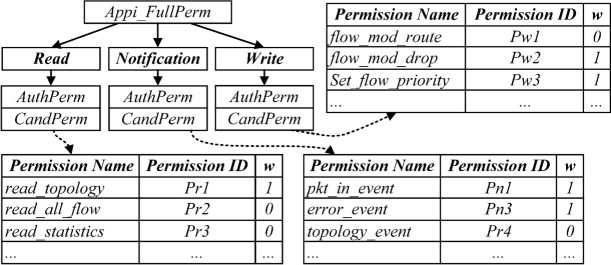
PERM-GUARD: Authenticating the Validity of Flow Rules in Software
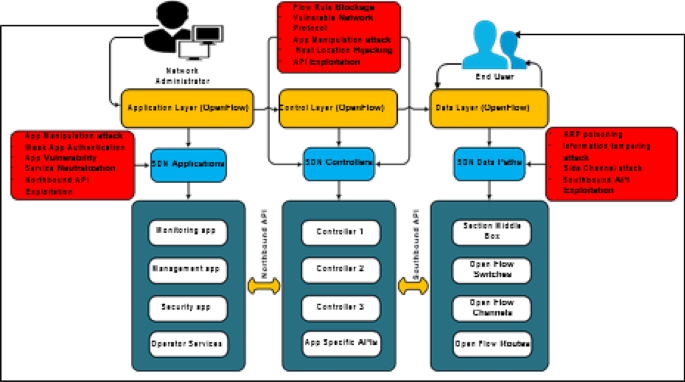
Security & Privacy in Software Defined Networks, Issues
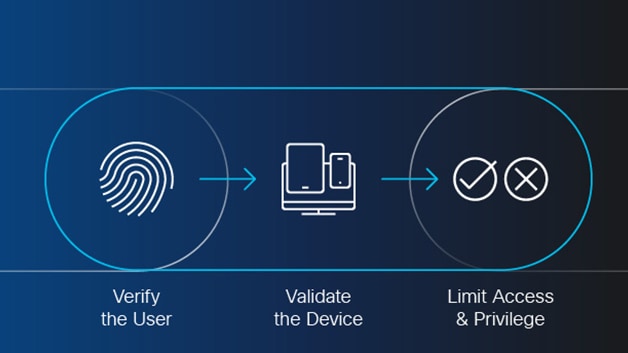
What Is Zero Trust Network Access? - Cisco
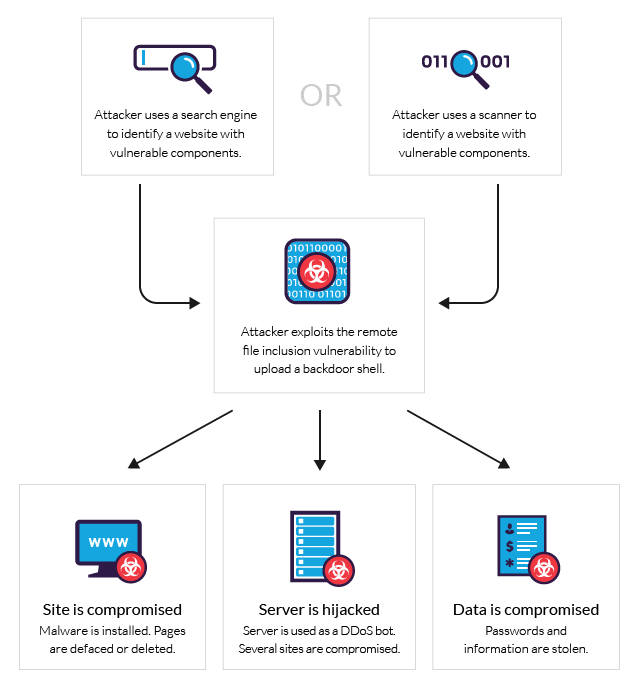
What is RFI Remote File Inclusion Example & Mitigation Methods
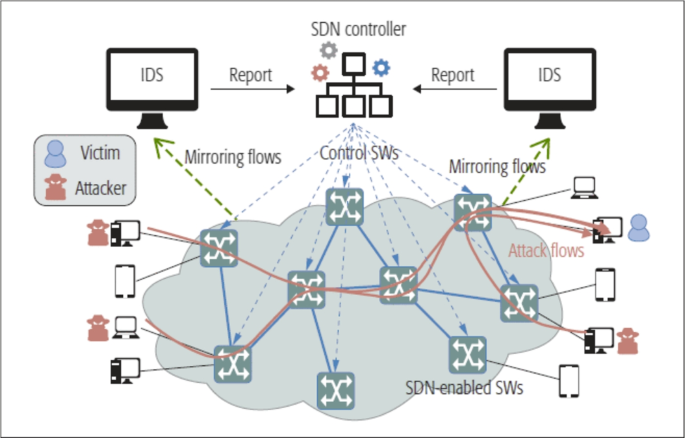
Software defined networks (SDNs) for environmental surveillance

Recommendations for networking and connectivity - Microsoft Azure
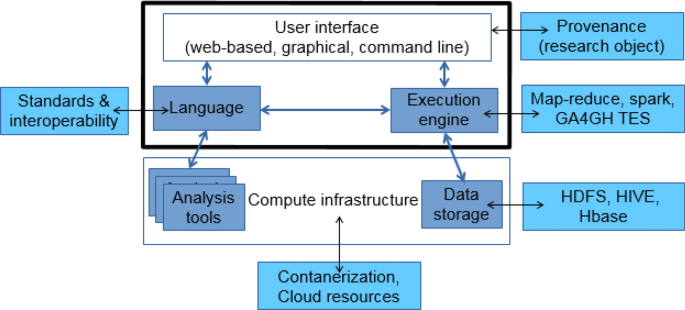
Design considerations for workflow management systems use in
Recomendado para você
-
 Operator and Function Overloading in Custom Python Classes – Real Python22 dezembro 2024
Operator and Function Overloading in Custom Python Classes – Real Python22 dezembro 2024 -
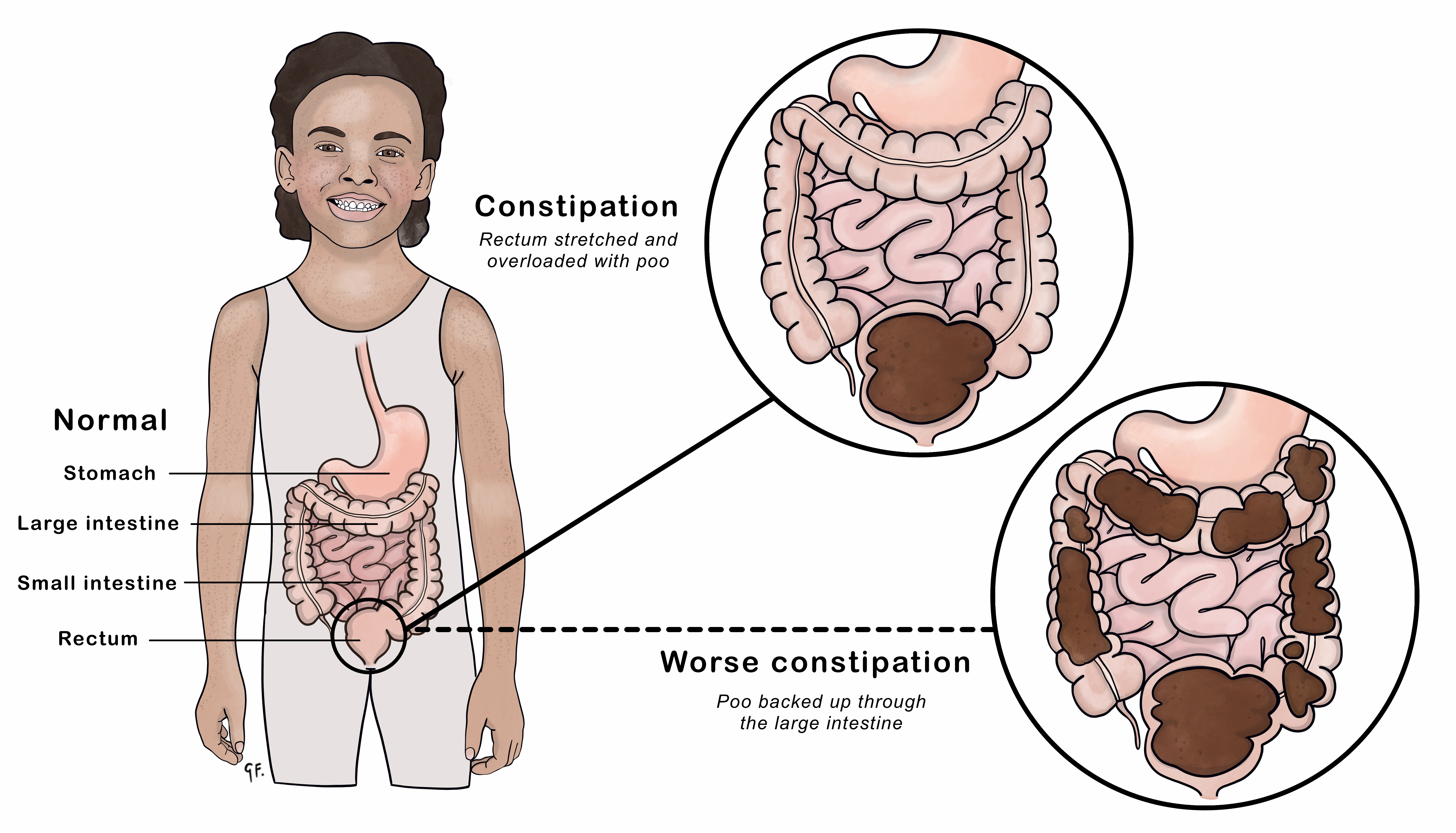 Constipation KidsHealth NZ22 dezembro 2024
Constipation KidsHealth NZ22 dezembro 2024 -
 Overload de métodos - POO - s02e1222 dezembro 2024
Overload de métodos - POO - s02e1222 dezembro 2024 -
Neurodive - The Condescending Tao of Poo Ahhh Poo bear.22 dezembro 2024
-
 Help Needed! Protein Overload? Moisture Overload? Hygral Fatigue? : r/curlyhair22 dezembro 2024
Help Needed! Protein Overload? Moisture Overload? Hygral Fatigue? : r/curlyhair22 dezembro 2024 -
To Get To The Bottom Of Your Microbiome, Start With A Swab Of Poo, NPR Article22 dezembro 2024
-
 Graphical User Interface of POO SG.22 dezembro 2024
Graphical User Interface of POO SG.22 dezembro 2024 -
 C# POO + Lógica de Programação Aplicada22 dezembro 2024
C# POO + Lógica de Programação Aplicada22 dezembro 2024 -
![PDF] Managing Overloaded Hosts for Dynamic Consolidation of Virtual Machines in Cloud Data Centers under Quality of Service Constraints](https://d3i71xaburhd42.cloudfront.net/a615968237d6f2cc1908f779bd9ff80d28f164d0/10-Table1-1.png) PDF] Managing Overloaded Hosts for Dynamic Consolidation of Virtual Machines in Cloud Data Centers under Quality of Service Constraints22 dezembro 2024
PDF] Managing Overloaded Hosts for Dynamic Consolidation of Virtual Machines in Cloud Data Centers under Quality of Service Constraints22 dezembro 2024 -
CMPA or lactose overload (foremilk/hindmilk imbalance)** (with pics) - November 2020 Babies, Forums22 dezembro 2024
você pode gostar
-
 JJSSKLL Gorilla Tag Plush Gorilla Stuffed Doll Gift for Friends22 dezembro 2024
JJSSKLL Gorilla Tag Plush Gorilla Stuffed Doll Gift for Friends22 dezembro 2024 -
 Golden Time/#1805868 - Zerochan Golden time anime, Golden time22 dezembro 2024
Golden Time/#1805868 - Zerochan Golden time anime, Golden time22 dezembro 2024 -
 Xbox Game Pass ”Core” FIM DA XBOX LIVE GOLD !22 dezembro 2024
Xbox Game Pass ”Core” FIM DA XBOX LIVE GOLD !22 dezembro 2024 -
 Base Calendário 2021 Vermelho - Imagem Legal22 dezembro 2024
Base Calendário 2021 Vermelho - Imagem Legal22 dezembro 2024 -
 Go gle Q whoisthe 11th hokage TUDO IMAGENS NOTICIAS COMPRAS VIDEO Jiraiya In other media. Jiraiya makes an appearance in two Naruto films, Naruto Shippuden the Movie: Bonds (2008) and Naruto Shippuden22 dezembro 2024
Go gle Q whoisthe 11th hokage TUDO IMAGENS NOTICIAS COMPRAS VIDEO Jiraiya In other media. Jiraiya makes an appearance in two Naruto films, Naruto Shippuden the Movie: Bonds (2008) and Naruto Shippuden22 dezembro 2024 -
 Jogo da memória 9 pares lembrancinha brinquedos de menino22 dezembro 2024
Jogo da memória 9 pares lembrancinha brinquedos de menino22 dezembro 2024 -
 Rebaixados Elite Brasil - Atualização (Vida Real, Novo Mapa e Muito mais)22 dezembro 2024
Rebaixados Elite Brasil - Atualização (Vida Real, Novo Mapa e Muito mais)22 dezembro 2024 -
 John colton hi-res stock photography and images - Alamy22 dezembro 2024
John colton hi-res stock photography and images - Alamy22 dezembro 2024 -
 MX Player Now On TV22 dezembro 2024
MX Player Now On TV22 dezembro 2024 -
 BMW 3 Series (E46) project - Classics World22 dezembro 2024
BMW 3 Series (E46) project - Classics World22 dezembro 2024


