Malware analysis Suspicious activity
Por um escritor misterioso
Last updated 08 janeiro 2025
Symmetry, Free Full-Text
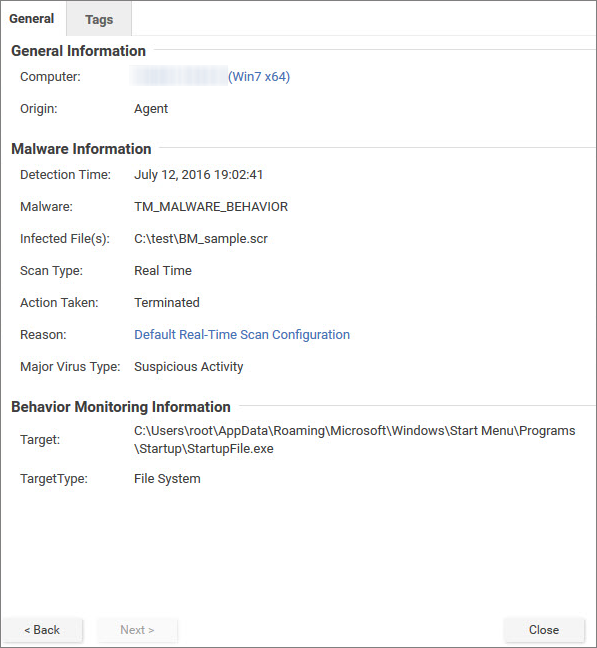
Enhanced anti-malware and ransomware scanning with behavior

Malware Analysis: Steps & Examples - CrowdStrike

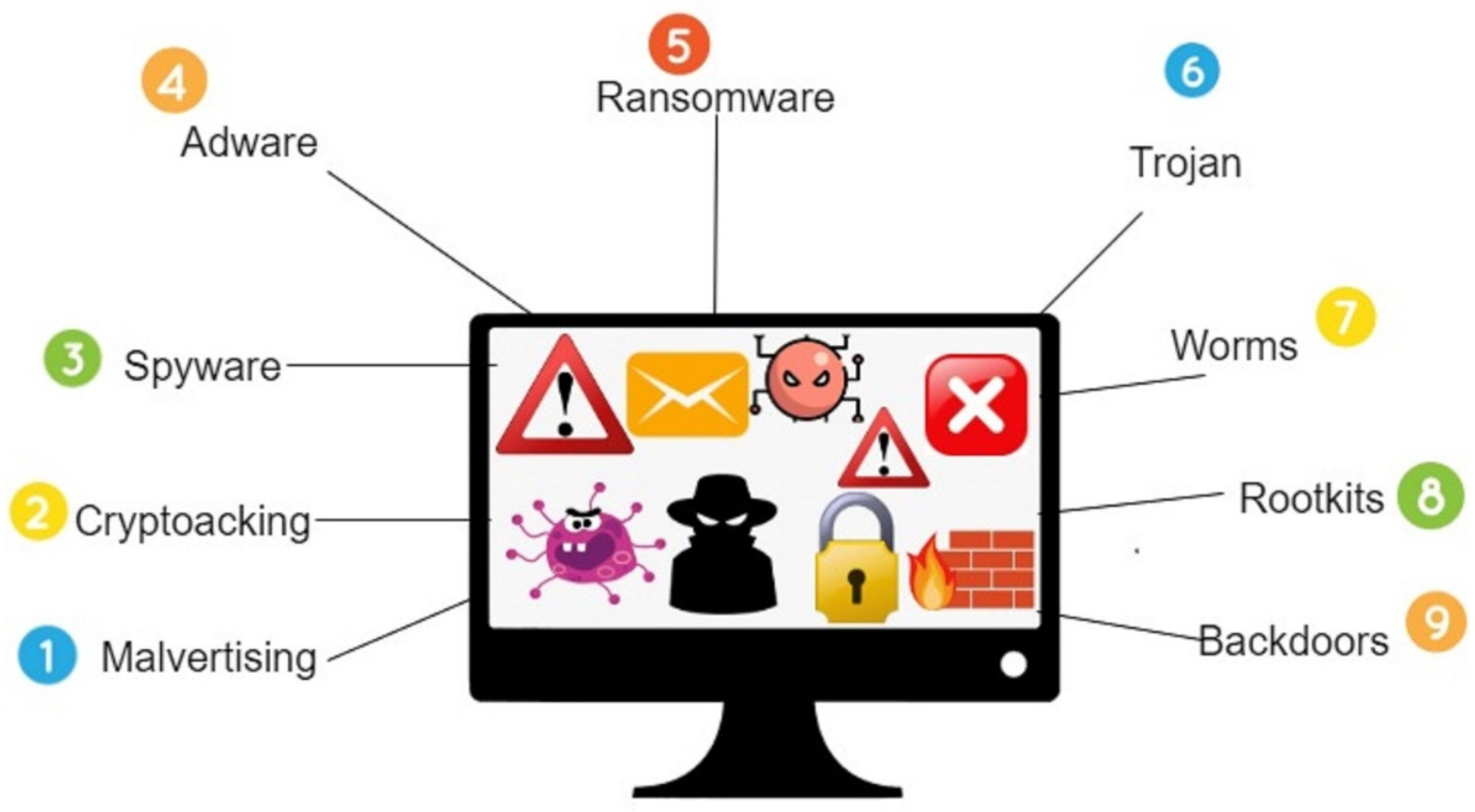
Malware Detection & Top Techniques Today
Remove McAfee Suspicious Activity Pop-ups [Virus Removal]
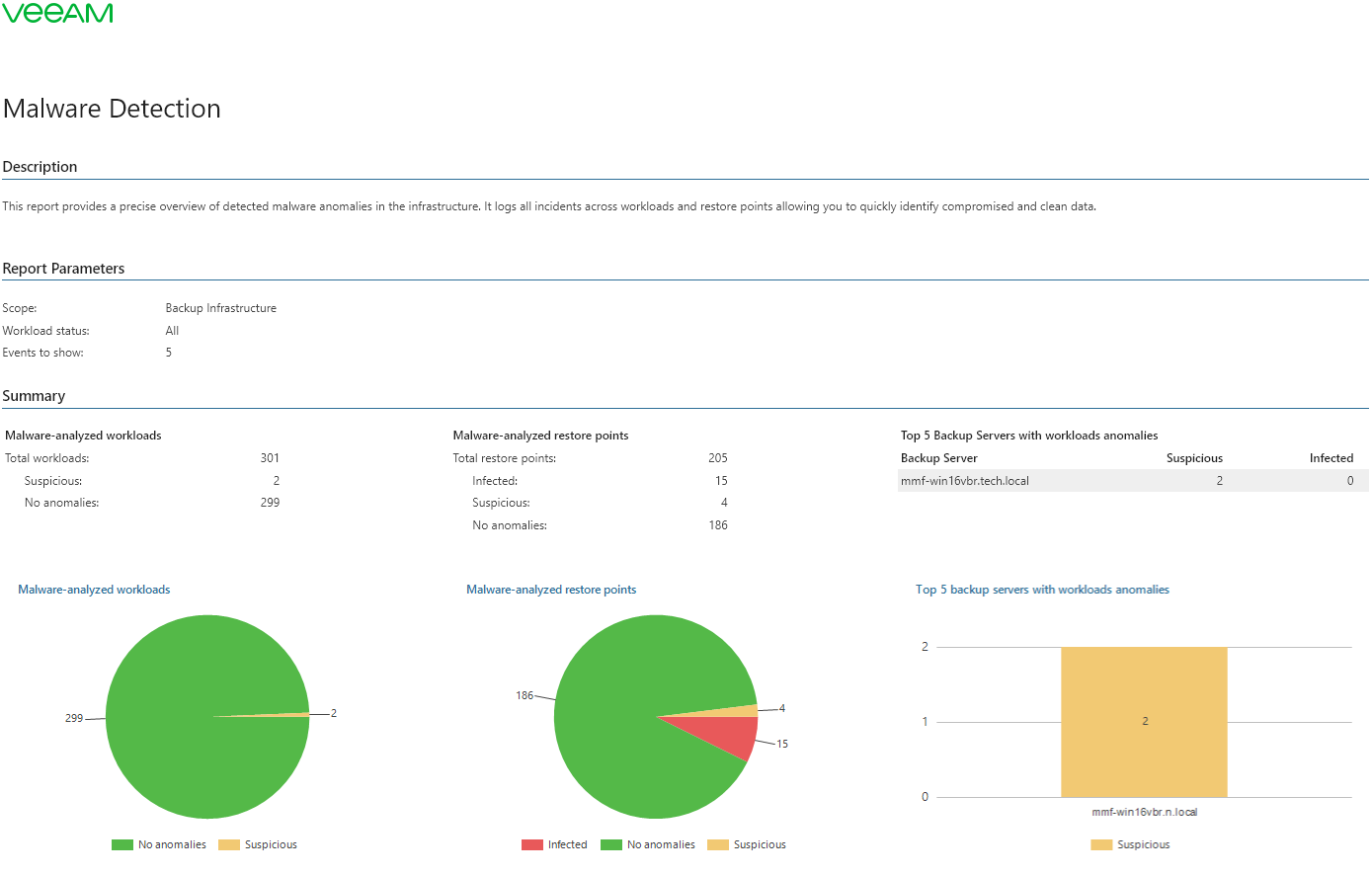
Malware Detection - Veeam ONE Reporting Guide

Dismantling ZLoader: How malicious ads led to disabled security
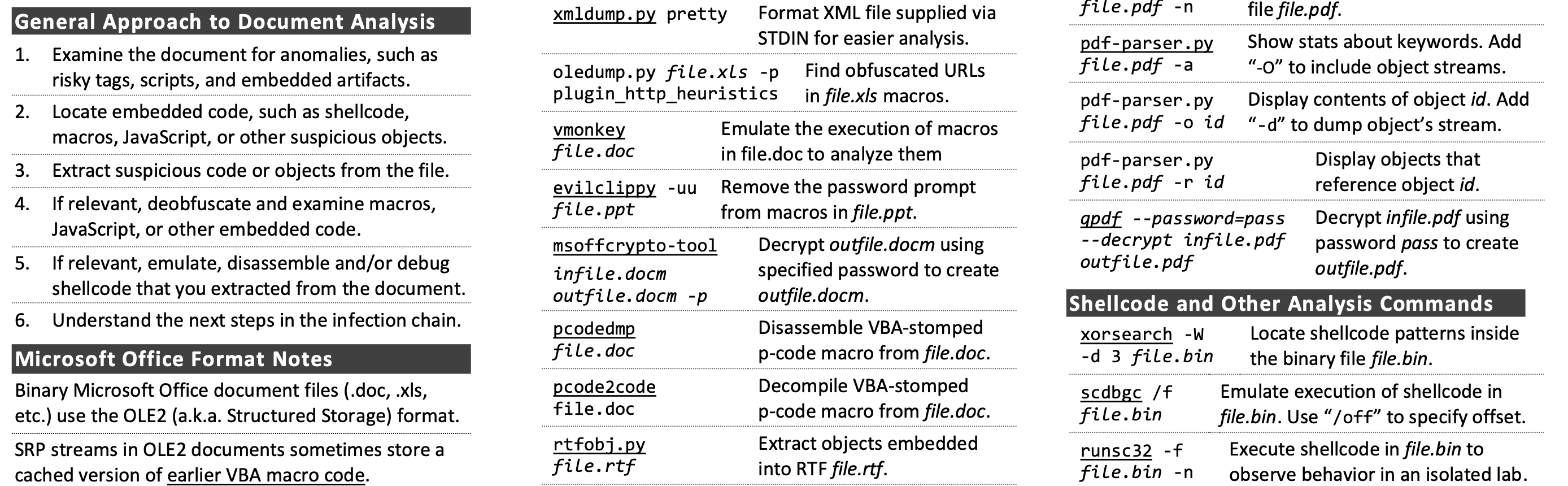
Analyzing Malicious Documents Cheat Sheet
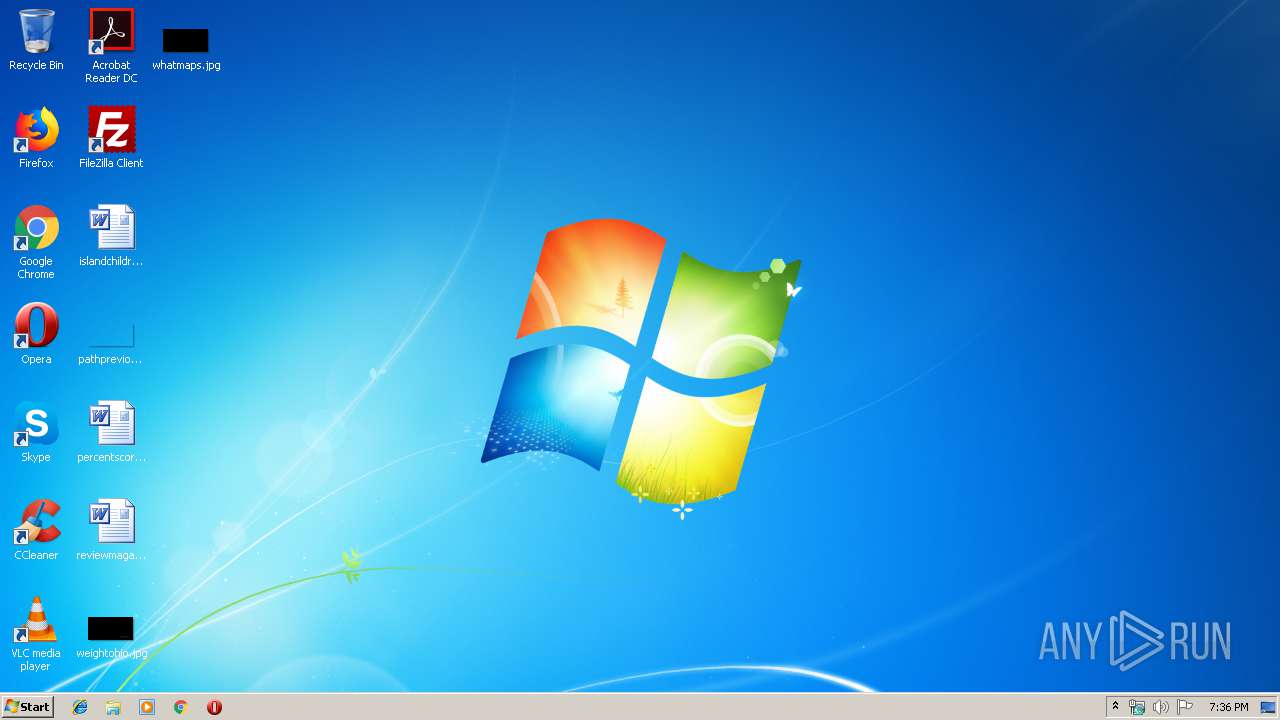
Malware analysis cable.exe Suspicious activity

A flow chart of malware detection approaches and features

REMnux toolkit for malware analysis version 7 released - Help Net
What is Malware Analysis? - SOC Prime
Recomendado para você
-
Hacking Simulator! - Roblox08 janeiro 2025
-
 Play Roblox on PC - Download for Free at08 janeiro 2025
Play Roblox on PC - Download for Free at08 janeiro 2025 -
XMAS☃️] Hack Simulator - Roblox08 janeiro 2025
-
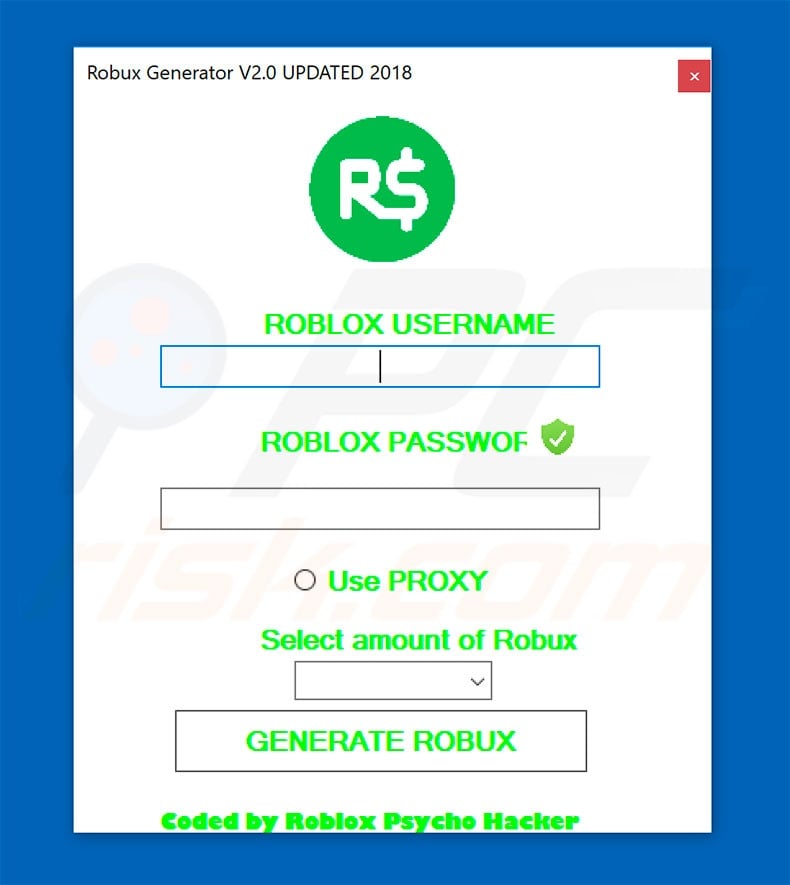 Roblox Virus - Malware removal instructions (updated)08 janeiro 2025
Roblox Virus - Malware removal instructions (updated)08 janeiro 2025 -
roblox-hacks · GitHub Topics · GitHub08 janeiro 2025
-
 Master mod menu for roblox APK for Android Download08 janeiro 2025
Master mod menu for roblox APK for Android Download08 janeiro 2025 -
 Stream Roblox Fluxus APK: Download and Play Roblox with Unlimited Features from Tara Sheldon08 janeiro 2025
Stream Roblox Fluxus APK: Download and Play Roblox with Unlimited Features from Tara Sheldon08 janeiro 2025 -
Roblox Mod Apk Unlimited Robux 2022 For Android08 janeiro 2025
-
 Stream Roblox Robux Infinity Download Apk 2022 Happymod from08 janeiro 2025
Stream Roblox Robux Infinity Download Apk 2022 Happymod from08 janeiro 2025 -
 Roblox responds to the hack that allowed a child's avatar to be raped in its game08 janeiro 2025
Roblox responds to the hack that allowed a child's avatar to be raped in its game08 janeiro 2025
você pode gostar
-
 Save 50% on Street Fighter V - Capcom Pro Tour: 2022 Premier Pass08 janeiro 2025
Save 50% on Street Fighter V - Capcom Pro Tour: 2022 Premier Pass08 janeiro 2025 -
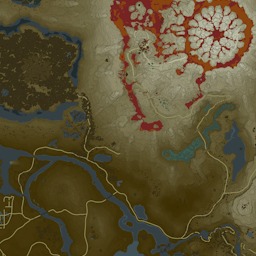 Hyrule · Interactive Maps · The Legend of Zelda: Breath of the08 janeiro 2025
Hyrule · Interactive Maps · The Legend of Zelda: Breath of the08 janeiro 2025 -
 Onde Jogar Vôlei em SP - 9 Lugares Excelentes08 janeiro 2025
Onde Jogar Vôlei em SP - 9 Lugares Excelentes08 janeiro 2025 -
 Fortinet Championship 2023: Winner's Payout & Prize Money Earnings08 janeiro 2025
Fortinet Championship 2023: Winner's Payout & Prize Money Earnings08 janeiro 2025 -
 roblox ropa mujer emo08 janeiro 2025
roblox ropa mujer emo08 janeiro 2025 -
 jounin-react08 janeiro 2025
jounin-react08 janeiro 2025 -
 DRAGON QUEST V on the App Store08 janeiro 2025
DRAGON QUEST V on the App Store08 janeiro 2025 -
 Lord Of The Rings Deluxe Art Scale Statue 1/10 Sauron 38 cm08 janeiro 2025
Lord Of The Rings Deluxe Art Scale Statue 1/10 Sauron 38 cm08 janeiro 2025 -
 Volition's giving away the Saints Row you never got to play08 janeiro 2025
Volition's giving away the Saints Row you never got to play08 janeiro 2025 -
 Assistir Watashi no Oshi wa Akuyaku Reijou Online completo08 janeiro 2025
Assistir Watashi no Oshi wa Akuyaku Reijou Online completo08 janeiro 2025
![XMAS☃️] Hack Simulator - Roblox](https://tr.rbxcdn.com/36ee6c8dba6592927e482008609226f4/150/150/Image/Png)
