Malware analysis Malicious activity
Por um escritor misterioso
Last updated 22 dezembro 2024

Malware Analysis: Steps & Examples - CrowdStrike

Malware analysis metasploit.bat Malicious activity

Intro to Malware Analysis: What It Is & How It Works - InfoSec Insights

ReversingLabs Malware Lab: Detect, classify, analyze, and respond to malicious files - Help Net Security
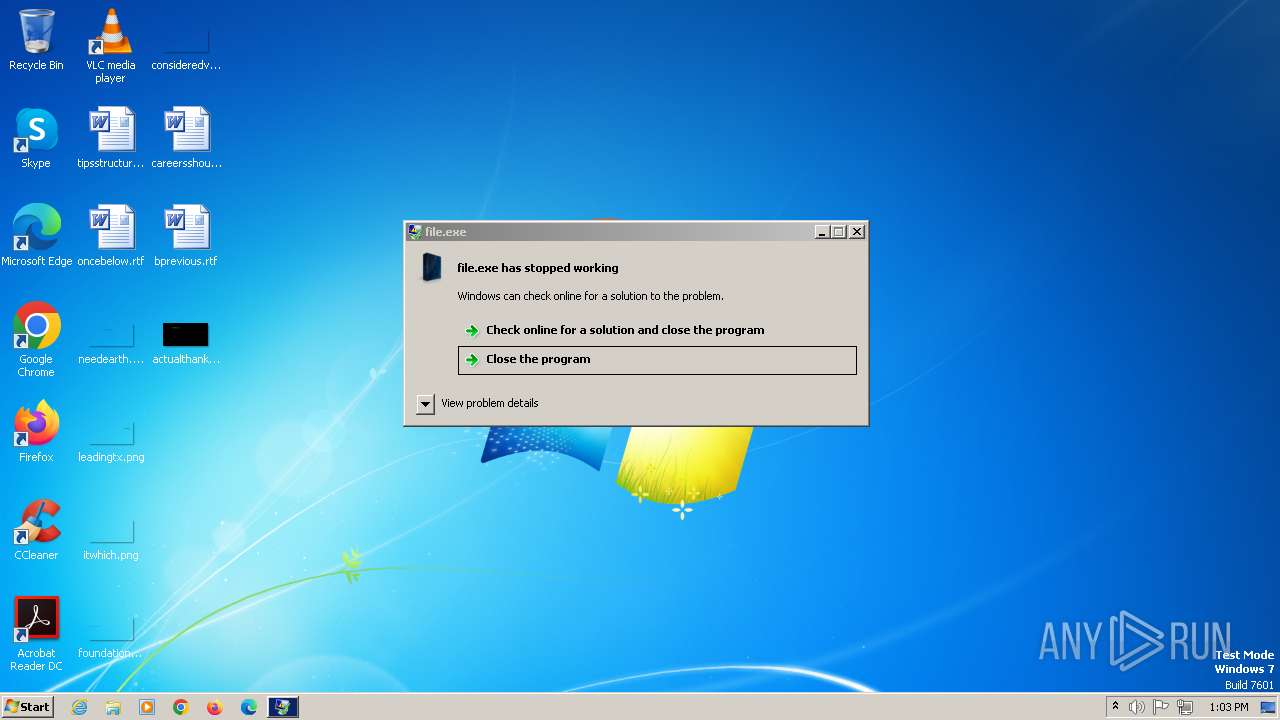
Malware analysis file Malicious activity

FBI, CISA, MS-ISAC release cybersecurity advisory on emerging Rhysida ransomware targeting critical sectors - Industrial Cyber

MetaDefender Cloud Advanced threat prevention and detection

The Guide to Ransomware Solutions in 2023 - Security Boulevard

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog

Cybersecurity News, Insights and Analysis

Endpoint Detection and Response, Free - What is EDR Security?
Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware: 9781788392501: A,

Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware
Recomendado para você
-
How to block ads on AnimeSuge? And Alternatives22 dezembro 2024
-
 What happened to Zoro.to? Is it shutdown or rebranded?22 dezembro 2024
What happened to Zoro.to? Is it shutdown or rebranded?22 dezembro 2024 -
 Anime T-Shirt Design, Anime Vector Graphics Bundle ,samurai t shirt Bu By Rana Creative22 dezembro 2024
Anime T-Shirt Design, Anime Vector Graphics Bundle ,samurai t shirt Bu By Rana Creative22 dezembro 2024 -
 it has been two-week since I stopped using animesuge to see if you guys removed this. so I'm when will this be gone (I'm not rage-hating) love this website, but this is22 dezembro 2024
it has been two-week since I stopped using animesuge to see if you guys removed this. so I'm when will this be gone (I'm not rage-hating) love this website, but this is22 dezembro 2024 -
resuploading it #animesuge #magicalpouch #todoroki ##todobakudekuchild22 dezembro 2024
-
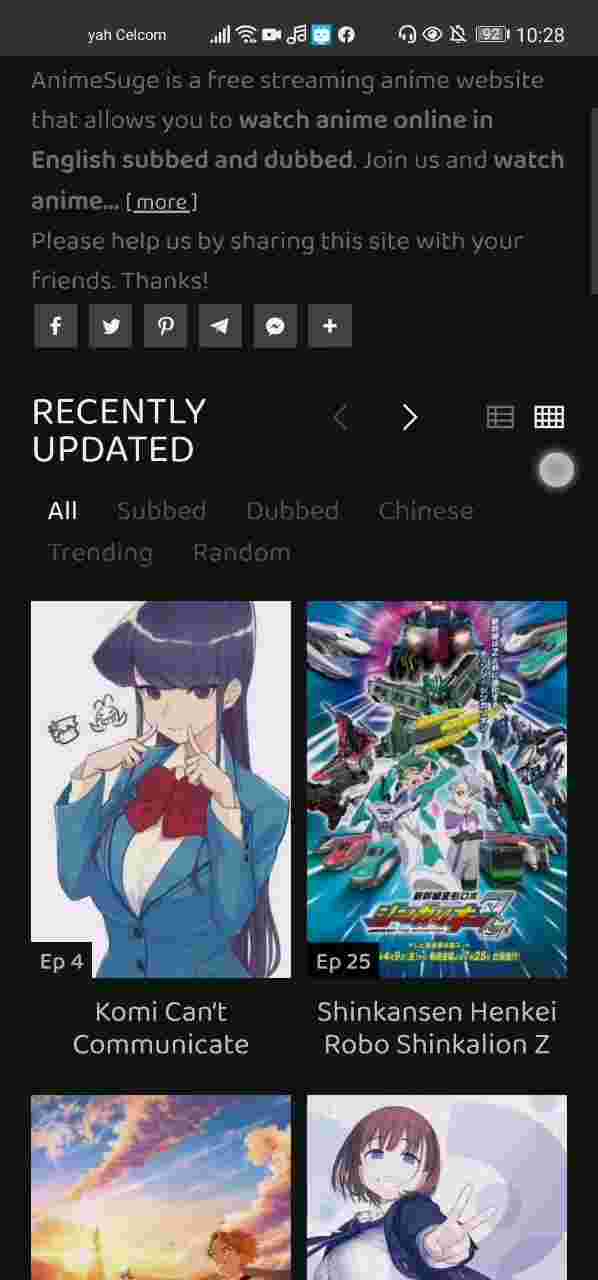 Anime Suge - BiliBili22 dezembro 2024
Anime Suge - BiliBili22 dezembro 2024 -
 Watch Anime Online in HD with SUB, DUB for FREE22 dezembro 2024
Watch Anime Online in HD with SUB, DUB for FREE22 dezembro 2024 -
I need help fr drop some anime sites22 dezembro 2024
-
Animepiracy Index22 dezembro 2024
-
anime#weebs#fypppppp#fyp#biral#demonslayermovie22 dezembro 2024
você pode gostar
-
Strikerz has announced UFL, a free-to-play football simulation game coming to “all major consoles.” . “UFL is a global online football…22 dezembro 2024
-
 Roblox Hacker Tier List22 dezembro 2024
Roblox Hacker Tier List22 dezembro 2024 -
 7,238 Boy Face Scared Stock Photos - Free & Royalty-Free Stock Photos from Dreamstime22 dezembro 2024
7,238 Boy Face Scared Stock Photos - Free & Royalty-Free Stock Photos from Dreamstime22 dezembro 2024 -
 Will World Cup 2022 Protests impact TV viewership and advertising? – The Hollywood Reporter22 dezembro 2024
Will World Cup 2022 Protests impact TV viewership and advertising? – The Hollywood Reporter22 dezembro 2024 -
 650 Ilustrações de Motocross - Getty Images22 dezembro 2024
650 Ilustrações de Motocross - Getty Images22 dezembro 2024 -
 Promised Land' Review: ABC Drama Stars Bellamy Young, John Ortiz22 dezembro 2024
Promised Land' Review: ABC Drama Stars Bellamy Young, John Ortiz22 dezembro 2024 -
 Genshin Impact 4.3 livestream codes release date and Special Program leaks22 dezembro 2024
Genshin Impact 4.3 livestream codes release date and Special Program leaks22 dezembro 2024 -
LIMITED] Airplane Simulator - Roblox22 dezembro 2024
-
 Andrea Botez on X: thanks for having us ☺️⛷️ @DewTour @MTNDEWGaming #ad / X22 dezembro 2024
Andrea Botez on X: thanks for having us ☺️⛷️ @DewTour @MTNDEWGaming #ad / X22 dezembro 2024 -
 Os memes da goleada do Flamengo no Grêmio - Diário do Rio de Janeiro22 dezembro 2024
Os memes da goleada do Flamengo no Grêmio - Diário do Rio de Janeiro22 dezembro 2024




![LIMITED] Airplane Simulator - Roblox](https://tr.rbxcdn.com/a3e4761475f3643d028b19a2925b9ee6/768/432/Image/Png)