JCP, Free Full-Text
Por um escritor misterioso
Last updated 22 dezembro 2024
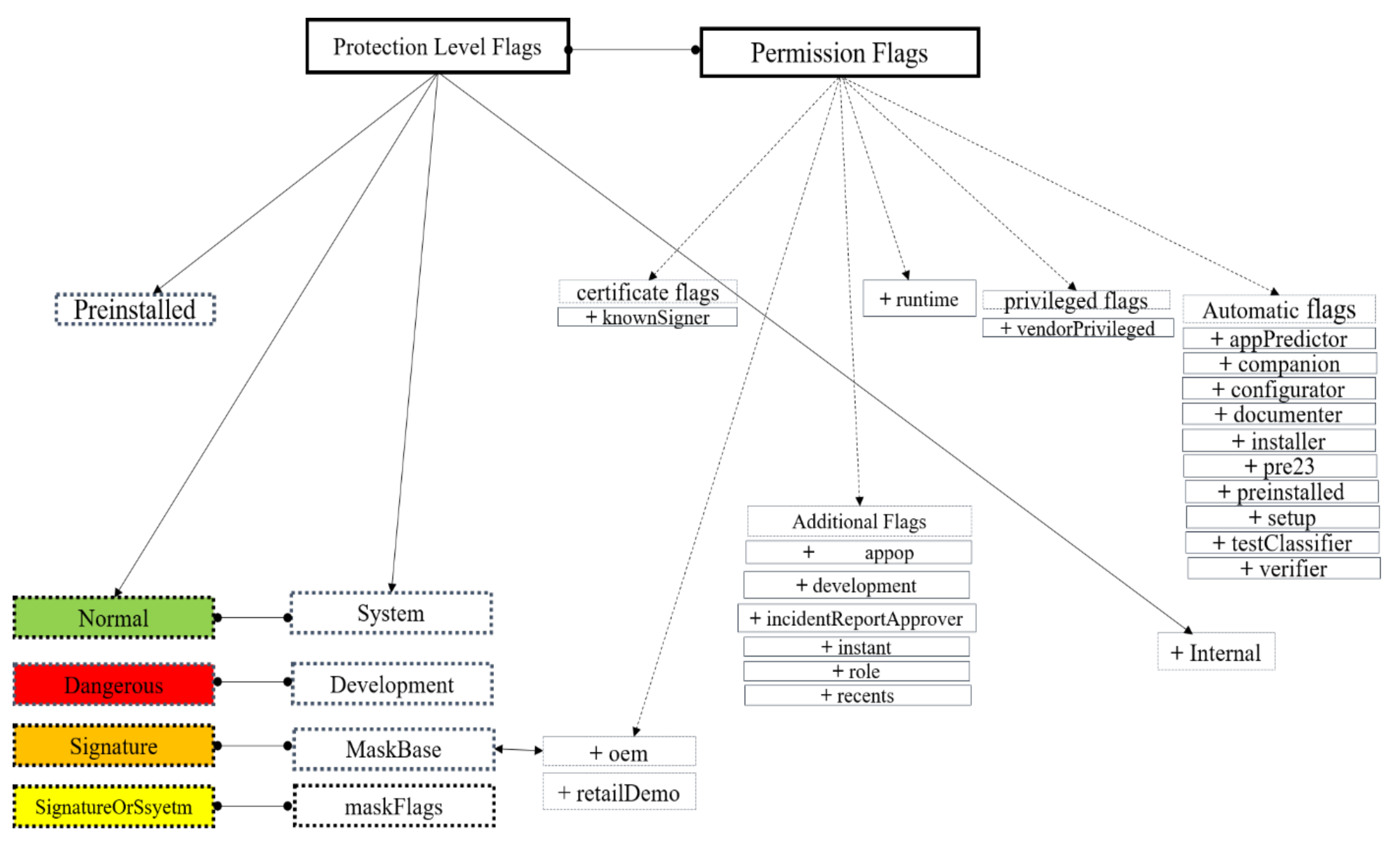
The evolution of mobile technology has increased correspondingly with the number of attacks on mobile devices. Malware attack on mobile devices is one of the top security challenges the mobile community faces daily. While malware classification and detection tools are being developed to fight malware infection, hackers keep deploying different infection strategies, including permissions usage. Among mobile platforms, Android is the most targeted by malware because of its open OS and popularity. Permissions is one of the major security techniques used by Android and other mobile platforms to control device resources and enhance access control. In this study, we used the t-Distribution stochastic neighbor embedding (t-SNE) and Self-Organizing Map techniques to produce a visualization method using exploratory factor plane analysis to visualize permissions correlation in Android applications. Two categories of datasets were used for this study: the benign and malicious datasets. Dataset was obtained from Contagio, VirusShare, VirusTotal, and Androzoo repositories. A total of 12,267 malicious and 10,837 benign applications with different categories were used. We demonstrate that our method can identify the correlation between permissions and classify Android applications based on their protection and threat level. Our results show that every permission has a threat level. This signifies those permissions with the same protection level have the same threat level.
JCPenney Online Credit Center

Journal of Cancer Prevention

1990 JCPenney Christmas Wishbook Catalog : Free Download, Borrow

JCPenney Credit Cards & Rewards Program - Worth It? [2023]

JC Penney Shipping Label Template
J.C. Penney's Homepage – 494 of 833 Homepage Examples – Baymard

PDF) Understanding the Basics of Meta-Analysis and How to Read a
JCP, Free Full-Text

5 Best JCPenney Online Coupons, Promo Codes - Dec 2023 - Honey
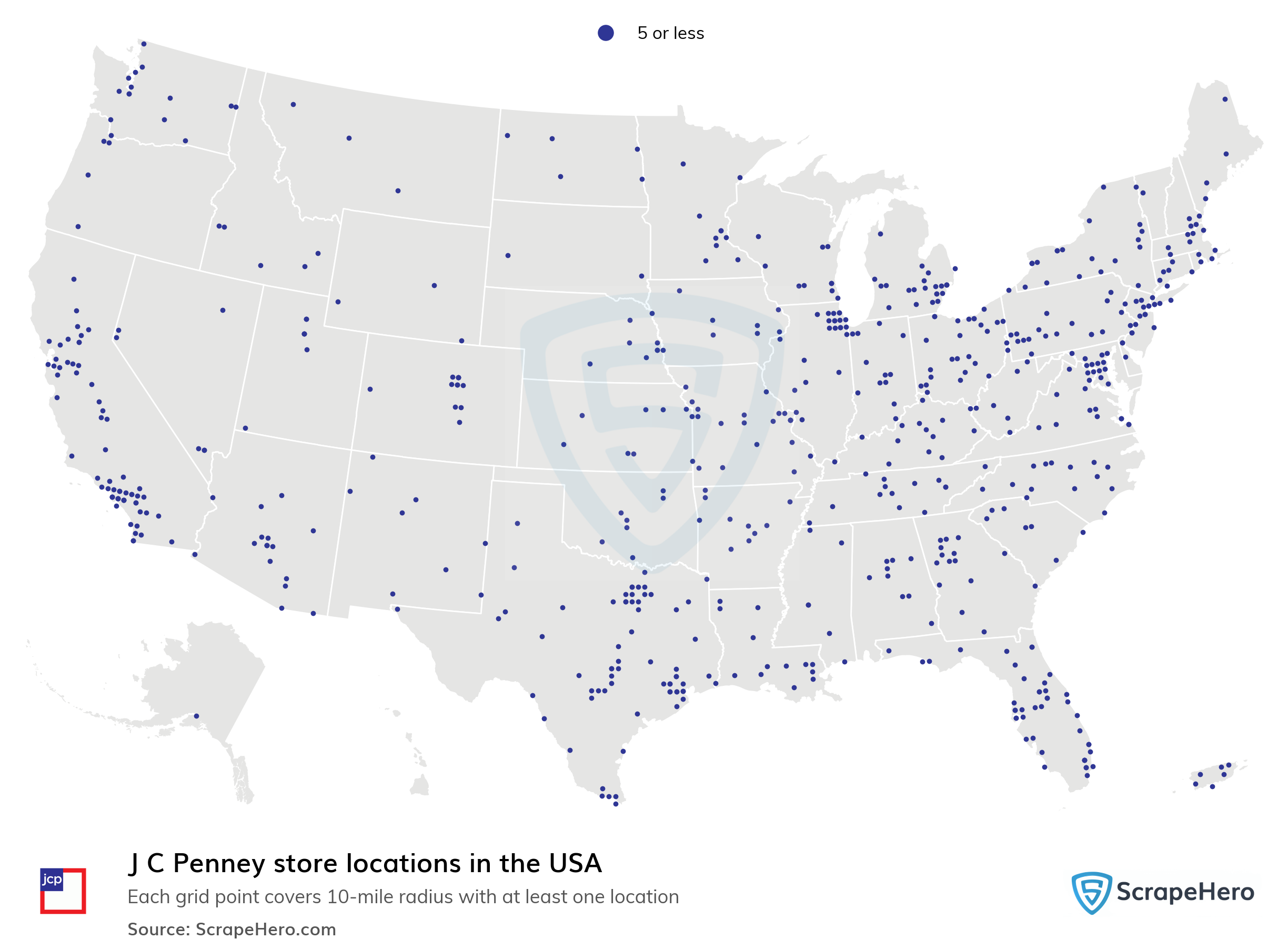
Number of J C Penney locations in the USA in 2023

J.C. Penney's Search Field – 261 of 660 Search Field Examples
Understanding and Managing Withdrawal Syndromes After
Recomendado para você
-
Cheat Engine - Wikipedia22 dezembro 2024
-
 Cheat Engine :: View topic - Using Cheat engine in android game ?22 dezembro 2024
Cheat Engine :: View topic - Using Cheat engine in android game ?22 dezembro 2024 -
 10 Best AI Apps for Android to Make Life Easier22 dezembro 2024
10 Best AI Apps for Android to Make Life Easier22 dezembro 2024 -
 Cheat Engine - Download22 dezembro 2024
Cheat Engine - Download22 dezembro 2024 -
 Undetected Cheat Engine + Driver, 202322 dezembro 2024
Undetected Cheat Engine + Driver, 202322 dezembro 2024 -
 Tutorial: Reverse Engineering a Private API22 dezembro 2024
Tutorial: Reverse Engineering a Private API22 dezembro 2024 -
 43 Browser Extensions to Perform Accessibility Testing Effectively • DigitalA11Y22 dezembro 2024
43 Browser Extensions to Perform Accessibility Testing Effectively • DigitalA11Y22 dezembro 2024 -
 7 open source alternatives to VS Code22 dezembro 2024
7 open source alternatives to VS Code22 dezembro 2024 -
 Review: Apple's powerful new 'basic' iPad is a real budget laptop replacement22 dezembro 2024
Review: Apple's powerful new 'basic' iPad is a real budget laptop replacement22 dezembro 2024 -
Yonas Leguesse on LinkedIn: #mobilesecurity #reverseengineering22 dezembro 2024
você pode gostar
-
 Hd Wallpapers Photos and Images22 dezembro 2024
Hd Wallpapers Photos and Images22 dezembro 2024 -
 JUJUTSU KAISEN Shibuya Incident Arc Episode 17 Recap - Crunchyroll News22 dezembro 2024
JUJUTSU KAISEN Shibuya Incident Arc Episode 17 Recap - Crunchyroll News22 dezembro 2024 -
 GTA V - A TEORIA SOBRE O DESTINO DE NIKO BELLIC!22 dezembro 2024
GTA V - A TEORIA SOBRE O DESTINO DE NIKO BELLIC!22 dezembro 2024 -
Mini World - API Wiki - Great teacher 7/24 🏜The22 dezembro 2024
-
 Dua Lipa's Personal Favorite 'Future Nostalgia' Lyrics Are From22 dezembro 2024
Dua Lipa's Personal Favorite 'Future Nostalgia' Lyrics Are From22 dezembro 2024 -
![Blender/FNAF] Molten Freddy UCN icon recreation by RazvanAndrei123](https://images-wixmp-ed30a86b8c4ca887773594c2.wixmp.com/f/52671c08-c1d4-443a-871c-2bbc036d9dbe/deizot0-da4b3318-6560-42ce-b273-fcdf7d48c06c.png?token=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJ1cm46YXBwOjdlMGQxODg5ODIyNjQzNzNhNWYwZDQxNWVhMGQyNmUwIiwiaXNzIjoidXJuOmFwcDo3ZTBkMTg4OTgyMjY0MzczYTVmMGQ0MTVlYTBkMjZlMCIsIm9iaiI6W1t7InBhdGgiOiJcL2ZcLzUyNjcxYzA4LWMxZDQtNDQzYS04NzFjLTJiYmMwMzZkOWRiZVwvZGVpem90MC1kYTRiMzMxOC02NTYwLTQyY2UtYjI3My1mY2RmN2Q0OGMwNmMucG5nIn1dXSwiYXVkIjpbInVybjpzZXJ2aWNlOmZpbGUuZG93bmxvYWQiXX0.eNh61sO7GzwuaXsHuRBd3bvkt7DIEFf-kEmPR1vEN4M) Blender/FNAF] Molten Freddy UCN icon recreation by RazvanAndrei12322 dezembro 2024
Blender/FNAF] Molten Freddy UCN icon recreation by RazvanAndrei12322 dezembro 2024 -
 Gênio Quiz 3 - Respostas22 dezembro 2024
Gênio Quiz 3 - Respostas22 dezembro 2024 -
kanojo ga koushaku tei dublado|Pesquisa do TikTok22 dezembro 2024
-
 Boneco Dragon Ball Stars Super Saiyan 4 Goku- Fun Divirta-se - Ri Happy22 dezembro 2024
Boneco Dragon Ball Stars Super Saiyan 4 Goku- Fun Divirta-se - Ri Happy22 dezembro 2024 -
 Shiny Mega Gengar by ElementalDraws on DeviantArt22 dezembro 2024
Shiny Mega Gengar by ElementalDraws on DeviantArt22 dezembro 2024


