Trend Micro Research on X: Scenario 2: If the user is not logged
Por um escritor misterioso
Last updated 31 dezembro 2024
How to generate various logs in Trend Micro for Windows
Secure Endpoint Best Practices Guide - Cisco
Trend Micro Internet Security Data Collection Notice
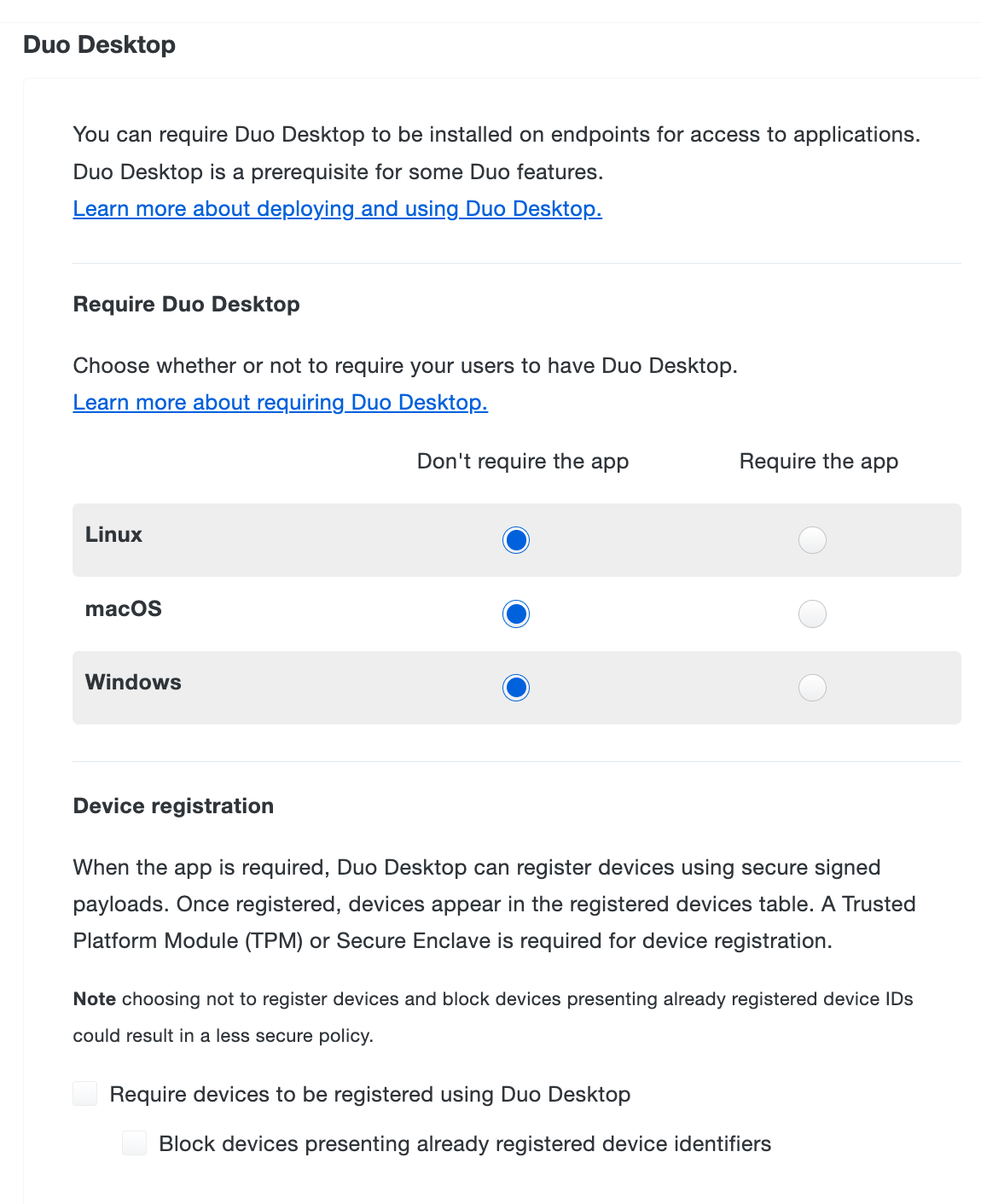
Duo Administration - Policy & Control
Empty list for endpoint and domain nodes after agent deployment - OfficeScan
Evaluate Microsoft Exchange Online modules - Cloud App Security

What is EAP-TLS?

Duo Administration - Policy & Control
Data Collection Disclosure - Trend Micro Portable Security 2.0
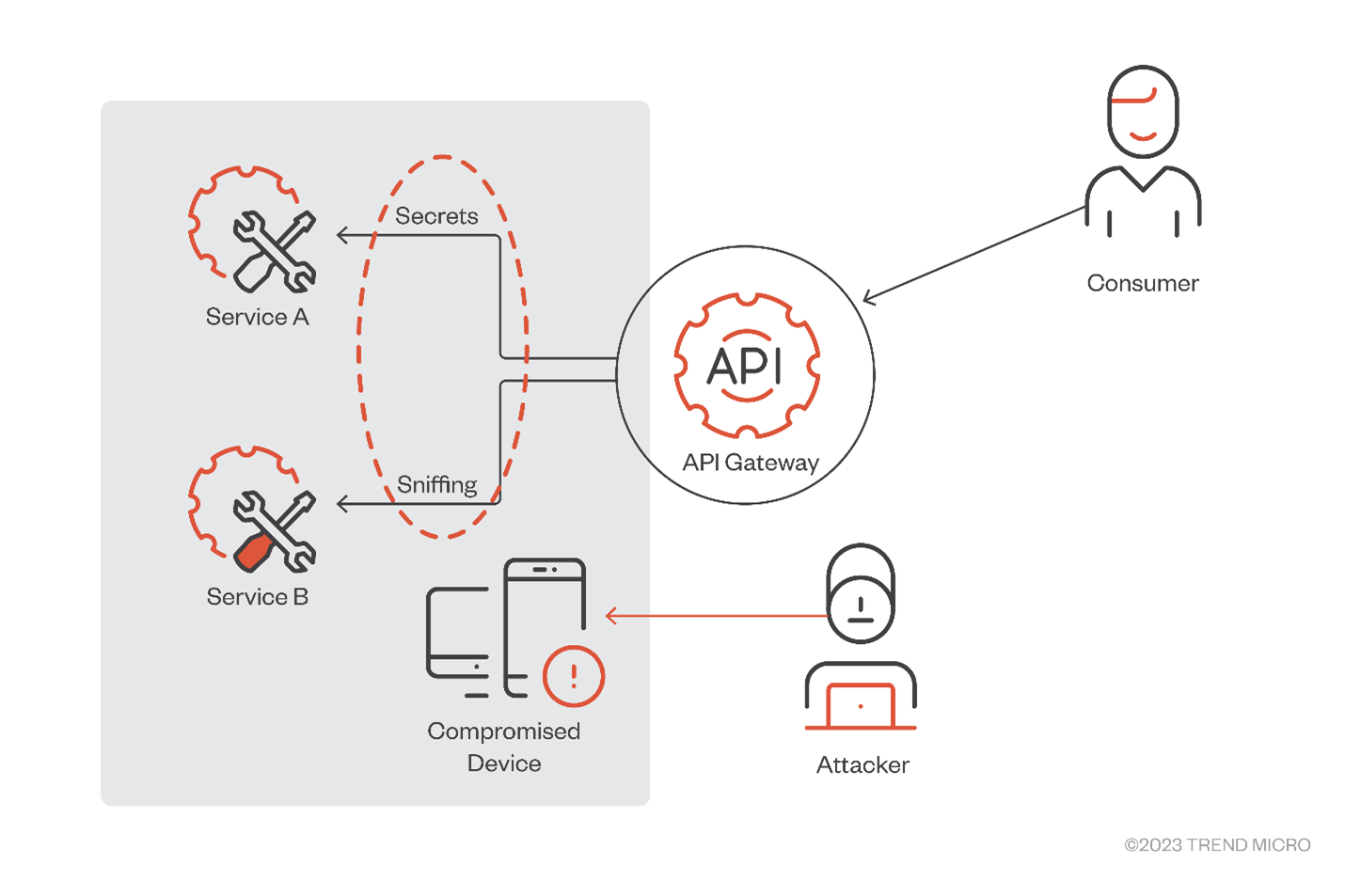
Threat Modeling API Gateways: A New Target for Threat Actors? - Noticias de seguridad - Trend Micro ES

Trend Micro Antivirus+ Security Review
Collecting debug logs - Portable Security 3.0
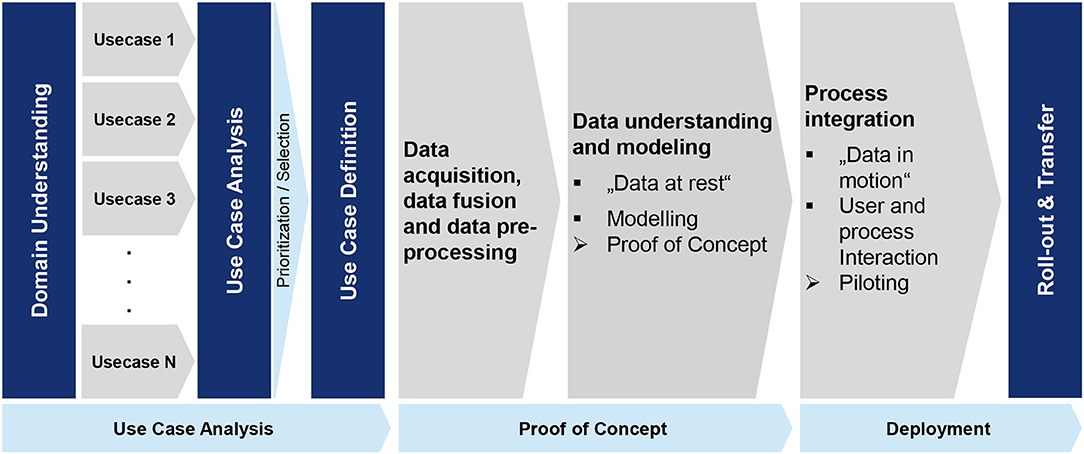
Frontiers Implementation and Transfer of Predictive Analytics for Smart Maintenance: A Case Study
Passed a potential security risk' in Virus/Malware Logs

Wi-Fi Spoofing: A Major Threat to Network Security - Cloud RADIUS
Recomendado para você
-
 How to Login to Your Facebook Business Profile from Anywhere31 dezembro 2024
How to Login to Your Facebook Business Profile from Anywhere31 dezembro 2024 -
Is it possible to get past login history report on Facebook? - Quora31 dezembro 2024
-
 Facebook31 dezembro 2024
Facebook31 dezembro 2024 -
 Facebook Login Home Page Screen Editorial Stock Photo31 dezembro 2024
Facebook Login Home Page Screen Editorial Stock Photo31 dezembro 2024 -
 How to Integrate Facebook Login with WordPress31 dezembro 2024
How to Integrate Facebook Login with WordPress31 dezembro 2024 -
 Facebook Login Form31 dezembro 2024
Facebook Login Form31 dezembro 2024 -
 Simplify Your Facebook Login Screen · Nono Martínez Alonso31 dezembro 2024
Simplify Your Facebook Login Screen · Nono Martínez Alonso31 dezembro 2024 -
 Facebook login page Stock Photo - Alamy31 dezembro 2024
Facebook login page Stock Photo - Alamy31 dezembro 2024 -
 Facebook Login Sign Up New Account, Login FB Account Now31 dezembro 2024
Facebook Login Sign Up New Account, Login FB Account Now31 dezembro 2024 -
 Facebook Style login page and Registration page using HTML and CSS31 dezembro 2024
Facebook Style login page and Registration page using HTML and CSS31 dezembro 2024
você pode gostar
-
 Listen to Don't Be Shy by Tiësto in Música Tecno House Mix 202331 dezembro 2024
Listen to Don't Be Shy by Tiësto in Música Tecno House Mix 202331 dezembro 2024 -
 NOITE DE LUTA do Xadrez BRASILEIRO - Krikor Mekhitarian Vs Lucas31 dezembro 2024
NOITE DE LUTA do Xadrez BRASILEIRO - Krikor Mekhitarian Vs Lucas31 dezembro 2024 -
 Conheça 10 curiosidades dos jogos de The Witcher - Aficionados31 dezembro 2024
Conheça 10 curiosidades dos jogos de The Witcher - Aficionados31 dezembro 2024 -
 Ace Combat 7: Skies Unknown - Mission 11: Fleet Destruction31 dezembro 2024
Ace Combat 7: Skies Unknown - Mission 11: Fleet Destruction31 dezembro 2024 -
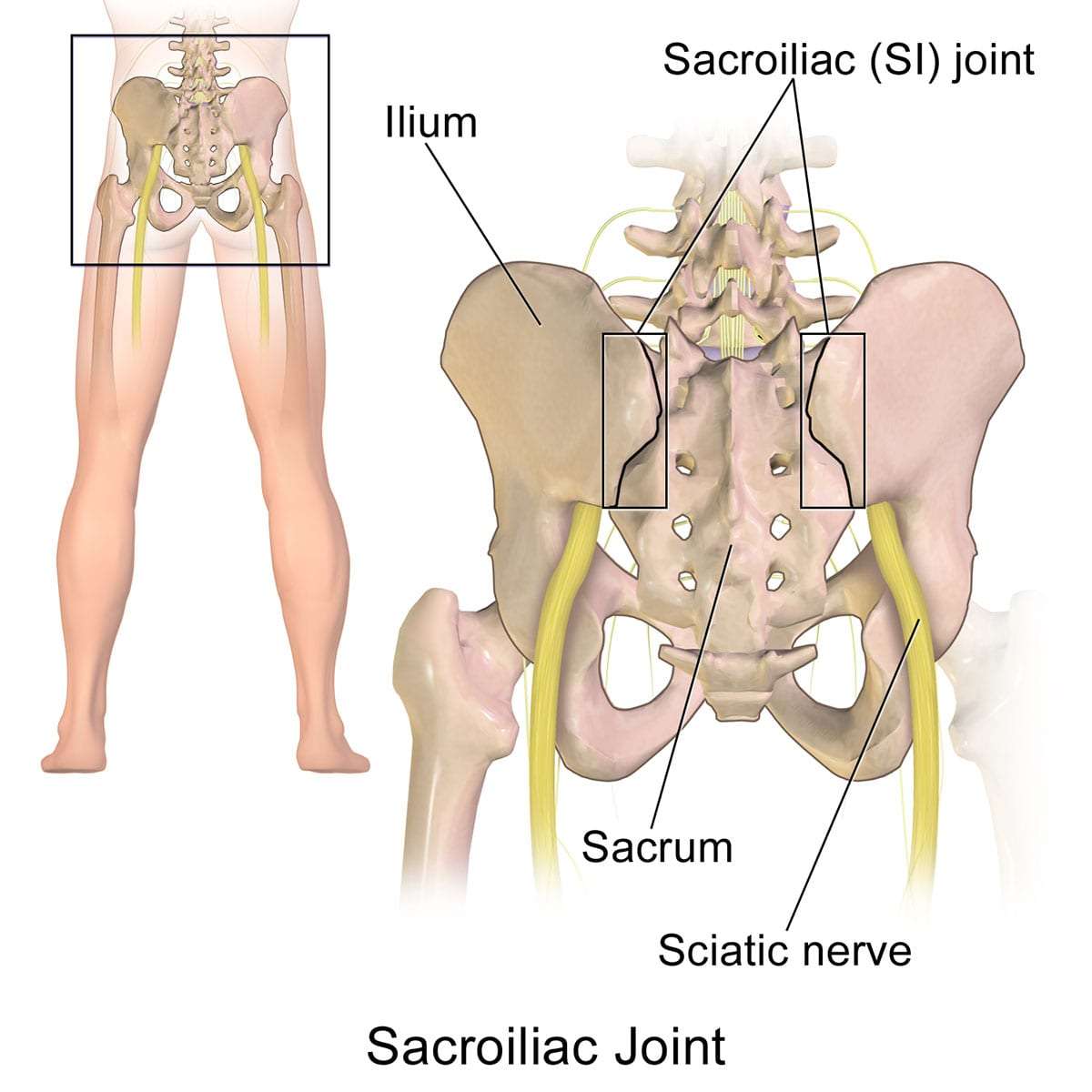 Sacroiliac Joint Pain Novus Spine & Pain Clinic, Lakeland, Florida31 dezembro 2024
Sacroiliac Joint Pain Novus Spine & Pain Clinic, Lakeland, Florida31 dezembro 2024 -
 Sage Valorant Art 4K Wallpaper #7.170931 dezembro 2024
Sage Valorant Art 4K Wallpaper #7.170931 dezembro 2024 -
 .com: 30cm/11.8inch Tails Doll Plush, Orange Tails.EXE Plush Toy, Blood Sonic.exe Plush Toy, Evil Sonic Stuffed Plush Doll, Dark Sonic Plush, from Popular Sonic Games, Gift for Fans for Boys & Girls31 dezembro 2024
.com: 30cm/11.8inch Tails Doll Plush, Orange Tails.EXE Plush Toy, Blood Sonic.exe Plush Toy, Evil Sonic Stuffed Plush Doll, Dark Sonic Plush, from Popular Sonic Games, Gift for Fans for Boys & Girls31 dezembro 2024 -
Israel clamando ao Senhor Jesus #noticias #israel #guerreiros31 dezembro 2024
-
 15 dos Melhores Jogos Indie e Comparar Preços31 dezembro 2024
15 dos Melhores Jogos Indie e Comparar Preços31 dezembro 2024 -
 Pizza: More than 60 Recipes for Delicious Homemade Pizza: Morgan, Diane, Gemignani, Tony, Peterson, Scott: 9780811845540: : Books31 dezembro 2024
Pizza: More than 60 Recipes for Delicious Homemade Pizza: Morgan, Diane, Gemignani, Tony, Peterson, Scott: 9780811845540: : Books31 dezembro 2024
