Cryptojacking: Understanding and defending against cloud compute
Por um escritor misterioso
Last updated 03 janeiro 2025

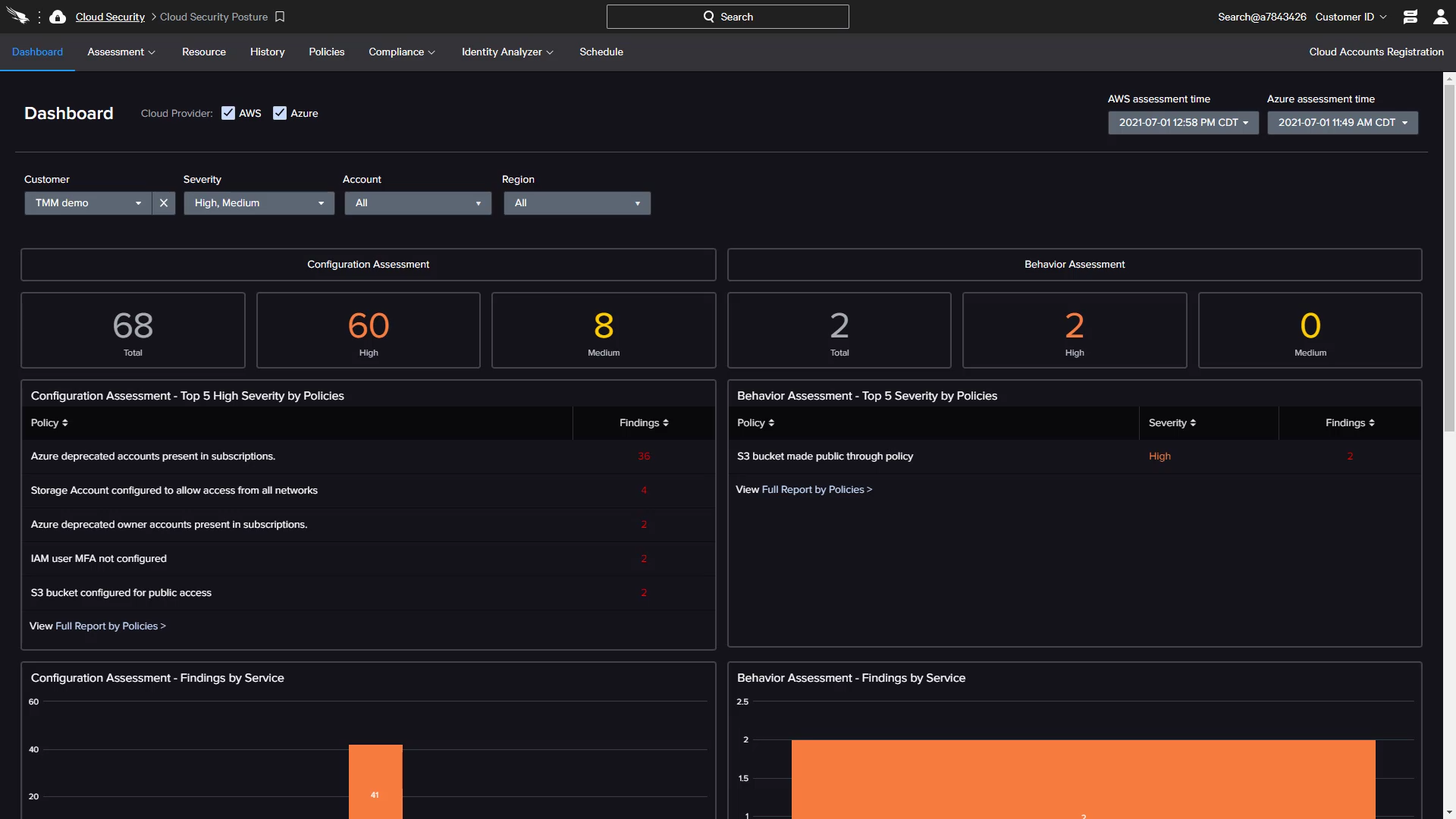
How to Monitor for Cryptomining in the Cloud
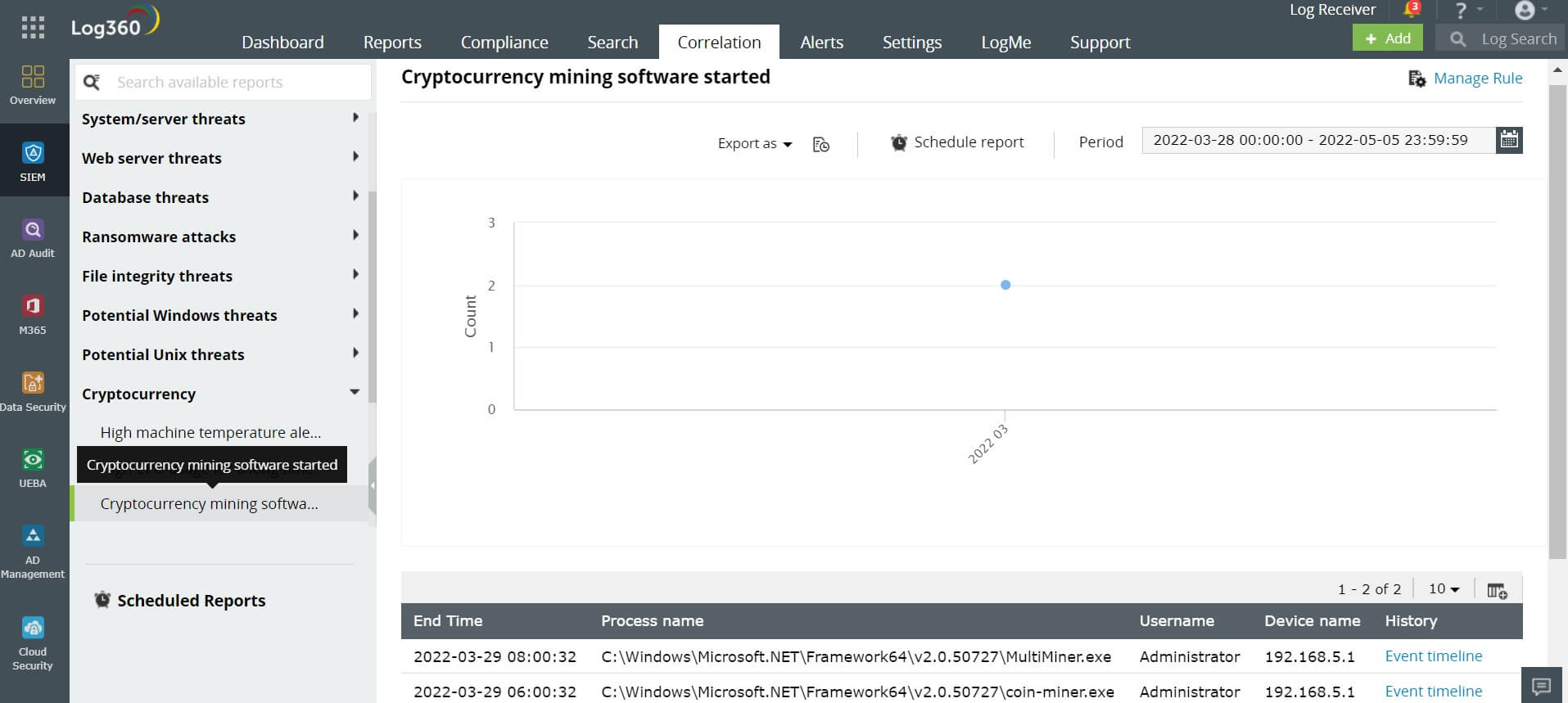
Cryptojacking demystified: Part 2
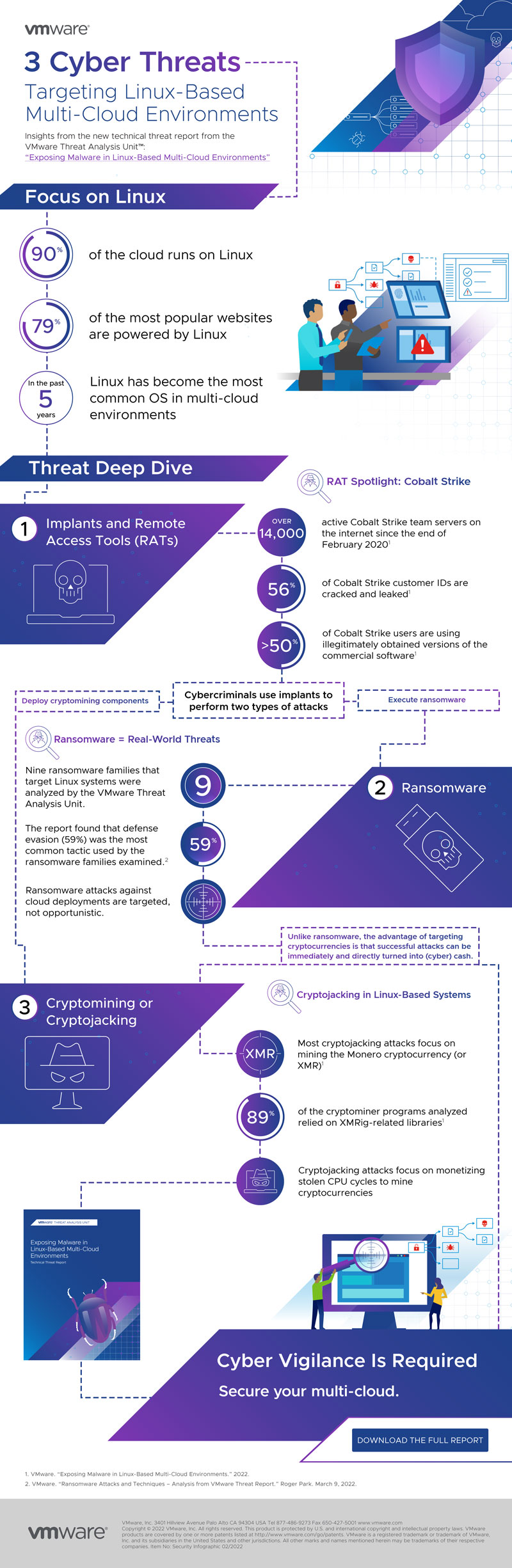
Infographic – Exposing Malware in Linux-Based Multi-Cloud

What is Cryptojacking? Definition, Detection, Prevention

ITVolks
What Is Cryptocurrency Mining? How to Prevent Cryptojacking? - Huawei
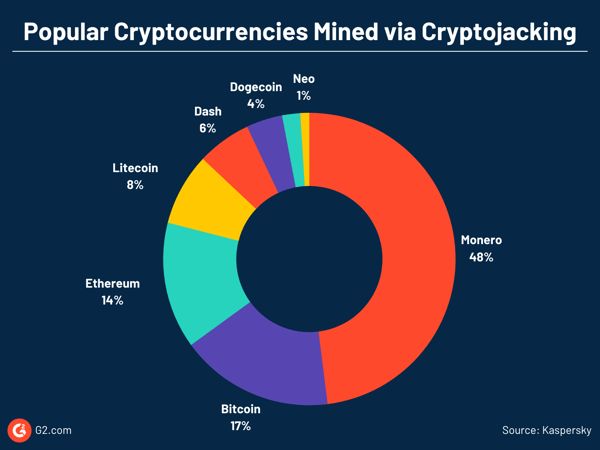
The Silent Threat of Cryptojacking and How to Protect Yourself

Cyrptojacking - How It Works and How to Protect Your Business

Cryptojacking: Understanding and defending against cloud compute
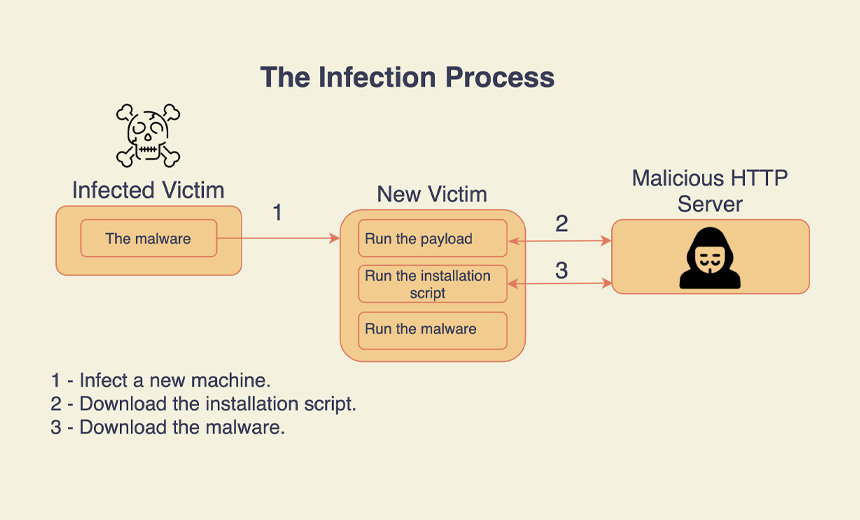
Cryptojacking Malware Adds Rootkit, Worming Capabilities

Cybersecurity Attacks 101: Phishing, Cryptojacking and Ransomware
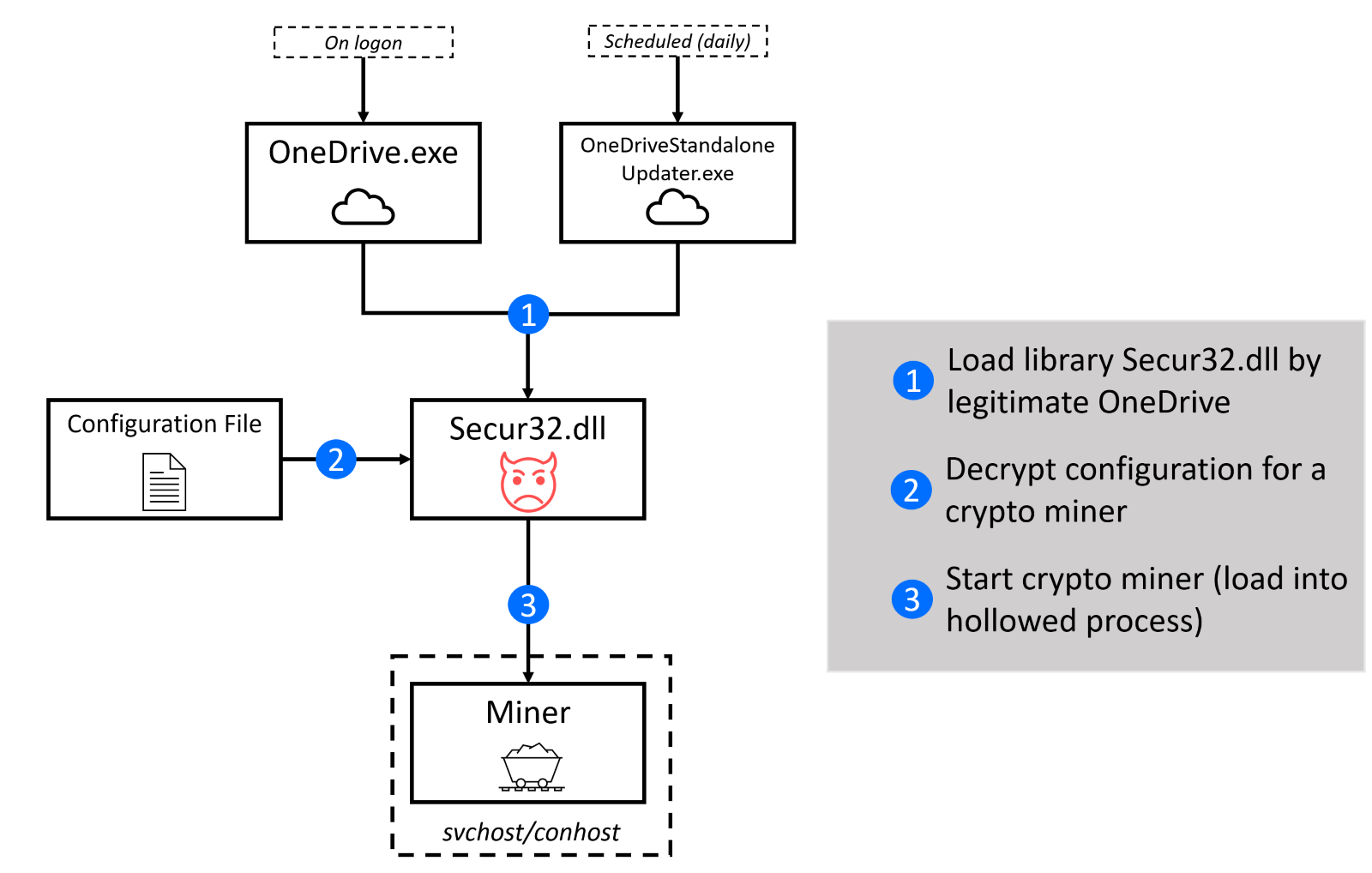
Deep Dive into a Cryptojacking Operation
Cryptojacking - 5 Ways To Prevent Attacks

The Threat of Cryptojacking: Unveiling the Silent Cyber Robbery
Recomendado para você
-
 Sudden Attack03 janeiro 2025
Sudden Attack03 janeiro 2025 -
 The Global Burden of Cardiovascular Diseases and Risk: A Compass for Future Health03 janeiro 2025
The Global Burden of Cardiovascular Diseases and Risk: A Compass for Future Health03 janeiro 2025 -
 Severe heart attack causing sudden death affects 96,150 people in Karnataka every year03 janeiro 2025
Severe heart attack causing sudden death affects 96,150 people in Karnataka every year03 janeiro 2025 -
 10 Conflicts to Watch in 202303 janeiro 2025
10 Conflicts to Watch in 202303 janeiro 2025 -
 New Games with Gold for March 2023 - Xbox Wire03 janeiro 2025
New Games with Gold for March 2023 - Xbox Wire03 janeiro 2025 -
AFGSC names 2023 Global Strike Challenge winners > U.S. Strategic03 janeiro 2025
-
 Strikes, riots and civil commotion outlook 202303 janeiro 2025
Strikes, riots and civil commotion outlook 202303 janeiro 2025 -
 Wild otter attack leads to woman being airlifted to hospital, 203 janeiro 2025
Wild otter attack leads to woman being airlifted to hospital, 203 janeiro 2025 -
 Latest Statistics Sudden Cardiac Arrest Foundation03 janeiro 2025
Latest Statistics Sudden Cardiac Arrest Foundation03 janeiro 2025 -
/cdn.vox-cdn.com/uploads/chorus_asset/file/25029019/1743339233.jpg) Pro-Palestine protest: What unites the global protests for03 janeiro 2025
Pro-Palestine protest: What unites the global protests for03 janeiro 2025
você pode gostar
-
![100+] Dark Minimalist Wallpapers](https://wallpapers.com/images/featured/dark-minimalist-4dgrytq4ymoszpcq.jpg) 100+] Dark Minimalist Wallpapers03 janeiro 2025
100+] Dark Minimalist Wallpapers03 janeiro 2025 -
Lelouch lamperouge wallpaper by Kira10j - Download on ZEDGE™03 janeiro 2025
-
 BATATAS FRITAS CROCANTES COM MANTEIGA E ALHO - Teste Receitas03 janeiro 2025
BATATAS FRITAS CROCANTES COM MANTEIGA E ALHO - Teste Receitas03 janeiro 2025 -
 GoldenEye 007 (F) ROM Download - Nintendo DS(NDS)03 janeiro 2025
GoldenEye 007 (F) ROM Download - Nintendo DS(NDS)03 janeiro 2025 -
 5,031 Thomas Mitchell Photos & High Res Pictures - Getty Images03 janeiro 2025
5,031 Thomas Mitchell Photos & High Res Pictures - Getty Images03 janeiro 2025 -
 Russia lore in ohio song03 janeiro 2025
Russia lore in ohio song03 janeiro 2025 -
 Calendário de jogos do Sporting em Fevereiro 2023 - Camarote Leonino03 janeiro 2025
Calendário de jogos do Sporting em Fevereiro 2023 - Camarote Leonino03 janeiro 2025 -
 Ditto Music - Wikipedia03 janeiro 2025
Ditto Music - Wikipedia03 janeiro 2025 -
 Decoração festa 40 anos03 janeiro 2025
Decoração festa 40 anos03 janeiro 2025 -
 Restaurants Open on Thanksgiving in Asheville & Pre-order Meals03 janeiro 2025
Restaurants Open on Thanksgiving in Asheville & Pre-order Meals03 janeiro 2025
