Bluejacking vs Bluesnarfing: Exploring Bluetooth Hacking Variations.
Por um escritor misterioso
Last updated 22 dezembro 2024

Discover the potential security risks of Bluetooth technology, including various types of attacks like bluejacking, bluesnarfing, bluebugging

What's Bluejacking, Bluesnarfing, and Bluebugging?

THE BLUEJACKING

Security threats in Bluetooth technology - ScienceDirect
GitHub - StealthIQ/Bluestrike: Bluestrike: CLI tool to hack Bluetooth devices through speaker jamming, traffic spoofing & device hijacking (In the making)
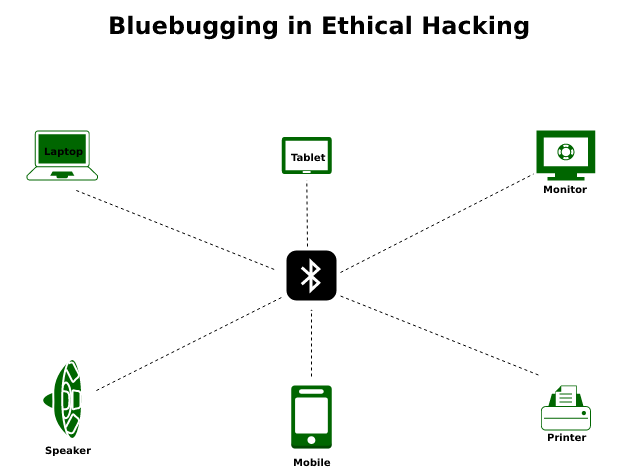
Bluebugging in Wireless Networks - GeeksforGeeks

Can someone hack my phone by using Bluetooth?

How Secure is Bluetooth? A Full Guide to Bluetooth Safety
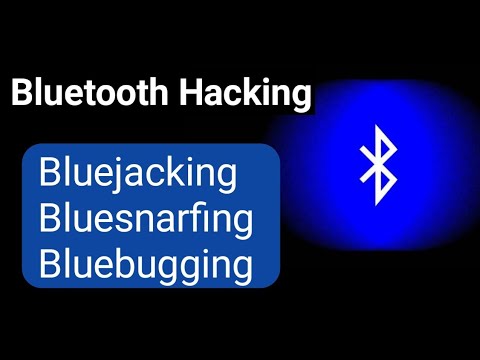
Bluetooth H∆cking? bluejacking bluesnarfing and bluebugging explained, Technical Haroon

Bluetooth Attack? bluebugging? bluesnarfing bluejacking? #shorts
Recomendado para você
-
 Hacker Typer Pro - Prank App on the App Store22 dezembro 2024
Hacker Typer Pro - Prank App on the App Store22 dezembro 2024 -
 Hacker Simulator Launcher for Android - Download22 dezembro 2024
Hacker Simulator Launcher for Android - Download22 dezembro 2024 -
 Hacks at the Massachusetts Institute of Technology - Wikipedia22 dezembro 2024
Hacks at the Massachusetts Institute of Technology - Wikipedia22 dezembro 2024 -
 Hacker attempts to sell data of 500 million WhatsApp users on dark web22 dezembro 2024
Hacker attempts to sell data of 500 million WhatsApp users on dark web22 dezembro 2024 -
Bluetooth Phone Hacker prank22 dezembro 2024
-
 What is Anonymous? The group went from 4chan to cyberattacks on Russia22 dezembro 2024
What is Anonymous? The group went from 4chan to cyberattacks on Russia22 dezembro 2024 -
Hackers - latest news, breaking stories and comment - The Independent22 dezembro 2024
-
 CapCut_account hack prank fb22 dezembro 2024
CapCut_account hack prank fb22 dezembro 2024 -
 Armed police sent to Mumsnet founder's home after hoax call22 dezembro 2024
Armed police sent to Mumsnet founder's home after hoax call22 dezembro 2024 -
hack it – Apps on Google Play22 dezembro 2024
você pode gostar
-
 Relógio Magnum Masculino Analógico Couro MA32952J em Promoção na22 dezembro 2024
Relógio Magnum Masculino Analógico Couro MA32952J em Promoção na22 dezembro 2024 -
 Mirai Nikki Redial - Yuno and Yuki Reunite on Make a GIF22 dezembro 2024
Mirai Nikki Redial - Yuno and Yuki Reunite on Make a GIF22 dezembro 2024 -
 GB Flame - The Chosen One MP3 Download & Lyrics22 dezembro 2024
GB Flame - The Chosen One MP3 Download & Lyrics22 dezembro 2024 -
 Play Games Online for Free at22 dezembro 2024
Play Games Online for Free at22 dezembro 2024 -
 Scp 3008 (the infinite ikea) In real life - Imgflip22 dezembro 2024
Scp 3008 (the infinite ikea) In real life - Imgflip22 dezembro 2024 -
 Electric Mini Fan Air Blower For Inflatable Toy Costume Doll Battery Powered USB22 dezembro 2024
Electric Mini Fan Air Blower For Inflatable Toy Costume Doll Battery Powered USB22 dezembro 2024 -
![Updated] Pokemon GBA ROM HACK With Alola Region, Z Move, Mega Evolution & New Gymleaders!](https://i.ytimg.com/vi/4EffRIz43wA/maxresdefault.jpg) Updated] Pokemon GBA ROM HACK With Alola Region, Z Move, Mega Evolution & New Gymleaders!22 dezembro 2024
Updated] Pokemon GBA ROM HACK With Alola Region, Z Move, Mega Evolution & New Gymleaders!22 dezembro 2024 -
 Medal - The #1 Social Clipping & Recording App22 dezembro 2024
Medal - The #1 Social Clipping & Recording App22 dezembro 2024 -
 CHESS TRAPS, Chess moves22 dezembro 2024
CHESS TRAPS, Chess moves22 dezembro 2024 -
 LIVE UPDATES: UEFA Champions League 2018/19 group stage draw22 dezembro 2024
LIVE UPDATES: UEFA Champions League 2018/19 group stage draw22 dezembro 2024
