Malware analysis Malicious activity
Por um escritor misterioso
Last updated 31 dezembro 2024

FBI, CISA, MS-ISAC release cybersecurity advisory on emerging Rhysida ransomware targeting critical sectors - Industrial Cyber

Malware Analysis Benefits Incident Response

Remediation and Malware Detection Overview

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog
10 Best Antivirus Software in 2023: Windows, Android, iOS, Mac

Robust Malware Detection Models: Learning From Adversarial Attacks and Defenses - Forensic Focus

Malware Analysis: Steps & Examples - CrowdStrike

Endpoint Detection and Response, Free - What is EDR Security?
TryHackMe Hacktivities

TryHackMe Hacktivities

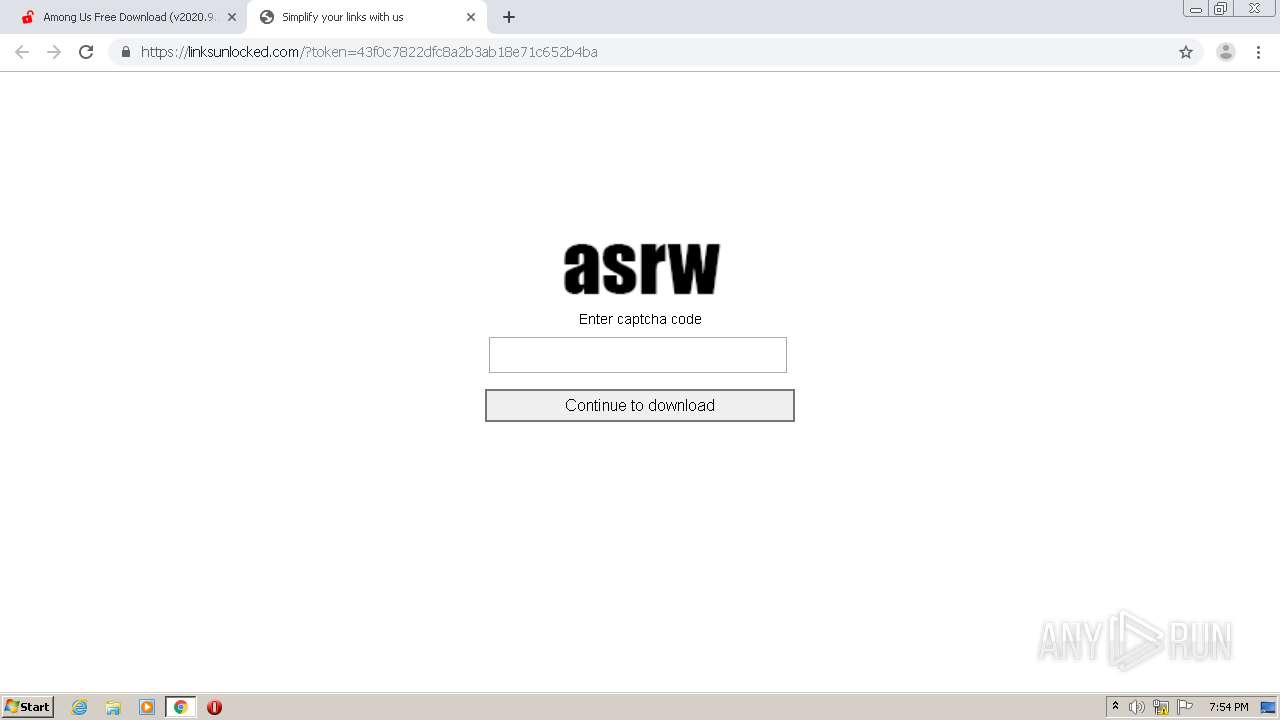
Malware analysis index.html Malicious activity
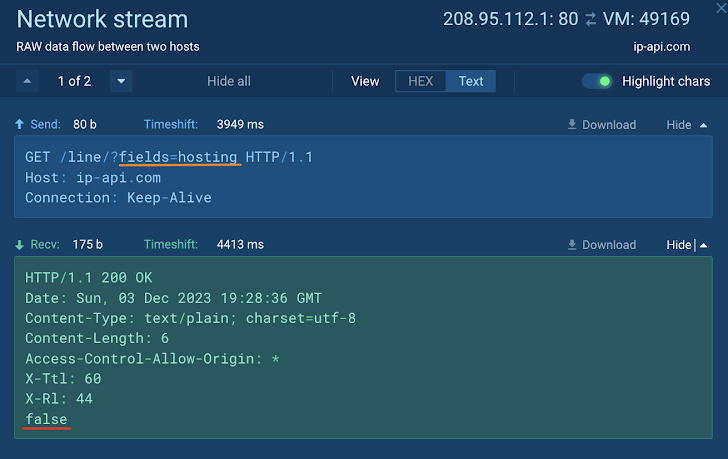
How to Analyze Malware's Network Traffic in A Sandbox

Malware Analysis: Steps & Examples - CrowdStrike
Recomendado para você
-
 I was just trying to download f1 2014 then i pressed download on steamunlocked.pro it changed to steamunlocked.net. which one is the ral one please help me i think i downloaded a31 dezembro 2024
I was just trying to download f1 2014 then i pressed download on steamunlocked.pro it changed to steamunlocked.net. which one is the ral one please help me i think i downloaded a31 dezembro 2024 -
 Web-Swinging Thrills Await: Embrace the Marvel Spider-Man Remastered Adventure in NYC! : steamunlocked: : Audible Books & Originals31 dezembro 2024
Web-Swinging Thrills Await: Embrace the Marvel Spider-Man Remastered Adventure in NYC! : steamunlocked: : Audible Books & Originals31 dezembro 2024 -
 Steamunlocked (steamunlockedgamespc) - Profile31 dezembro 2024
Steamunlocked (steamunlockedgamespc) - Profile31 dezembro 2024 -
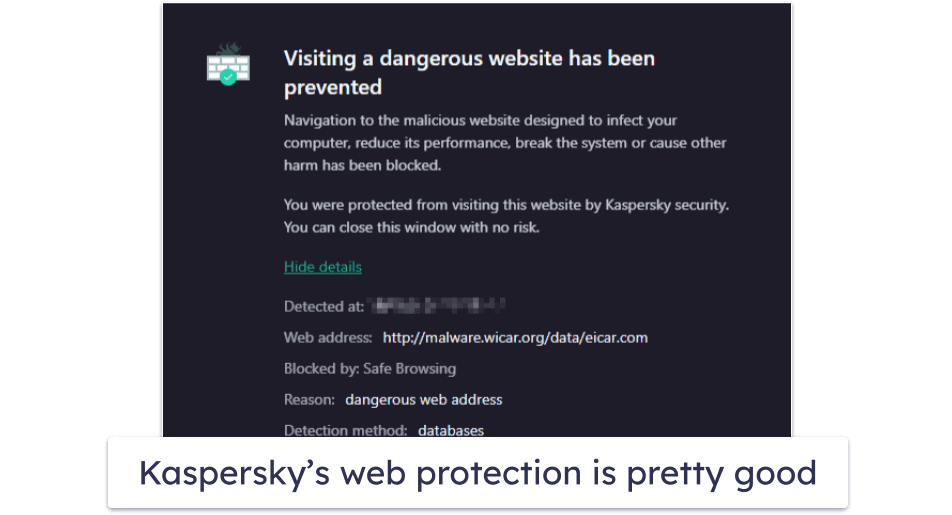
 Is SteamUnlocked Safe? 5 Secure Ways to Use It Without Risks31 dezembro 2024
Is SteamUnlocked Safe? 5 Secure Ways to Use It Without Risks31 dezembro 2024 -
 900+ Steamunlocked ideas in 2023 free download, puzzle solving, space sounds31 dezembro 2024
900+ Steamunlocked ideas in 2023 free download, puzzle solving, space sounds31 dezembro 2024 -
 Is Steam unlocked legit and safe? • TechBriefly31 dezembro 2024
Is Steam unlocked legit and safe? • TechBriefly31 dezembro 2024 -
 I've download the game on steam unlocked. Anybody know how can i run the mods on this version (Build 41) : r/projectzomboid31 dezembro 2024
I've download the game on steam unlocked. Anybody know how can i run the mods on this version (Build 41) : r/projectzomboid31 dezembro 2024 -
 What is SteamUnlocked? Is it legit and safe for downloading games?31 dezembro 2024
What is SteamUnlocked? Is it legit and safe for downloading games?31 dezembro 2024 -
 Need help with steamunlocked, I have 7-zip but unfortunately it keeps downloading 7-zip and not the intended games : r/PiratedGames31 dezembro 2024
Need help with steamunlocked, I have 7-zip but unfortunately it keeps downloading 7-zip and not the intended games : r/PiratedGames31 dezembro 2024 -
 why does steam unlocked have to use such a slow file hosting service? : r/Piracy31 dezembro 2024
why does steam unlocked have to use such a slow file hosting service? : r/Piracy31 dezembro 2024
você pode gostar
-
 Cheat Mobile Legends 2022 application31 dezembro 2024
Cheat Mobile Legends 2022 application31 dezembro 2024 -
 THE LEGO® BATMAN MOVIE 71017, Minifigures31 dezembro 2024
THE LEGO® BATMAN MOVIE 71017, Minifigures31 dezembro 2024 -
 Sad anime icons HD wallpapers31 dezembro 2024
Sad anime icons HD wallpapers31 dezembro 2024 -
 Five Nights at Freddy's Style 'Fisheye' - Godot Shaders31 dezembro 2024
Five Nights at Freddy's Style 'Fisheye' - Godot Shaders31 dezembro 2024 -
![Xbox Video on Xbox One lacks downloading capabilities [Update] - Neowin](https://cdn.neowin.com/news/images/uploaded/xboxvideoonxboxone.jpg) Xbox Video on Xbox One lacks downloading capabilities [Update] - Neowin31 dezembro 2024
Xbox Video on Xbox One lacks downloading capabilities [Update] - Neowin31 dezembro 2024 -
 K-ON! College, K-ON! Wiki31 dezembro 2024
K-ON! College, K-ON! Wiki31 dezembro 2024 -
 Black Adam Destroys Rotten Tomatoes' Credibility!31 dezembro 2024
Black Adam Destroys Rotten Tomatoes' Credibility!31 dezembro 2024 -
![The World Ends with You: The Animation The Complete Season [Blu-ray] - Best Buy](https://pisces.bbystatic.com/image2/BestBuy_US/images/products/4238268b-3dbc-406a-9727-73c5b84f9161.jpg) The World Ends with You: The Animation The Complete Season [Blu-ray] - Best Buy31 dezembro 2024
The World Ends with You: The Animation The Complete Season [Blu-ray] - Best Buy31 dezembro 2024 -
 TRADUÇÃO EM PORTUGUÊS-BR, ZELDA BOTW31 dezembro 2024
TRADUÇÃO EM PORTUGUÊS-BR, ZELDA BOTW31 dezembro 2024 -
 Assistir GOBLIN SLAYER: 2 Episodio 10 Online Gratis31 dezembro 2024
Assistir GOBLIN SLAYER: 2 Episodio 10 Online Gratis31 dezembro 2024