Operation Exchange Marauder: Active Exploitation of Multiple Zero-Day Microsoft Exchange Vulnerabilities
Por um escritor misterioso
Last updated 23 dezembro 2024
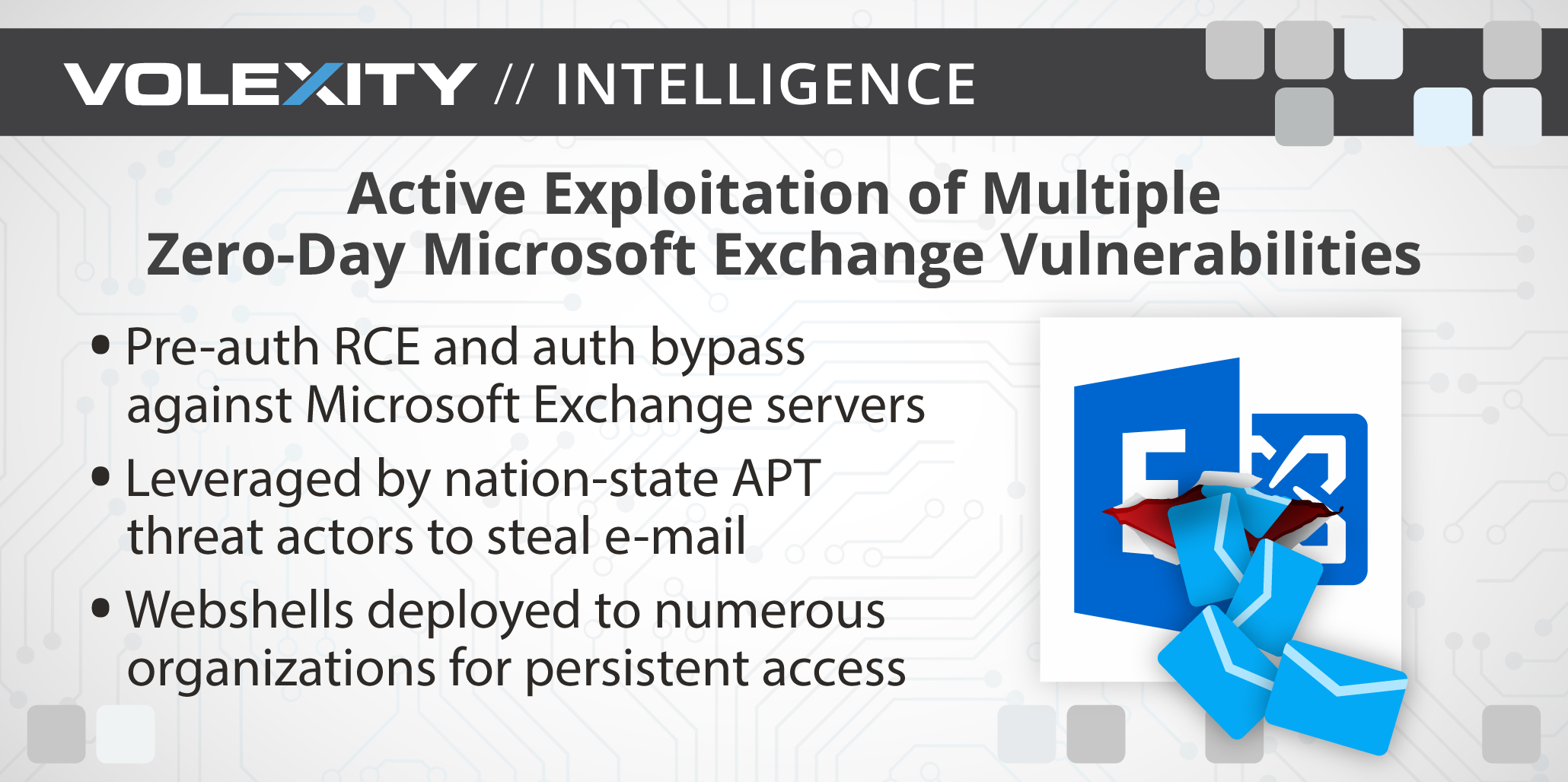
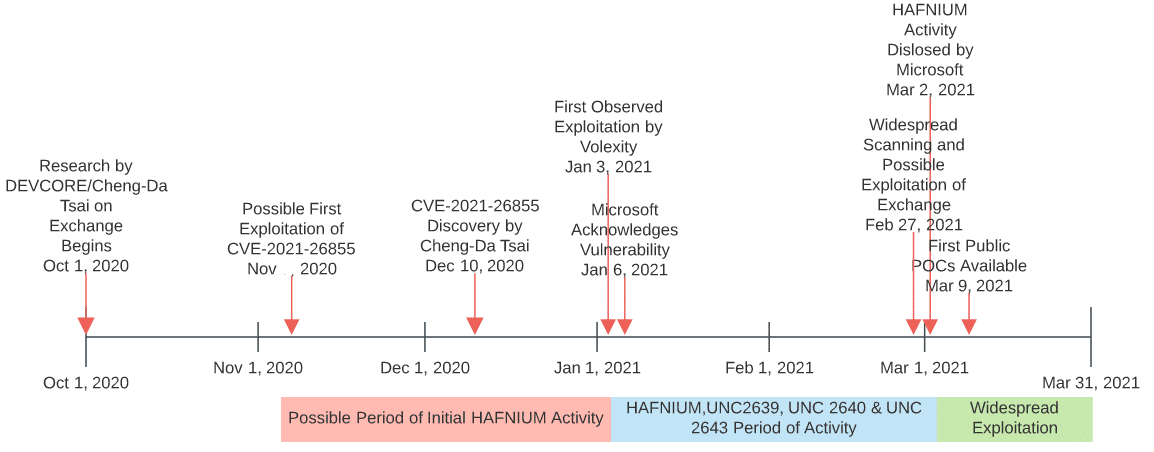
[UPDATE] March 8, 2021 – Since original publication of this blog, Volexity has now observed that cyber espionage operations using the SSRF vulnerability CVE-2021-26855 started occurring on January 3, 2021, three days earlier than initially posted. Volexity is seeing active in-the-wild exploitation of multiple Microsoft Exchange vulnerabilities used to steal e-mail and compromise networks. These attacks appear to have started as early as January 6, 2021. In January 2021, through its Network Security Monitoring service, Volexity detected anomalous activity from two of its customers' Microsoft Exchange servers. Volexity identified a large amount of data being sent to IP addresses it believed were not tied to legitimate users. A closer inspection of the IIS logs from the Exchange servers revealed rather alarming results. The logs showed inbound POST requests to valid files associated with images, JavaScript, cascading style sheets, and fonts used by Outlook Web Access (OWA). It was initially suspected the […]
Examining Exchange Exploitation and its Lessons for Defenders - DomainTools

Detecting Microsoft Exchange Vulnerabilities - 0 + 8 Days Later…
Microsoft Exchange exploitation: how to detect, mitigate, and stay calm
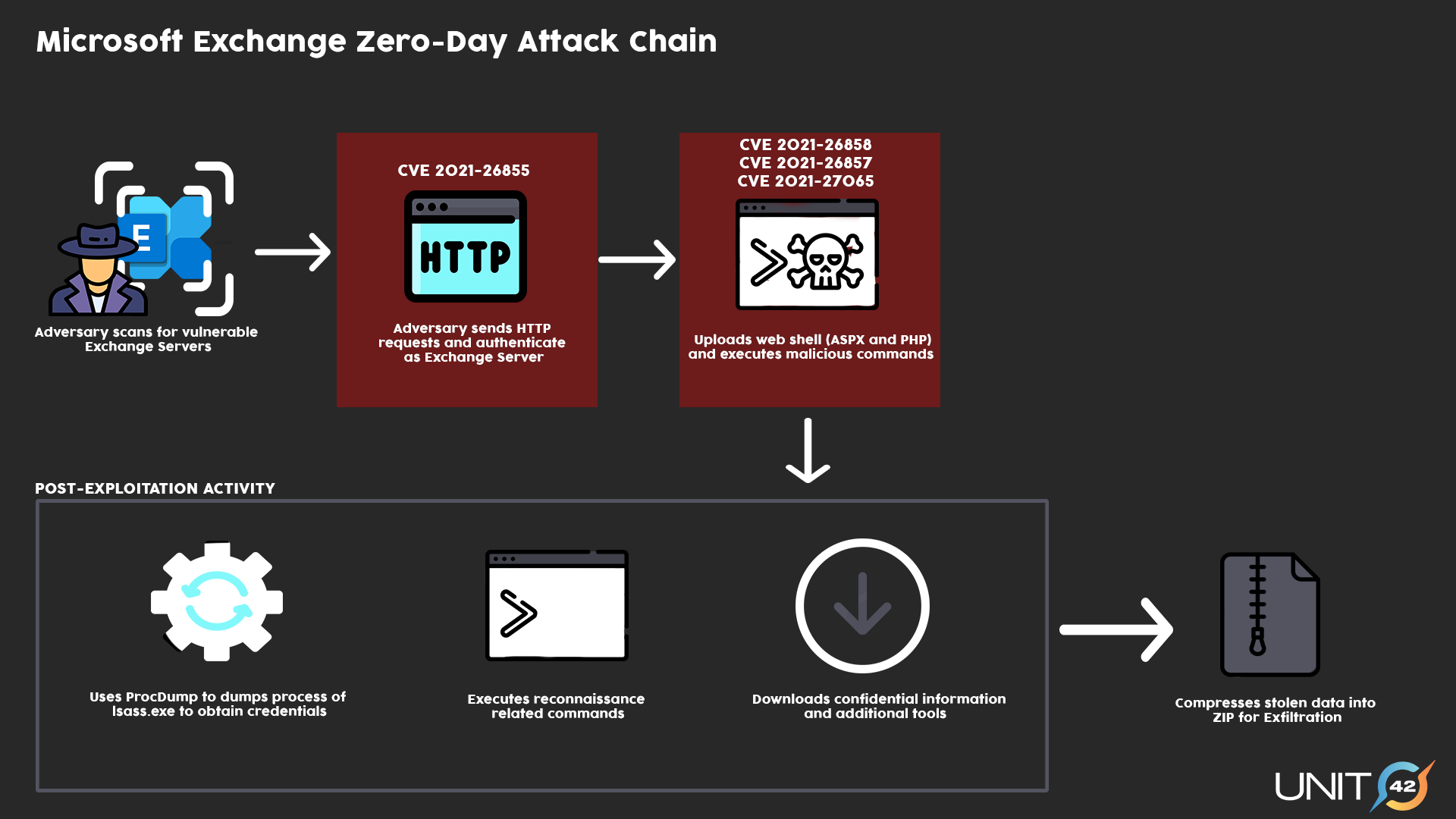
Threat Assessment: Active Exploitation of Four Zero-Day Vulnerabilities in Microsoft Exchange Server
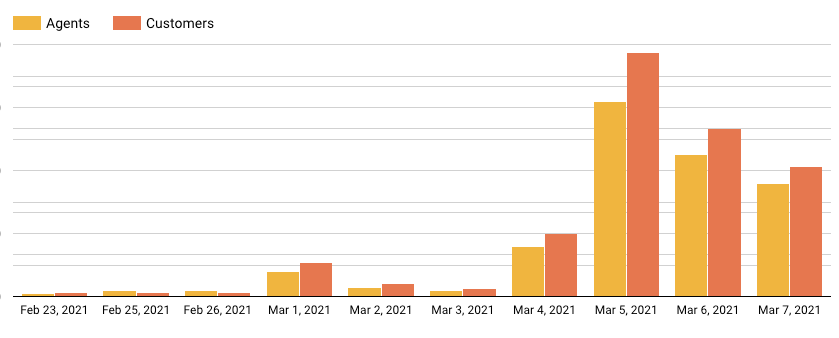
Busted by XDR: Detecting Microsoft Exchange Post-Exploit Activity in February - Palo Alto Networks Blog
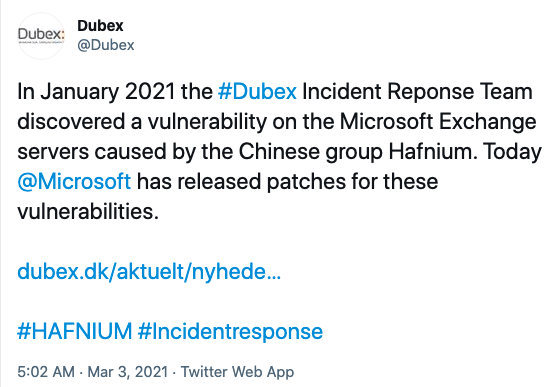
Microsoft Exchange Server Attack Timeline: Discoveries and Mitigations

Detecting Microsoft Exchange Vulnerabilities - 0 + 8 Days Later…
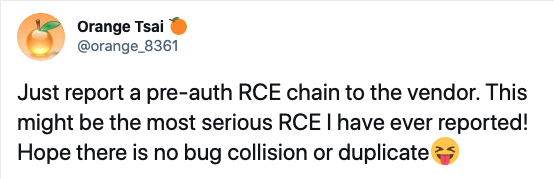
Microsoft Exchange Server Attack Timeline: Discoveries and Mitigations

Microsoft Exchange Faces New Security Threats: Unpatched Zero-Day Vulnerabilities Expose Critical Risks
Tactics, Techniques, and Procedures (TTPs) Used by HAFNIUM to Target Microsoft Exchange Servers
Tactics, Techniques, and Procedures (TTPs) Used by HAFNIUM to Target Microsoft Exchange Servers
Recomendado para você
-
 Counter-Strike: Condition Zero PC Back cover23 dezembro 2024
Counter-Strike: Condition Zero PC Back cover23 dezembro 2024 -
 Best Counter-Strike: Condition Zero Posts - Reddit23 dezembro 2024
Best Counter-Strike: Condition Zero Posts - Reddit23 dezembro 2024 -
CS:CZ] Unable to connect to server · Issue #1946 · ValveSoftware23 dezembro 2024
-
 COUNTER-STRIKE: CONDITION ZERO - 1ST TIME PLAYING IN 15 YEARS23 dezembro 2024
COUNTER-STRIKE: CONDITION ZERO - 1ST TIME PLAYING IN 15 YEARS23 dezembro 2024 -
 Counter Strike Portable, Counter-Strike: Condition Zero, Counter23 dezembro 2024
Counter Strike Portable, Counter-Strike: Condition Zero, Counter23 dezembro 2024 -
 Snow themed ST6, Urban23 dezembro 2024
Snow themed ST6, Urban23 dezembro 2024 -
 Condition Zero Mission Pack - Colaboratory23 dezembro 2024
Condition Zero Mission Pack - Colaboratory23 dezembro 2024 -
 Condition Zero MP5-SD smgs in Counter-Strike 223 dezembro 2024
Condition Zero MP5-SD smgs in Counter-Strike 223 dezembro 2024 -
 Condition Zero Servers - Colaboratory23 dezembro 2024
Condition Zero Servers - Colaboratory23 dezembro 2024 -
Steam Community :: Screenshot23 dezembro 2024
você pode gostar
-
 Anime meme : r/dankmemes23 dezembro 2024
Anime meme : r/dankmemes23 dezembro 2024 -
 Progress Bar with Roblox Rainbow Friends Cyan - Progress Bar for23 dezembro 2024
Progress Bar with Roblox Rainbow Friends Cyan - Progress Bar for23 dezembro 2024 -
 Como corrigir o erro de login rápido do Roblox23 dezembro 2024
Como corrigir o erro de login rápido do Roblox23 dezembro 2024 -
 Descubra o significado da música Bohemian Rhapsody, do Queen23 dezembro 2024
Descubra o significado da música Bohemian Rhapsody, do Queen23 dezembro 2024 -
 Jogos de Colorir Online – Joga Grátis23 dezembro 2024
Jogos de Colorir Online – Joga Grátis23 dezembro 2024 -
 PlayStation Plus review: Premium, Extra and Essential23 dezembro 2024
PlayStation Plus review: Premium, Extra and Essential23 dezembro 2024 -
Spartan Tattoo by Kamil Mocet on Vimeo23 dezembro 2024
-
 Countryhumans: Anime Adventure23 dezembro 2024
Countryhumans: Anime Adventure23 dezembro 2024 -
 Cardboard People Lightning McQueen Life Size Cardboard Cutout Standup - Disney Pixar's Cars 3 (2017 Film)23 dezembro 2024
Cardboard People Lightning McQueen Life Size Cardboard Cutout Standup - Disney Pixar's Cars 3 (2017 Film)23 dezembro 2024 -
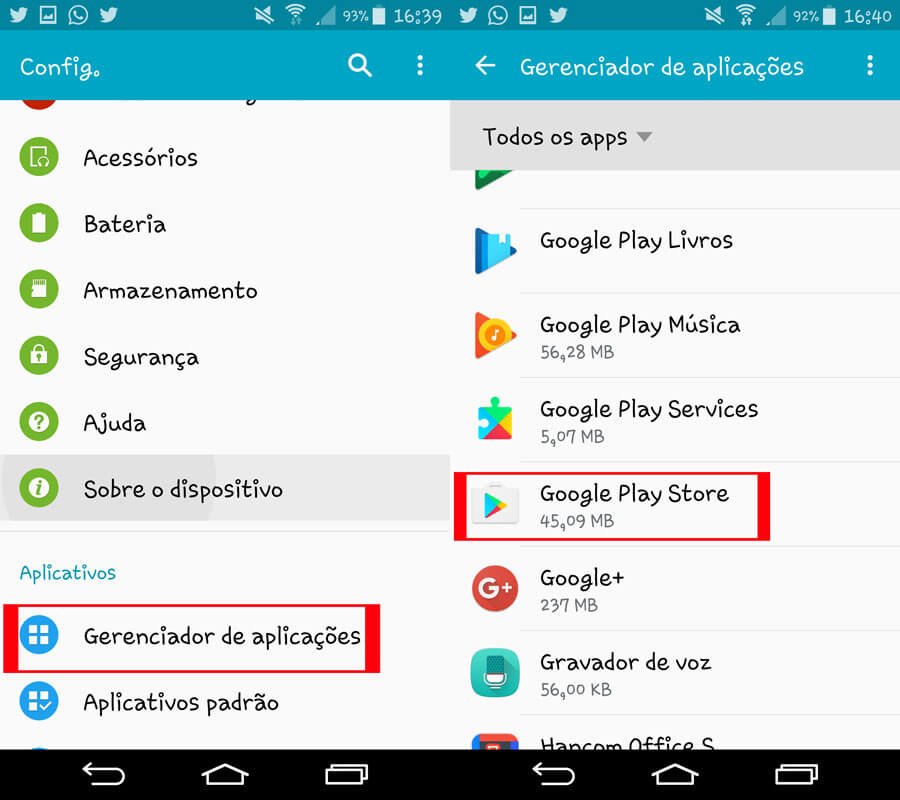 Como desinstalar a loja do Play Store de seu Android23 dezembro 2024
Como desinstalar a loja do Play Store de seu Android23 dezembro 2024