Complete UAF exploit - UD Capture
Por um escritor misterioso
Last updated 22 dezembro 2024

Use-After-Use-After-Free Exploit UAF by Genrating Your Own
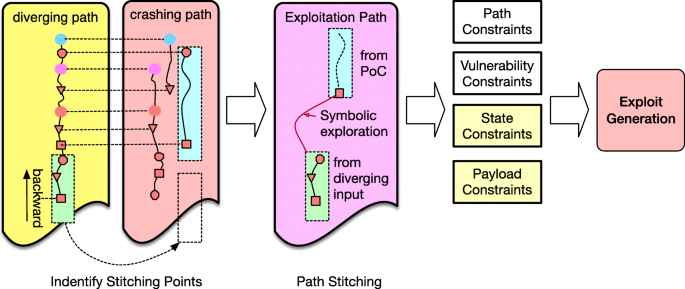
From proof-of-concept to exploitable, Cybersecurity
The big heap adventure. Mastering heap exploitation techniques on

Use-After-Use-After-Free: Exploit UAF by Generating Your Own

SETTLERS OF NETLINK: Exploiting a limited UAF in nf_tables (CVE

SETTLERS OF NETLINK: Exploiting a limited UAF in nf_tables (CVE

Google Reports 27 New Chrome Browser Exploits

Automated Use-After-Free Detection and Exploit Mitigation: How Far
Guest Blog Post - Memory corruption vulnerabilities in Edge
Recomendado para você
-
 6 Best King Legacy Script GUIs 202322 dezembro 2024
6 Best King Legacy Script GUIs 202322 dezembro 2024 -
![UPDATE 4.7.1💧] King Legacy Script 2023 - AutoFarm](https://theclashify.com/wp-content/uploads/2023/05/King-Legacy-Script.jpg) UPDATE 4.7.1💧] King Legacy Script 2023 - AutoFarm22 dezembro 2024
UPDATE 4.7.1💧] King Legacy Script 2023 - AutoFarm22 dezembro 2024 -
 Script King Legacy Update 4.66 (Auto Farm, Raid, Teleport, NPC)22 dezembro 2024
Script King Legacy Update 4.66 (Auto Farm, Raid, Teleport, NPC)22 dezembro 2024 -
 The Best Reviewed Games of 2022 - IGN22 dezembro 2024
The Best Reviewed Games of 2022 - IGN22 dezembro 2024 -
Trace Metals in Global Air: First Results from the GAPS and GAPS Megacities Networks22 dezembro 2024
-
![🧲UPDATED] King Legacy Script Hack](https://i.ytimg.com/vi/bxvskBgBXhw/maxresdefault.jpg) 🧲UPDATED] King Legacy Script Hack22 dezembro 2024
🧲UPDATED] King Legacy Script Hack22 dezembro 2024 -
 Scribes of the Cairo Geniza22 dezembro 2024
Scribes of the Cairo Geniza22 dezembro 2024 -
 The Legacy of Larry by Montecito Journal - Issuu22 dezembro 2024
The Legacy of Larry by Montecito Journal - Issuu22 dezembro 2024 -
 Loras College Legacy Symposium 2015 Abstracts by Loras College - Issuu22 dezembro 2024
Loras College Legacy Symposium 2015 Abstracts by Loras College - Issuu22 dezembro 2024 -
DNC Chair/Rep. Debbie Wasserman Schultz on death of DNC staffer Seth Conrad Rich22 dezembro 2024
você pode gostar
-
 roblox face code:) em 2023 Fotos de coisas bonitas, Colares de22 dezembro 2024
roblox face code:) em 2023 Fotos de coisas bonitas, Colares de22 dezembro 2024 -
 Warrior PVP season 4 - Outfit - TBC Classic22 dezembro 2024
Warrior PVP season 4 - Outfit - TBC Classic22 dezembro 2024 -
 little witch academia, Tumblr22 dezembro 2024
little witch academia, Tumblr22 dezembro 2024 -
 Jen-Joyce - Student, General Artist22 dezembro 2024
Jen-Joyce - Student, General Artist22 dezembro 2024 -
 NOVO ANIME DE NANATSU NO TAIZAI ? ANIMAÇÃO INCRIVEL! NANATSU NO22 dezembro 2024
NOVO ANIME DE NANATSU NO TAIZAI ? ANIMAÇÃO INCRIVEL! NANATSU NO22 dezembro 2024 -
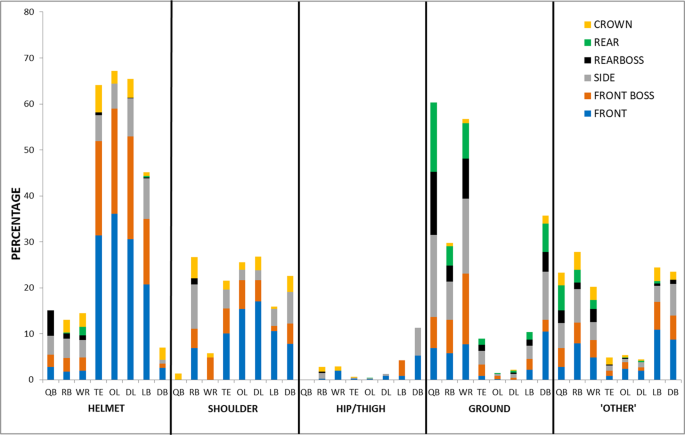 A novel repetitive head impact exposure measurement tool22 dezembro 2024
A novel repetitive head impact exposure measurement tool22 dezembro 2024 -
 Episódio 4 da segunda temporada de Demon Slayer é adiado - Critical Hits22 dezembro 2024
Episódio 4 da segunda temporada de Demon Slayer é adiado - Critical Hits22 dezembro 2024 -
 Italian Football TV on X: OFFICIAL: FIORENTINA WILL BE IN GROUP F22 dezembro 2024
Italian Football TV on X: OFFICIAL: FIORENTINA WILL BE IN GROUP F22 dezembro 2024 -
 Shrekt GIFs - Get the best GIF on GIPHY22 dezembro 2024
Shrekt GIFs - Get the best GIF on GIPHY22 dezembro 2024 -
 Free Vector Strategy online games abstract concept illustration. pc22 dezembro 2024
Free Vector Strategy online games abstract concept illustration. pc22 dezembro 2024
